Bloodhound is a great visual tool that shows the relationship between multiple Active Directory objects and allows you to quickly evaluate the possibility of compromising relevant information, as well as identify potential security weaknesses. The best thing about this tool is that it is practically ready to use after installation, so no complicated startup configurations are required.
Below, pentesting specialists from the International Institute of Cyber Security (IICS) will show you everything you need to know about using Bloodhound.
Installation
For this step, the factory version of Kali Linux is recommended. Enter the following command:
$ sudo install bloodhound
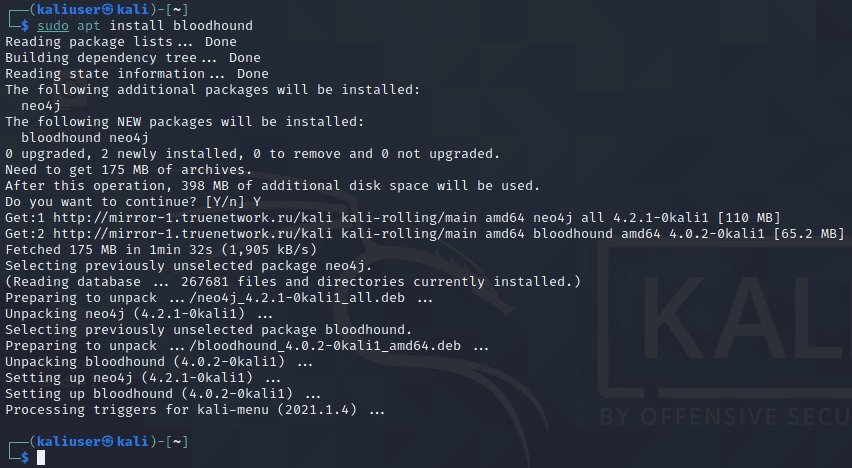
After the installation is complete, start the neo4j console. This step should work perfectly if the system is connected to the Internet and the repositories are registered correctly, as mentioned by pentesting experts:
$ sudo neo4j console
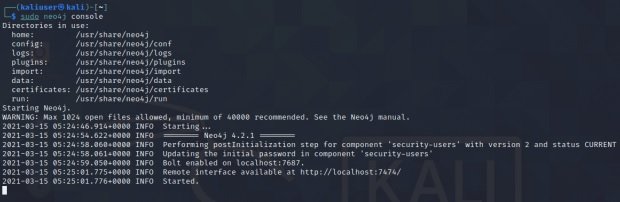
During startup, the following message will appear: “Remote control interface is available at: http://localhost: 7474/”. You can go through the browser available in Kali.
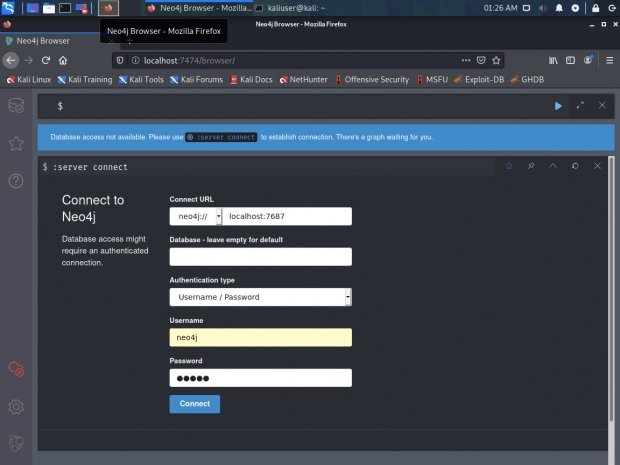
The tool will ask us to specify the username and password when connecting to the database. In this case, pentesting experts use “neo4j: neo4j”. There’s nothing else to do here. Now, in another window, run Bloodhound directly:
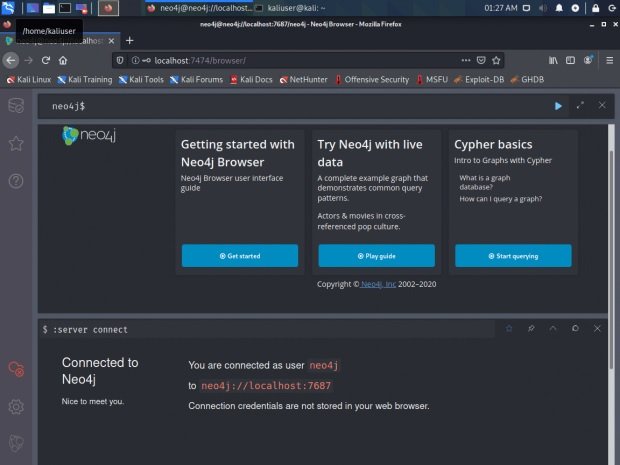
$ bloodhound
Log in and get to the application desktop.
