In its most recent report on trends in the ransomware world, security firm KrebsOnSecurity noted that all ransomware variants feature an integrated security device to prevent detection; according to experts, these malware variants are not installed on Windows systems that have one of multiple virtual keyboards in languages such as Russian.
This may be a mechanism by which threat actors seek to protect themselves from law enforcement agencies, mainly because these groups increasingly attract the attention of the US government, which constantly points to countries such as Russia or Ukraine as the main cybercriminal operations centers.
Simply put, countless strains of malware will check for the presence of one of these languages on the system and, in case of detection, the malware will close and not install.
As a result of this finding many system administrators began installing virtual keyboards with multiple European and Asian languages, thinking that this will add an additional layer of protection against ransomware. However, experts claim that in no way will this practice keep a Windows system safe from malware, as there is a lot of malicious software that does not perform such checks.
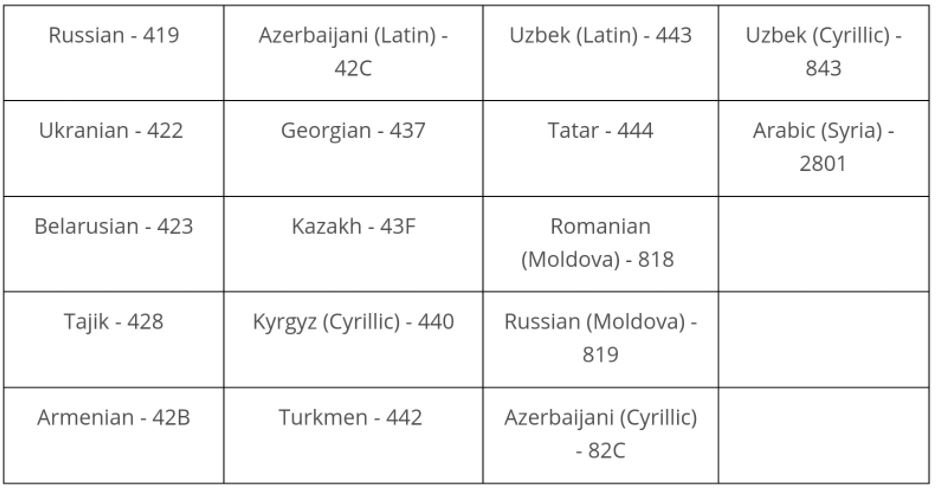
The full list of languages includes: Russian, Azeri, Uzbek Latin, Cyrillic Uzbek, Ukrainian, Georgian, Tatar, Arabic, Belarusian, Kazakh, Romanian, Tajik, Kyrgyz, Moldovan Russian, Armenian, Turkmen and Cyrillic Azeri.
Still, many cybersecurity experts recommend using these tools in conjunction with the other anti-malware solutions the user has on their system, since the worst thing that could happen is that, by accident, a user changes the language of their system and has to do some research on YouTube or Google.
In most cases, simply press the Windows key and space bar at the same time, bringing up all the languages installed on the system.
It should be noted that this does not mean that attackers stop all their operations by finding any of these languages on the target system, since in previous weeks it was reported to detect a variant of the DarkSide ransomware that does not perform this language check.
Allison Nixon, research manager at cybersecurity firm Unit221B mentions that this practice also allows hackers to ensure that they are only attacking victims outside Russian and Ukrainian territories: “Installing a Cyrillic keyboard or changing a location setting might suffice to trick some variants of Russian malware, avoiding having to deal with paying a ransom.”
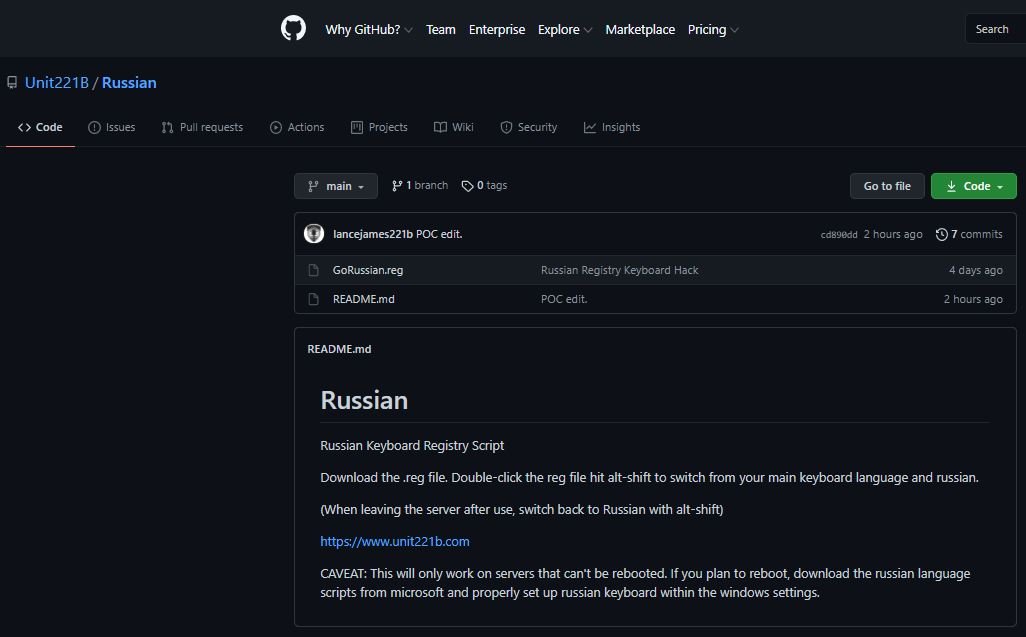
Nixon said that if enough people do this in large numbers, in the short term it can function as protection and, in the long run, force Russian hackers to take a new approach to attacks in the West, allowing cybersecurity researchers to be prepared against new trends once they appear. Cybersecurity specialist Lance James says he loves the idea of everyone adding one of these languages to his Windows system for protection against ransomware, for which he created his own script (available on GitHub) that adds a Russian reference to the specific keys analyzed by ransomware operators.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











