Pentesting is one of the most important processes in cybersecurity, as it allows a correct analysis of internal vulnerabilities to determine the best way to address the flaws encountered during the process. This is an essential task for specialists, so it is necessary to reflect on what are the best tools available.
This time, internal vulnerability assessment at the International Institute of Cyber Security (IICS) will show you the 15 best tools to perform this type of scan on corporate networks. The tools shown below are actively used by a wide range of specialists, so it will be useful for all stakeholders to know their capabilities and master them perfectly.
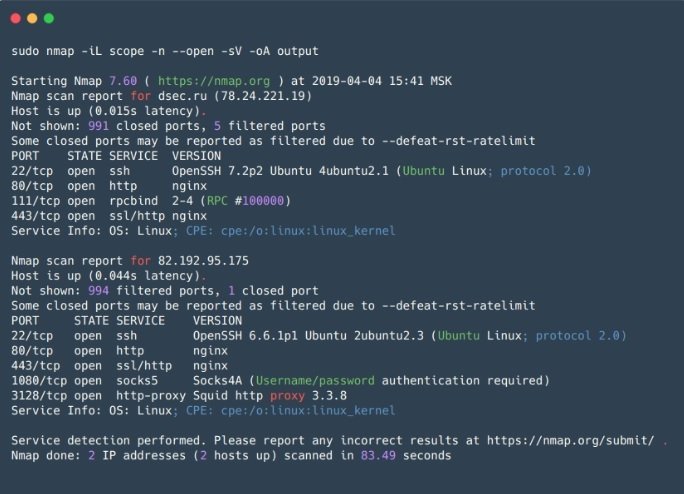
Nmap
This is an open source network scanning utility and one of the most popular internal vulnerability analysis tools in the world of cybersecurity. Nmap is mainly used for port scanning, although it has many other very useful features for researchers, including open port listening service and identifying security vulnerabilities.
Nmap allows researchers to develop a detailed network map, get the most information about running services on network hosts, and proactively verify some known vulnerabilities.
Pros: The tool works quickly with a small variety of hosts, and has a flexible configuration to make the most of all its capabilities. Nmap also has predefined sets of scripts for different tasks and outputs its results in five different formats, including XML.
Cons: The main disadvantage of Nmap is that information about particular hosts will not be available until the scan of the entire group is complete. In addition, SYN packets are sent to the target port during scans, which directly impacts overall scan performance compared to other solutions for internal vulnerability analysis.
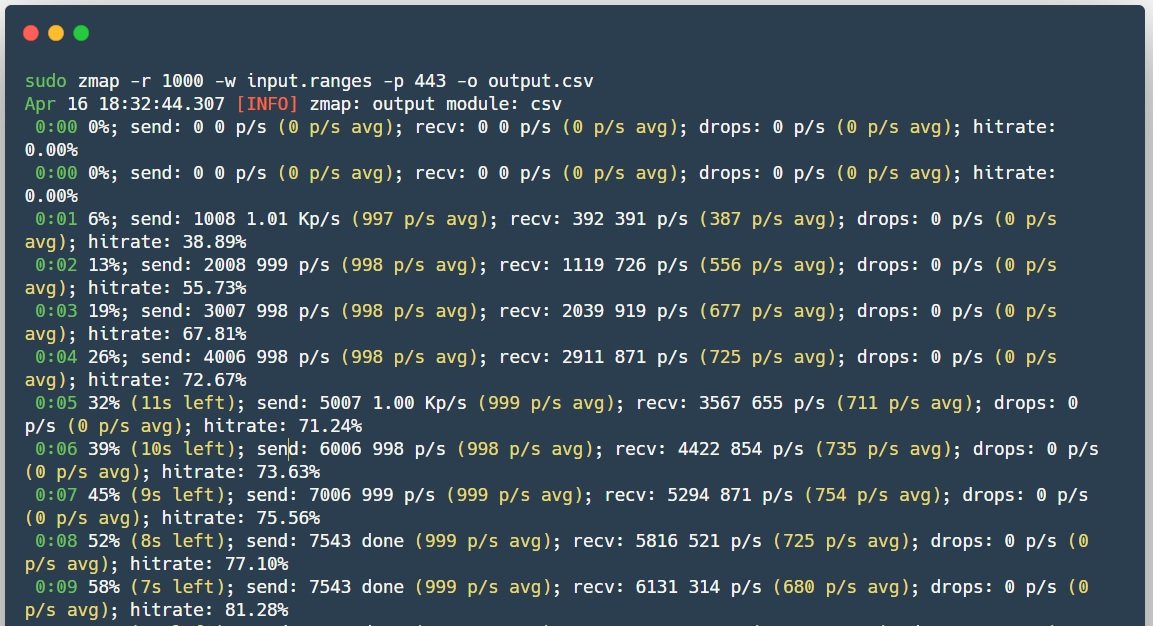
Zmap
Zmap (not to be confused with ZenMap) is also an open source scanner created as a faster alternative to Nmap. Unlike its counterpart, Zmap does not wait until a response is returned when sending SYN packets, but continues to scan, waiting in parallel for responses from all hosts, so it doesn’t actually maintain the state of the connection.
