Cybersecurity experts developed an experiment to demonstrate that malicious hackers can launch side channel attacks based on various browsers without using JavaScript. This attack has been tested on multiple platforms, including M1 chip running devices, Apple’s latest release.
This research was developed by specialists from Ben-Gurion Universities in Israel, the University of Michigan in the U.S. and the University of Adelaide, Australia.
This experiment focuses primarily on Prime+Probe, a cache side channel attack method that can detect which cache sets the target user accesses, using this information to infer potentially sensitive information.
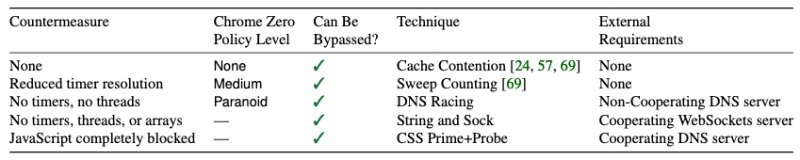
The report mentions that, under normal conditions, the deployment of such attacks would require JavaScript code execution and complex time measurement. Currently the vast majority of web browser developers have implemented the necessary measures to prevent these attacks, even through the complete suppression of JavaScript execution.
The method developed by these experts consists of a sequence of attacks in which the dependence of JavaScript functions is progressively reduced, allowing the attack to be based on HTML and CSS completely: “This has allowed us to dodge any existing countermeasures”, the researchers add.
The attack appears to have already been tested with varying degrees of success that depend on the abused architecture and security measures implemented against reinforced environments (such as Google Zero, Tor, and DeterFox) on all kinds of devices operating Intel, AMD, Apple, and Samsung chips.
Researchers have already notified all affected developers, although the responses they have received have not been entirely satisfactory: “Apple mentioned to us that they are not concerned about public disclosure of this attack.”
For experts, the fact that a large technology company takes this stance on a considerable security risk is somewhat daunting: “We demonstrate that advanced variants of the cache containment attack allow the deployment of a Prime+Probe condition through the browser in limited situations. Cache attacks cannot be prevented by reducing timer resolution, eliminating timers, threads, or arrays, or even completely disabling script support,” concludes the report.
What are your thoughts about this security report? Is the company forced to improve the potential attack vector? Are you willing to learn more about it? To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











