FireEye cybersecurity specialists published details of a recent research related to the DarkSide ransomware operation. This week experts released reports on five groups allegedly associated with this ransomware-as-a-service (RaaS) platform, responsible for some of the most devastating attacks recently detected.
Among the most recent victims of this encryption malware is Colonial Pipeline, one of the most important pipeline operating companies in the United States. The company’s IT services continue to work on restoring their systems.
While the creators of this ransomware variant claim to be an apolitical group and act only with financial motivations, research agencies in multiple countries have already begun to show greater interest in their potential links to nationally sponsored threat actor groups.
FireEye researchers mention detecting at least five DarkSide-affiliated hacking groups. These cybercriminal groups have access to custom variants of the ransomware, plus they must share with the developers the profits generated by each attack. Amounts vary depending on the gains made by the attackers.
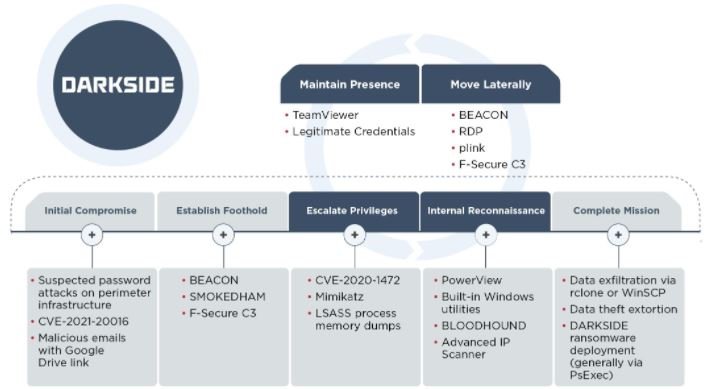
Experts shared some details of three of the groups associated with DarkSide, identified as UNC2628, UNC2659 and UNC2465. Down below is a list of some details mentioned about these hacking groups.
UNC2628: Active at least since February 2021, this hacking group is characterized by the rapid implementation of the attack, completing a successful infection in less than a week. Operators in this group use brute force attacks and abuse of authentication mechanisms to gain initial access to affected systems. Hackers can also access compromised platforms by purchasing login credentials on dark web platforms.
UNC2659: Attacks in this group usually take longer as they go from initial access to malware deployment through the infected system in about 10 days.
Apparently, the attacks of this group are based on the exploitation of CVE-2021-20016, a flaw in SonicWall SMA100 SSL VPN. Hackers can also compromise TeamViewer deployments to generate persistence on the target system.
UNC2465: This hacking group has remained active at least since April 2019 and its attacks rely on sending phishing emails to deliver malware via the backdoor identified as Smokedham.NET. According to FireEye’s report, hackers can remain on the affected system for up to eight months before running the ransomware.
Hackers also use backdoor to execute arbitrary commands, record keystrokes and even take screenshots, as well as use the NGROK utility to bypass firewalls and expose remote desktop service ports.
Finally, a joint report by Sophos and FireEye notes that, on average, hackers using DarkSide allow 45 days to pass between initial access and execution of the ransomware, displaying a very similar ransom note in each particular case.
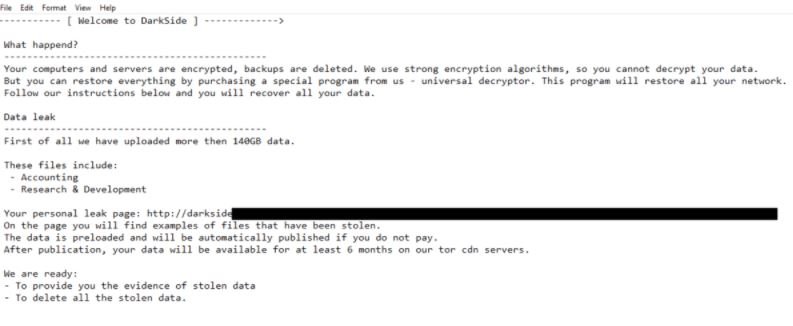
FireEye believes these attackers have become more sophisticated, reflected in the most successful attacks recently recorded. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