Pros: Among the best features of Zmap is its scanning speed, the generation of Ethernet frames without going through the system stack and the possibility to use PF_RING.
Cons: The main disadvantage is that using this tool can cause a denial of service (DoS) to the network computer, for example, to disable intermediate routers, despite distributed load, as all packets will pass through a router.
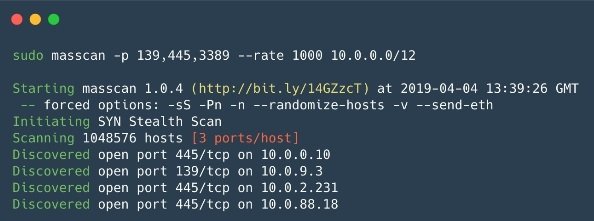
Masscan
Masscan is an open source scanner that was created with one goal in mind: to scan the Internet even faster (in less than 6 minutes at a speed of about 10 million packets per second). According to experts in internal vulnerability analysis, this tool works almost the same as Zmap, only at a better speed.
Pros: Masscan syntax is similar to Nmap and the program also supports some Nmap-compatible options, in addition to its outstanding operating speed that makes it one of the fastest asynchronous scanners.
Cons: Similar to Zmap, the load on the network is too high, which could lead to a DoS condition.
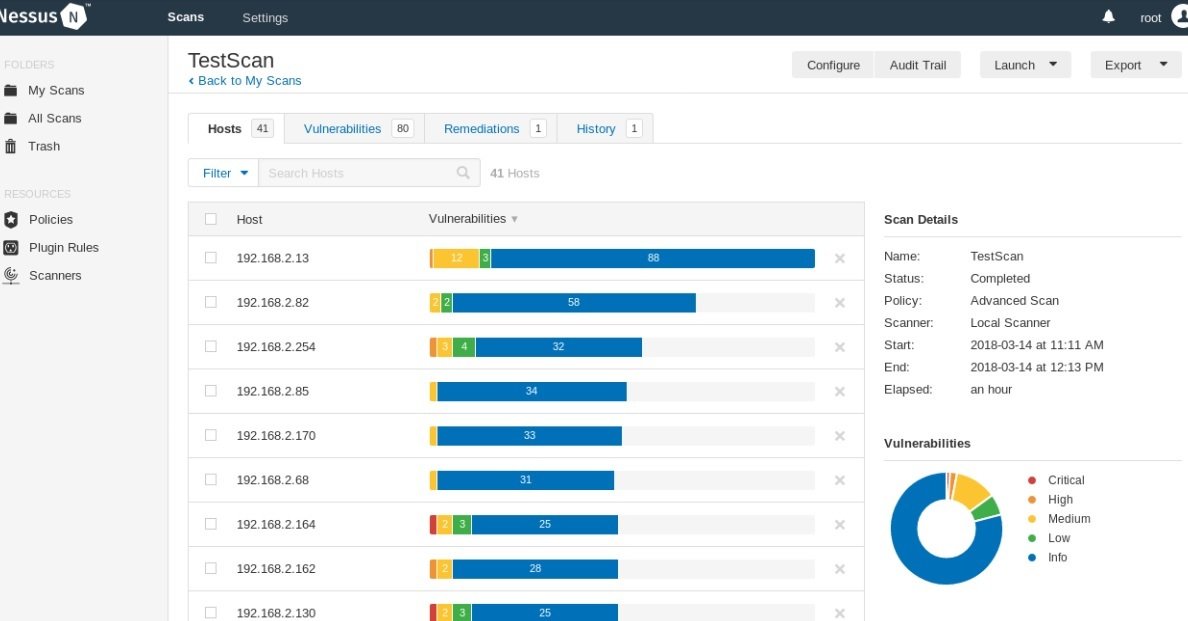
Nessus
Nessus is a scanner to automate the verification and detection of known vulnerabilities in the scanned system. According to internal vulnerability analysis experts, there is a free version of Nessus Home that allows you to scan up to 16 IP addresses with the same speed and detailed analysis as the paid version.
