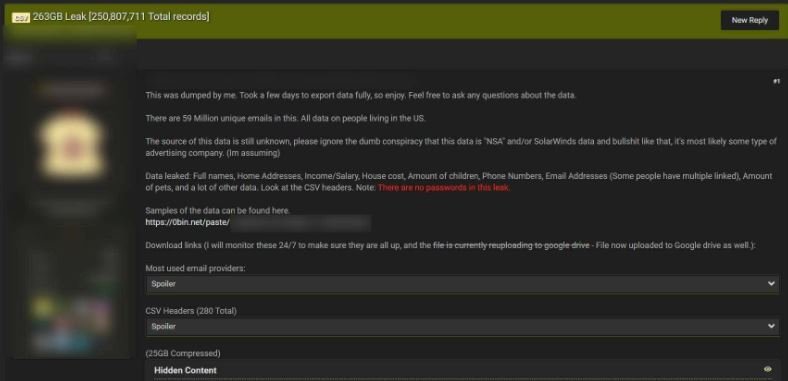
Just a few days ago a hacker identified as Pompompurin announced the leak of a database with more than 250 million confidential records belonging to U.S. citizens. This database was leaked into a hacking forum and is composed of 263 GB of personal records, including more than a thousand CSV files, each with about 200 thousand listings.
The cybersecurity community is unclear where this information comes from, although the leak apparently originates from an open Apache SOLR server hosted on Amazon Web Services (AWS). Experts also mention that the data is available at three different IP addresses that hackers accessed before being deleted. On the other hand, the Hackread.com confirmed that the leak includes information that could be of great interest to many cybercriminal groups.
Early reports indicate that the database includes details such as:
- Full names
- Phone numbers
- Dates of birth
- Email addresses
- Marital status
- Gender
- Home
- House value or rental amount
- Year of construction of the house
- ZIP codes
- Creditworthiness
- Geolocation
- Political affiliation
- Number of vehicles owned
- Salary and income details
- Number of children and pets in a home
Although the leak is full of sensitive information, good news is that there is no evidence of exposed passwords.
It has been more than a week since the leak and the database continues to circulate through multiple Russian-speaking hacking forums hosted on dark web and Telegram groups. It took very little time for the incident to take political tints, especially considering the supply chain attack that hit SolarWinds a few months ago.
This is not the first incident to leak information from millions of U.S. citizens. In mid-2017, a marketing company working for the Republican National Committee mistakenly leaked about 200 million individual records. Just a few months later, a data analytics company exposed about 123 million personal records due to incorrect AWS configuration.
So far no malicious campaigns associated with this leak have been identified, although experts recommend users stay on top of any potential attack attempts. These attacks can occur in the form of SMS messages, unsolicited emails and even visits from alleged vendors or government agents. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.