Web browsers are one of the most widely used tools by people around the world, whether or not they have hacking skills or minimal computer skills. However, we may not be making the most of this technology, as most users are unaware that by simply adding a few extensions our conventional browsers can become sophisticated cybersecurity utilities.
This time, ethical hacking experts from the International Institute of Cyber Security (IICS) will show you a list with the 11 best extensions to turn your web browser into a powerful hacking tool.
As usual, it should be remembered that this article was prepared for academic purposes only, so the misuse that may occur of these tools is not the responsibility of IICS.
IP ADDRESS AND DOMAIN INFORMATION
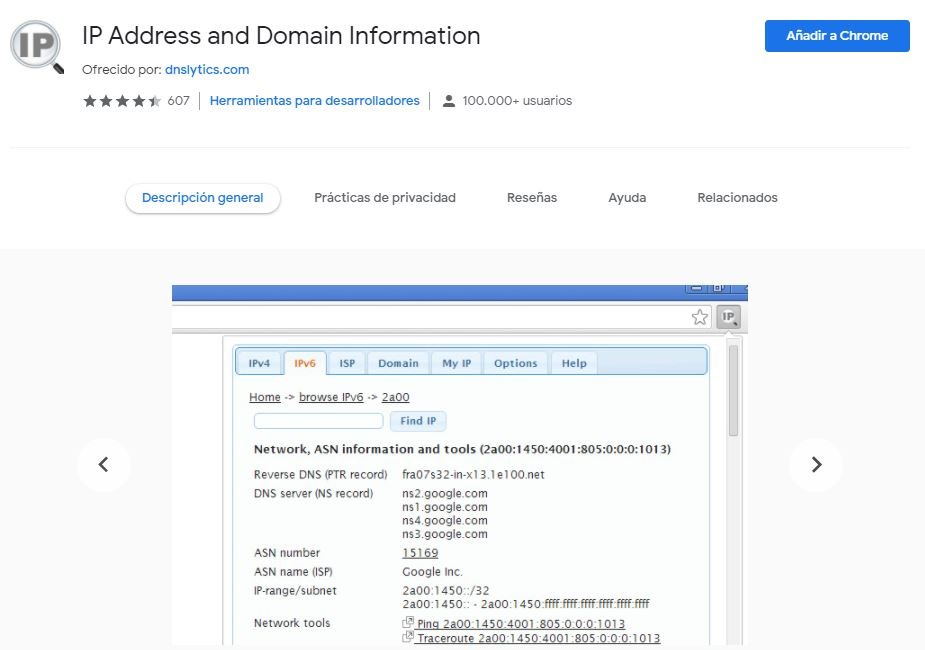
The first stage in any ethical hacking task is recognition. To do this, the TCPIPutils.com will help us to obtain data such as IP address, hosting provider, among other relevant information. According to ethical hacking experts, you can install this extension from the official Chrome store.
SHODAN
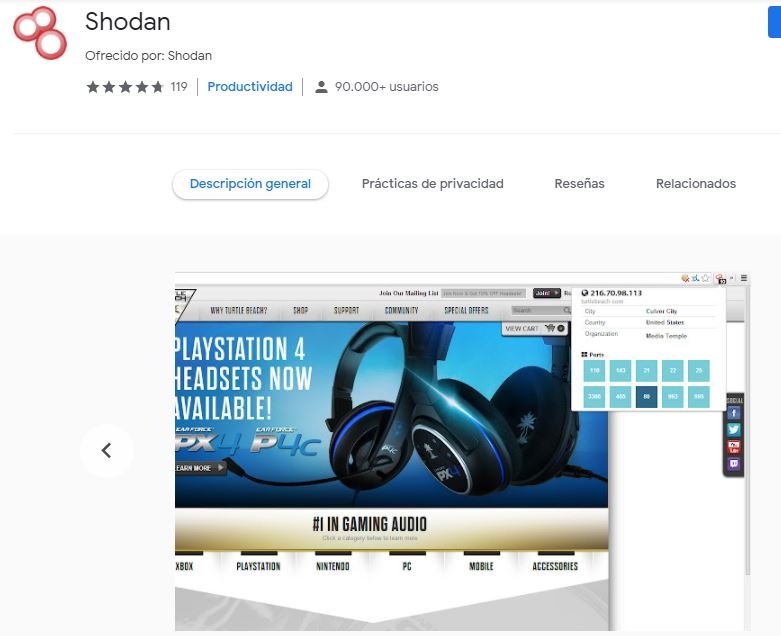
After collecting as much information as possible from the target domain, start the analysis using the Shodan search engine, which will show the researcher a list of open ports and services, among other data. To get started, you can try the free version of the tool available in Chrome and on the official website.