The tool is able to identify vulnerable versions of services or servers, detect system configuration errors and brute force dictionary passwords. It can be used to determine service configuration remediation as well as in preparation for PCI DSS auditing.
Pros: The tool has separate scripts for each security flaw found thanks to its constantly updated database. Nessus also yields results in formats such as plain text, XML, HTML, and LaTeX; Nessus API and allows scanning windows or Linux credentials to check for new updates.
Cons: The scanned systems may fail to function, not to mention that the full version of this tool requires a subscription.
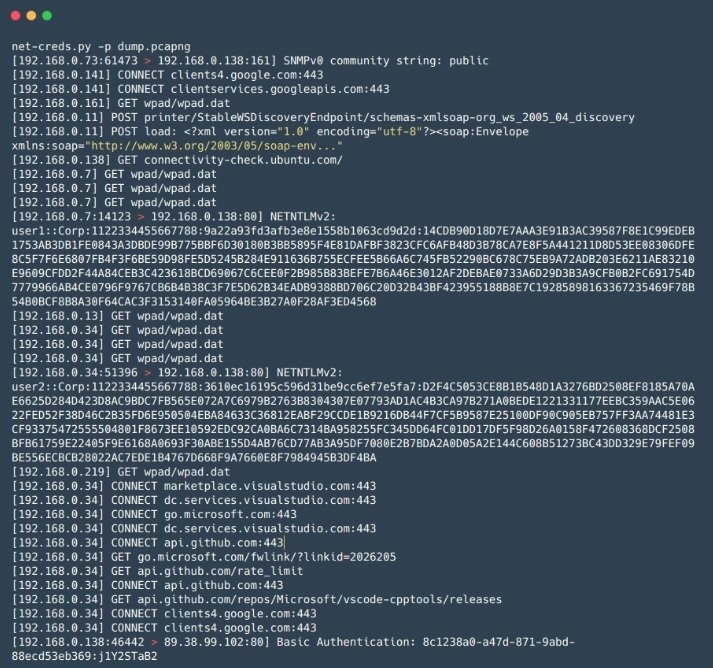
Net-Creds
This is a Python tool for collecting passwords and hashes, as well as other data relevant to the analysis of internal vulnerabilities. Net-Creds is ideal for rapid analysis of large volumes of traffic during Man-in-The-Middle (MiTM) attacks, for example.
Pros: Service identification is based on packet analysis rather than identifying a service based on the port used, and is actually quite easy to use.