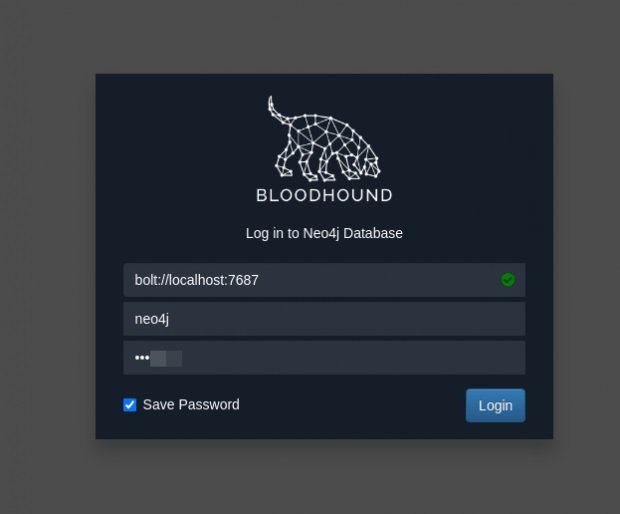
The database is empty. Now we need to load ActiveDirectory data here.
Collect data from a domain
Next we will need a collector and a domain user account, as mentioned by pentesting experts:
- The collector can be downloaded here: https://github.com/BloodHoundAD/BloodHound/tree/master/Collectors
- Take a domain account, whichever will be useful. The methods for obtaining valid accounts are different; as an option, listen to the responder and collect the NetNTLMv2 hash. You can also use SMB.
In this case, the Sharphound collector has been downloaded, which must be executed as a domain user. This can be done from a node that is not included in the scanned domain.
Open the command prompt as an administrator and run the following command:
runas /netonly /user:domain\login cmd.exe
User password required
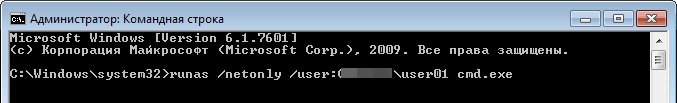
If the credentials are correct, we will see a new command line session, the title of which will be the name of our user:
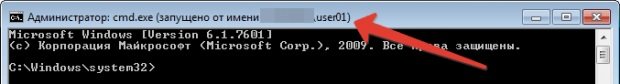
Later, in this session we will launch our collector specifying the domain name. It is important to note that we must have the DNS of this domain registered in order to resolve it by name.
sharpdound.exe -d domain name
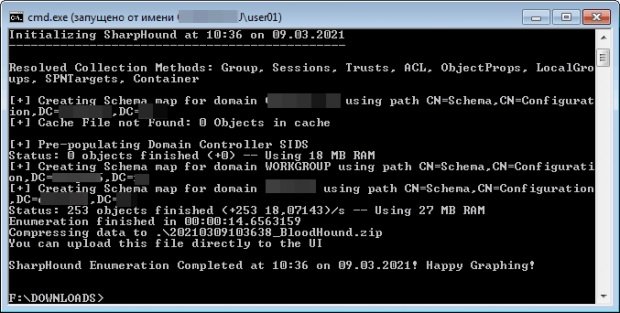
When the data collection is complete, we will see the file with the corresponding name, indicated in the program output. This file is what we need to import to Bloodhound, pentesting specialists mention.
What information will we get?
