A hacker group claims to have gained access to data from thousands of SIM cards through a complex cyberattack targeting Schepisi Communications, a renowned Australian-based telecommunications company. On its website, this company claims to be associated with telecommunications giant Telstra, providing phone numbers and cloud storage services.
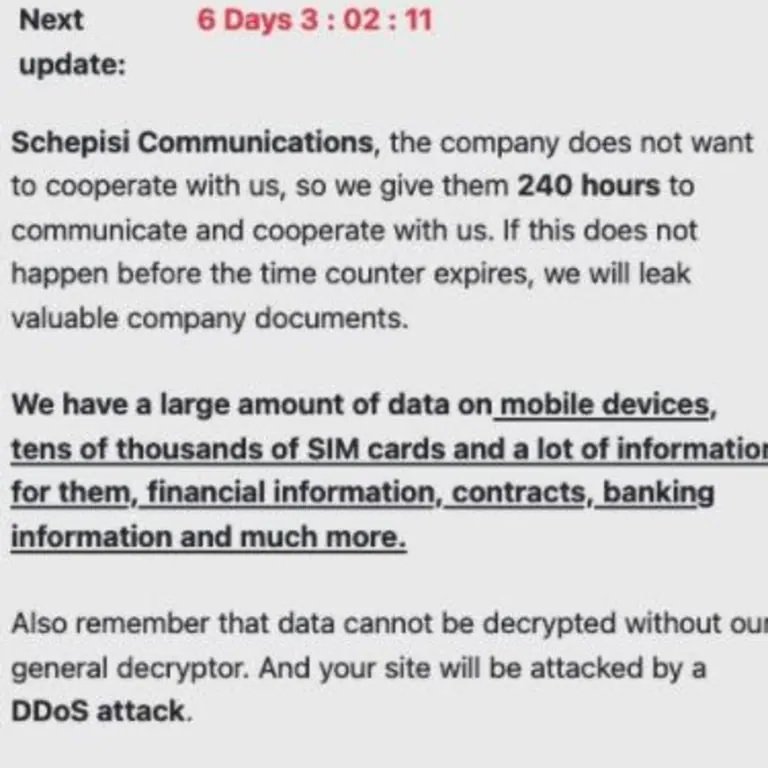
The claims of these hackers appear to be true, as the company’s official platform has been out of service for days. In addition, internal sources mention that company executives have already received a ransom note in which hackers claim to have accessed all kinds of confidential information, including SIM cards, payment details and contracts, among other records.
In this regard, Telstra has already confirmed a cybersecurity incident affecting one of its distributors, without explicitly naming Schepisi Communications: “We have contacted the affected company, so we are aware of access to certain confidential information,” a Telstra spokesperson said. The representative of Tesltra added that the company has strict guidelines established for access to the personal data of its customers for the purposes permitted by law, in addition concluded its message ensuring that the affected systems are not connected to Telstra’s networks.
Moreover, some of the documents exposed on dark web as an extortion method show what appear to be names and phone numbers of some affected customers. The leak also includes information from Schepisi’s business customers, including companies such as Nestlé, some radio stations and financial services companies based in Australia.
Schepisi’s official platforms show that Schepisi offers access and support to Telstra’s services, working primarily with business customers. These services include advice on migrating documents from physical servers to cloud storage units, as well as complementary services.
About hackers, it is not known which ransomware group is behind the attack, although a source close to the investigation mentioned that the ransom note received by Schepisi included a timer that would have expired this weekend. The ransom amount demanded by hackers is also unknown.
Although there is little official information, cybersecurity specialist Brett Callow claims that threat actors employed an attack mechanism identified as “triple edge”, which allowed them to steal data, encrypt compromised information and eventually leave the victim’s website out of service. This is an increasingly common method of attack and it has proven to be more dangerous, as stolen information can be sold on dark web even if victims agree to pay the ransom.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