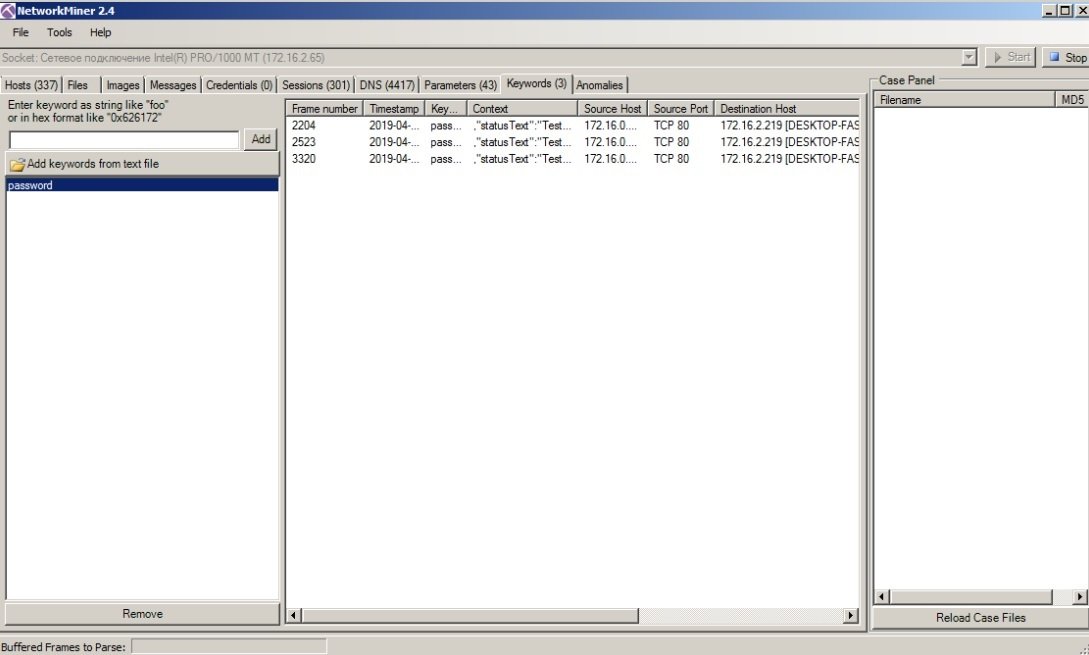
Network-miner
This is an analogue of Net-Creds in its working principle, but it has a variety of additional functionalities. Like Net-Creds, Network-miner is ideal for analyzing large amounts of traffic in no time.
Pros: This tool has a sophisticated graphical interface and options for viewing and sorting data by groups, simplifying traffic analysis.
Cons: Like Net-Creds, this tool has a free version with limited features, so researchers will have to pay to access a full version.
MITM6
This is a tool to perform attacks targeting IPv6. On Windows systems, the IPv6 interface is enabled by default, allowing analysts to configure the target system’s DNS server using Router Advertisement packets, allowing the DNS of the target system to be spoofed.
Pros: Works great on many networks due to the default settings for Windows hosts and networks.
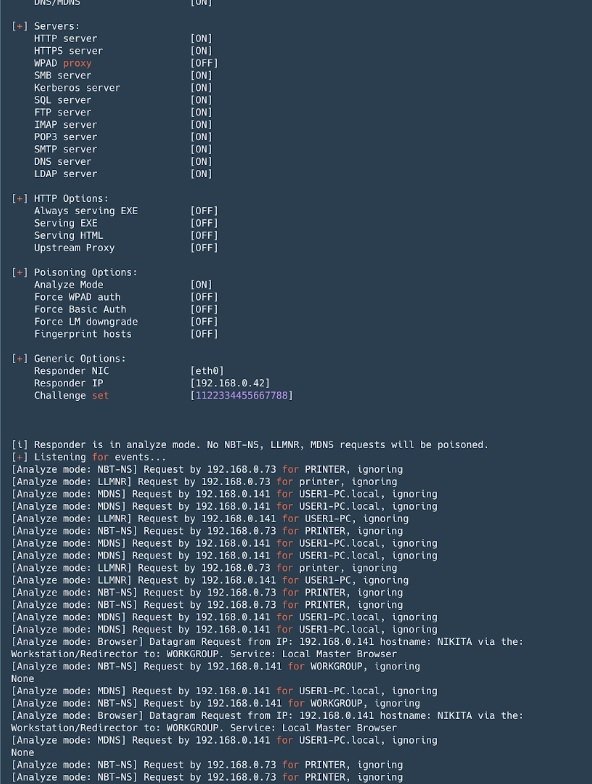
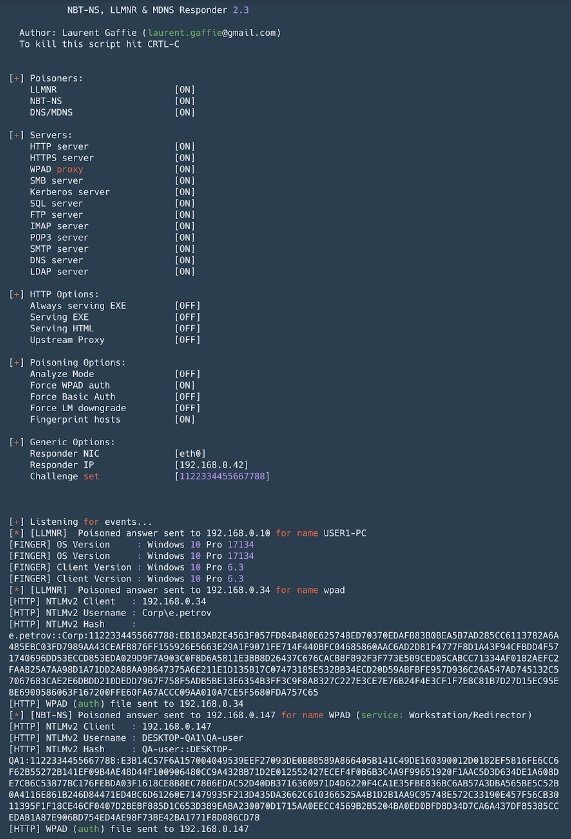
Responder