PORT SCANNER
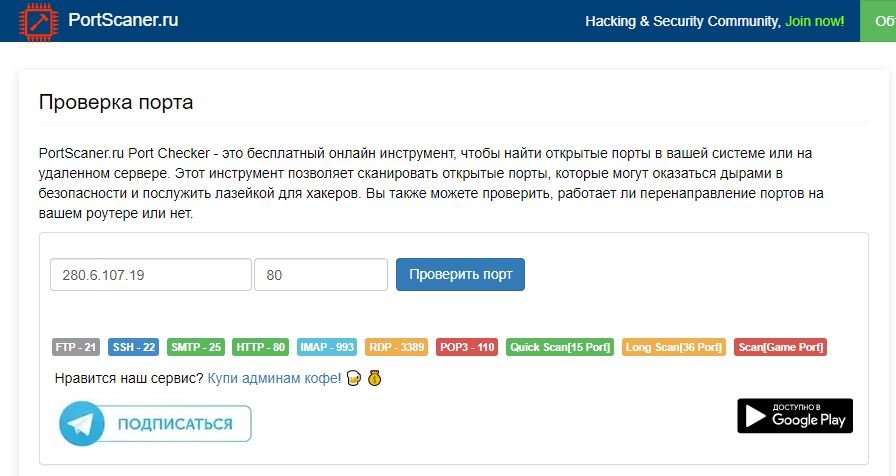
As the name suggests, Port Scanner will scan the open ports on a remote host to know their current state, Users can rake a completely different server, in addition to manually configuring the TCP port range in this tool, as mentioned by ethical hacking specialists.
PROXY SWITCHYOMEGA
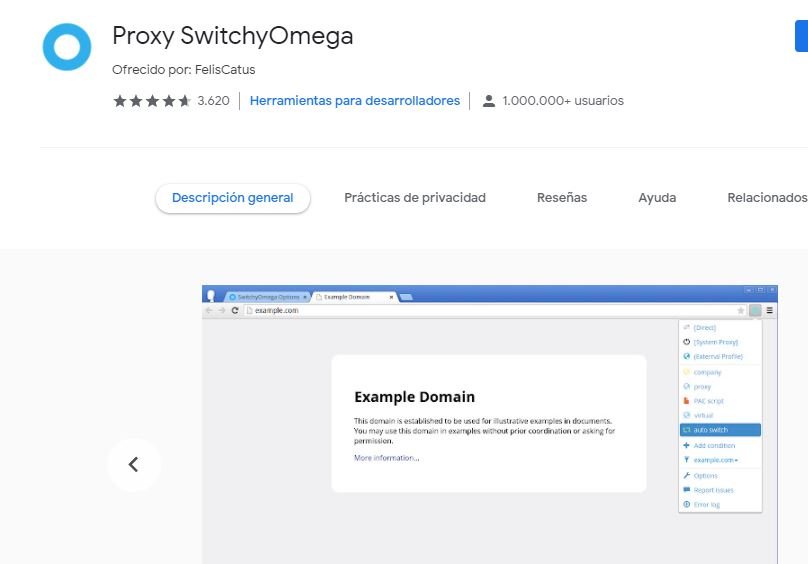
Port scanning sometimes doesn’t always turn out as expected, as multiple servers have sophisticated firewalls and other attack prevention systems. Anonymous proxies help users prevent intruders from reaching your website; one of the best tools, Proxy SwitchyOmega (also known as Proxy SwitchySharp) offers a simple and convenient way to enable the best possible protection against meddlers.
EDITTHISCOOKIE
All current websites use temporary identifiers (cookies) to track the activity of their users. The developers of the EditThisCookie extension created a tool for easy cookie management, allowing users to clearly identify website tracking purposes.
THE EXPLOIT DATABASE
After the information collection work, it’s time to get down to business and find vulnerabilities at the selected site. This extension provides convenient access to an Offensive Security file exploit database. By default, updates are checked every five minutes and all new vulnerabilities are sorted by date, type, author, and description, mentioned by ethical hacking experts.
GOOGLE HACKING DATABASE (GHDB)
This is a Chrome app that contains examples of sneaky queries that allow you to quickly find network computers and web platforms with known vulnerabilities through Google.
A separate section includes typical queries for network cameras, video surveillance systems, and printers. In addition, built-in account search procedures and specific errors are also added.
XSS RAYS
This tool allows ethical hacking experts to perform penetration testing using inter-site scripting (XSS) attacks, including vulnerability scanners, scrip analysis, form injectors, and reverse engineering tools.
This tool can perform advanced keyword searches on HTML pages and external scripts and handlers. XSS Rays is available for free download.
HPP FINDER
This extension performs a thorough review of the website in the current tab to search for items in the web application affected by known failures. HPP Finder uses a method discovered more than five years ago, however, the vulnerability found touches the fundamental flaws of RFC3986 and therefore remains relevant. It is possible to correct only your manifestation in a specific application.
REQUEST MAKER
This extension allows you to send normal or modified requests to a particular server in order to parse response packets. According to ethical hacking specialists, Request Maker is launched from the Add-ons menu by clicking on its Options menu, as well as including auxiliary features.
IMACROS FOR CHROME
This extension saves you time by automating routine tasks. For example, when performing a penetration test, you often need to repeat the same actions on different pages of the site. Using iMacros you can record and play them with default settings, as typical tasks are already in the sample database.
PANIC BUTTON PLUS
The time may come when you need to delete all log of your hacking activities on your device, which could be really easy using the right tool. Panic Button will help you get rid of all these records with just a few clicks; If at a time you need to delete this information, you can assign an easy-to-remember command to prevent other users from accessing your ethical hacking activity.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