Click the “Load Data” button in Bloodhound
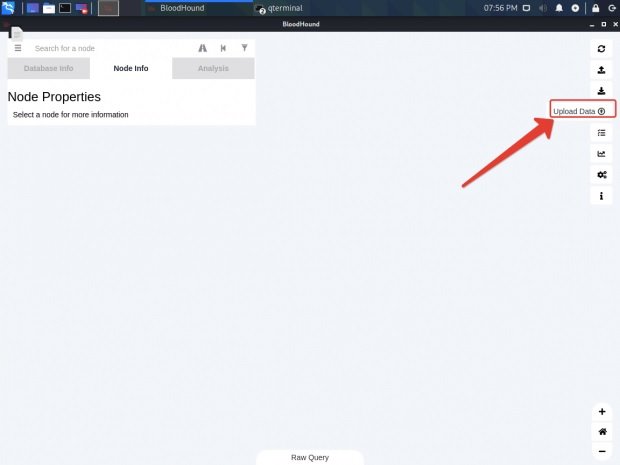
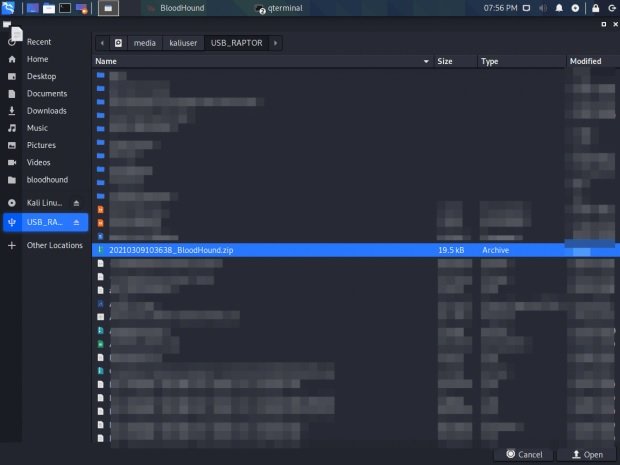
Select the file created in the previous step and open it.
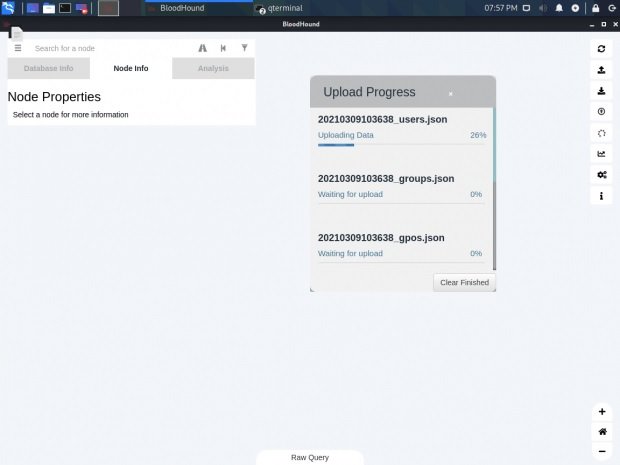
Next we will have to import the process.
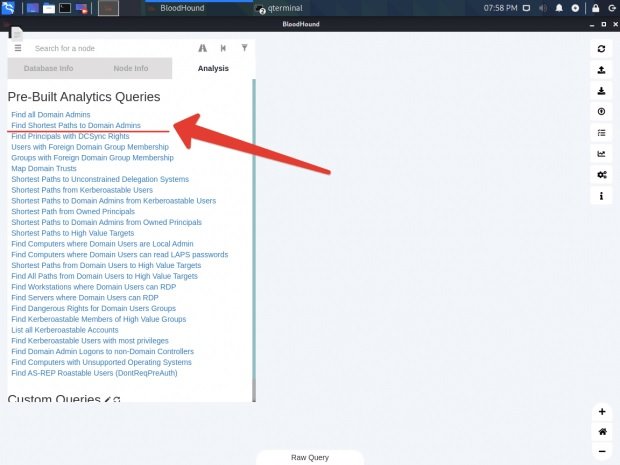
When the import is complete, you can go to the “Analysis” tab and select the ready-made templates. Pentesting experts recommend dealing with “Finding shorter paths for domain administrators”; find the shortest path for the domain administrator.