This is a tool for falsifying name resolution protocols (such as LLMNR, NetBIOS, or MDNS) that is indispensable for any Active Directory network. In addition to performing forgery attacks, the tool can intercept NTLM authentication and includes a set of tools to collect information and implement NTLM-Relay attacks.
Pros: By default, the tool lifts many servers with NTLM authentication support: SMB, MSSQL, HTTP, HTTPS, LDAP, FTP, POP3, IMAP and SMTP, and allows you to impersonate DNS in case of MiTM attacks.
Cons: When running on Windows systems, port 445 (SMB) binding presents some difficulties, internal vulnerability analysis specialists point out.
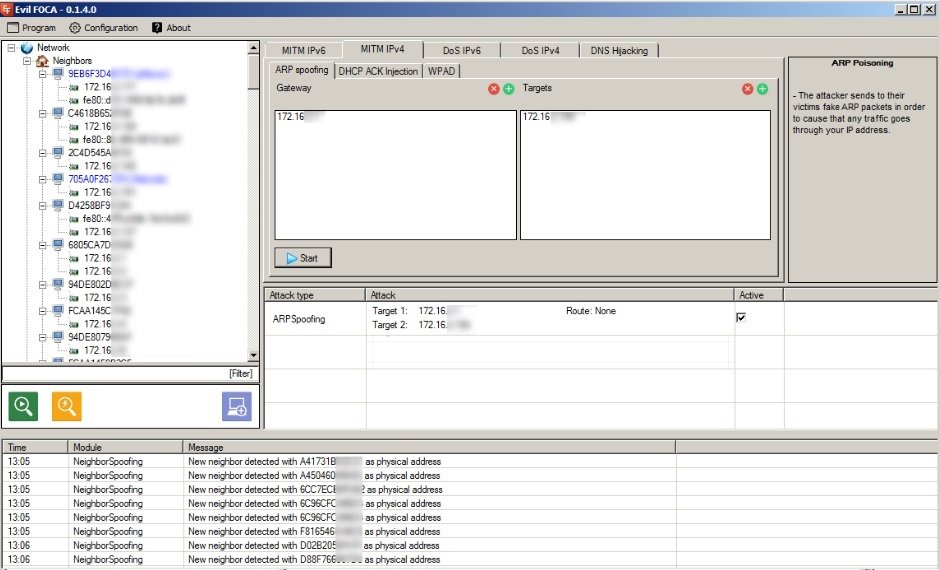
Evil Foca
Evil Foca is a tool to test multiple variants of attacks against IPv4 and IPv6 networks. The tool can scan the local network, identify devices, routers and their network interfaces, and perform various attacks against connected devices.
Pros: This tool is very useful for DoS attacks and MiTM attack variants (ARP impersonation, DHCP ACK injection, SLAAC attacks, DHCP impersonation). In addition, a DNS hijacking can be performed and has a very easy-to-use graphical interface.
Cons: Unlike most tools, Evil Foca only works on Windows systems.
Bettercap
This is a powerful framework for analyzing and attacking networks, and here we are also talking about attacks on wireless networks, BLE (bluetooth low energy) and even MouseJack attacks on wireless HID devices. Bettercap also contains functionality for collecting traffic information.
Pros: The tool can capture visited URLs and HTTPS hosts, as well as making it possible to deploy MiTM attacks and manage traffic according to researchers’ needs. The tool also supports caplets, which are files that allow you to describe complex and automated attacks in a scripting language.
Cons: Some modules (for example, ble.enum) are not partially compatible with macOS and Windows, plus some are designed for Linux only (packet.proxy, for example).
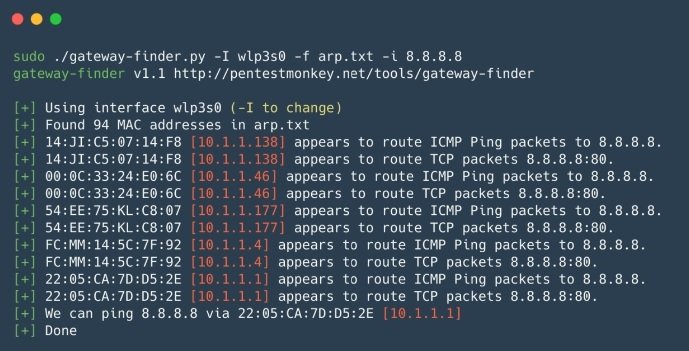
Gateway_finder
This is a Python script that helps identify potential gateways on the network. According to internal vulnerability analysis experts, this tool is ideal for verifying segmentation or finding hosts that can route to a desired subnet or Internet. Gateway_finder is also well suited for internal penetration testing when you need to quickly verify unauthorized routes or routes to other internal local networks.
Pros: The main advantage of Gateway_finder is that it is very easy to use and has great customization capability.
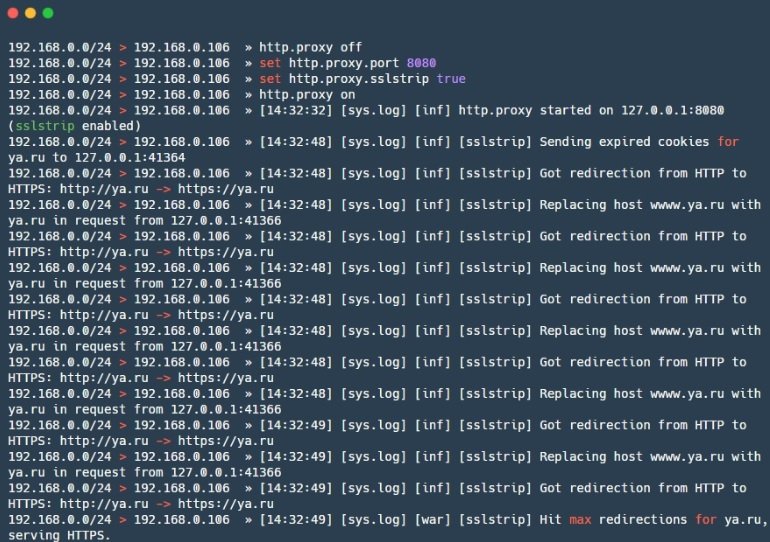
Mitmproxy
This is an open source tool for analyzing SSL/TLS-protected traffic. Internal vulnerability analysis experts can use Mitmproxy to intercept and modify secure traffic, although this tool does not allow SSL/TLS decryption attacks.
An attack consists of Mitmproxy, for proxy traffic, mitmdump, similar to tcpdump, but for HTTP (S) traffic, and mitmweb, a web interface for Mitmproxy.
Pros: The tool works with multiple protocols and also supports modifying various formats, from HTML to Protobuf. The tool also has an API for Python, which allows users to write scripts for non-standard tasks.
Cons: The dump format is not compatible with anything, it is difficult to use grep and the user has to write scripts.