The corresponding chart was created automatically. At a closer inspection, you may find something interesting. For example, a user **** USER9, who is a member of the Domain Admins group, was immediately discovered. In addition, it is not yet clear whether this is misconfigured or deliberately left, although this is a clear sample of how the tool works.
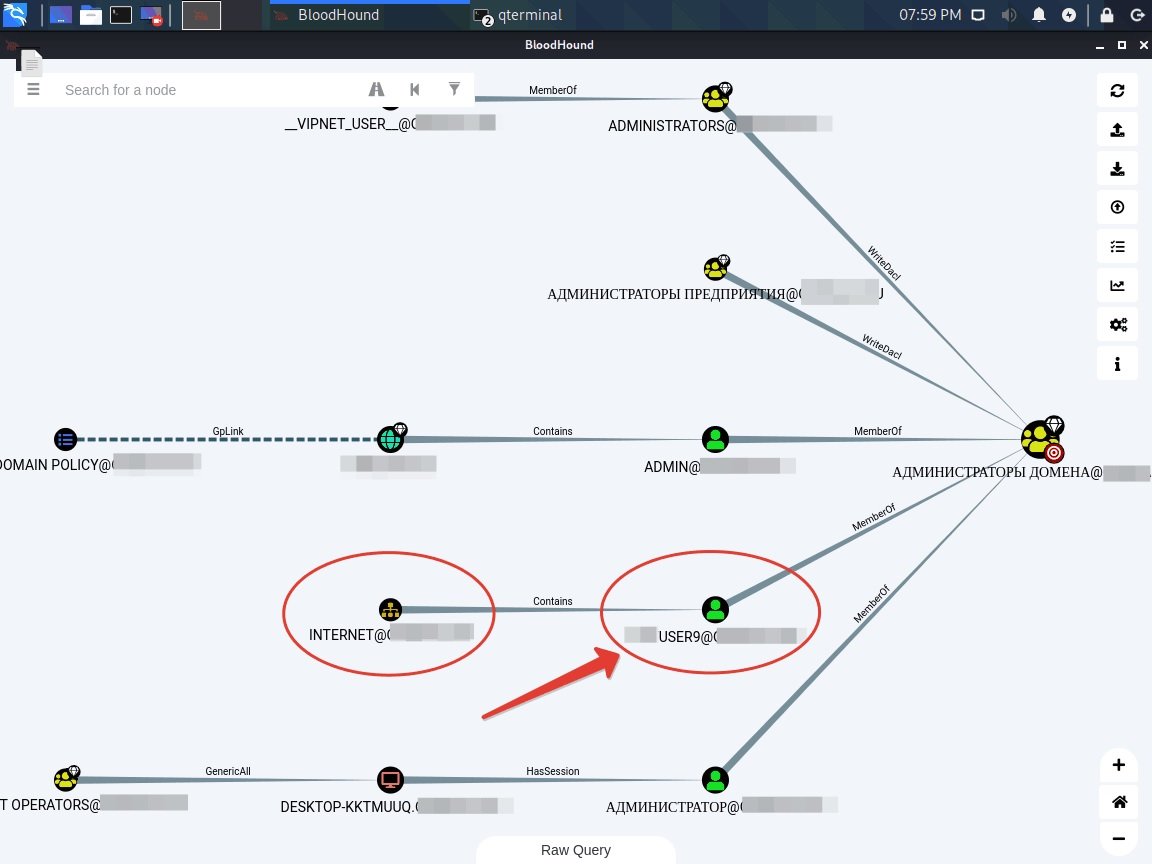
Bloodhound has many scripts and analysis prepared, mentioned by pentesting experts. You can create your own charts and mark such important nodes to complete the goal of this tutorial: capturing the target domain.
This is a tool that can be very useful to both administrators and pentesting experts; Remember that this article was prepared for academic purposes, so IICS is not responsible for the misuse that may be given to Bloodhound. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