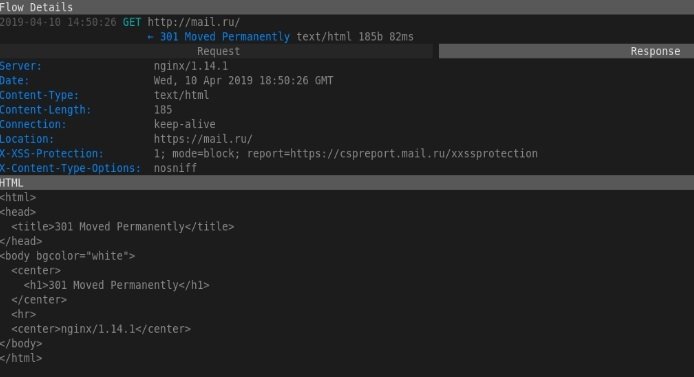
SIET
SIET is a tool to take advantage of Cisco Smart Install protocol capabilities. It is possible to obtain and modify a configuration, as well as take control of a Cisco device, mentioned by experts in internal vulnerability analysis.
Pros: The use of the Cisco Smart Install protocol allows you to perform all kinds of actions, including:
- Change the tftp server address on the client device by sending an incorrectly formatted TCP packet
- Copy the device configuration file
- Replace device settings, for example, by adding a new user
- Update the iOS image on your device
Cons: SIET works with a limited set of Cisco devices, plus you need a white IP to get a response from the device or it must be on the same network with the device.
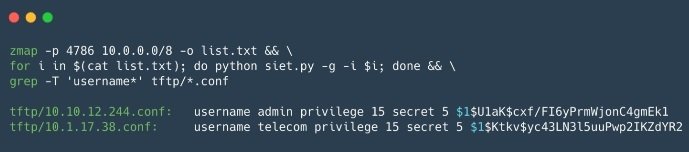
Yersinia
Yersinia is an L2 attack framework designed to exploit security flaws in various L2 network protocols.
Pros: Allows attacks on STP, CDP, DTP, DHCP, HSRP, VTP and others.
Cons: Experts believe that the Yersinia interface is very difficult to use for most researchers.
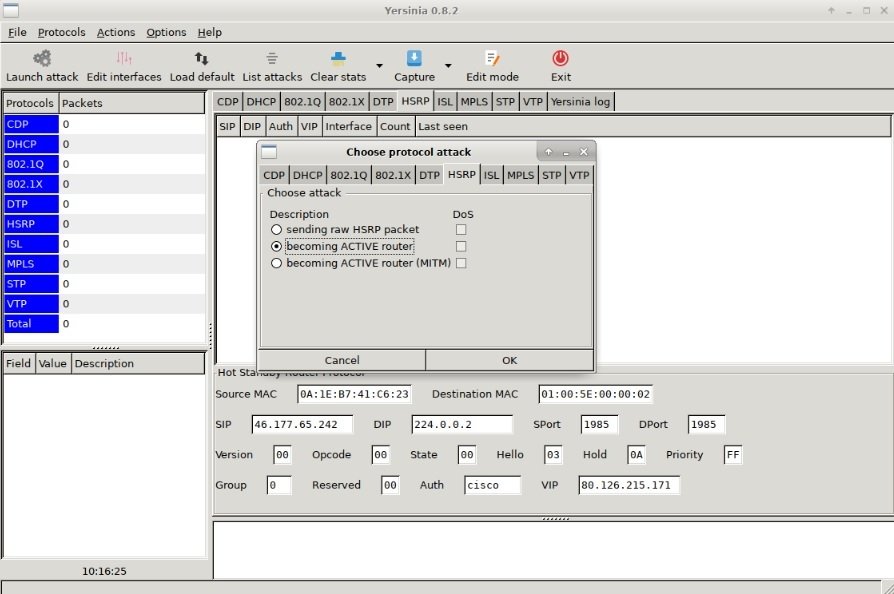
Proxychains
Proxychains is a tool that allows users to redirect application traffic through a specific SOCKS proxy.
Pros: Proxychains helps redirect traffic from some applications, which by default do not know how to work with a proxy.
Recuerde que este artículo fue elaborado con fines exclusivamente informativos, por lo que IICS no es responsable del mal uso que pueda darse a esta información. To learn more about information security risks, malware variants, internal vulnerability assessment and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











