Reverse engineering is one of the most important methods for research and hacking, as it allows users to determine which are the components of antivirus tools, malware variants or datasets, as well as discover how these elements interact with each other and how they were integrated into a single development.
For malware reverse engineering professionals, debugging an application is critical because it facilitates the reverse engineering process and allows researchers to advance the analysis of potential security threats. This time, experts from the International Institute of Cyber Security (IICS) will show you the best tools to reverse engineer applications, malware and network traffic, which will certainly be of great use to cybersecurity experts in debugging, disassembly and any other steps involved in reverse software analysis.
As usual, we remind you that this material was made for specifically informative purposes, so IICS is not responsible for the misuse that may be given to this tool.
X64dbg
This is a modern debugging tool with a very easy-to-use interface. According to malware reverse engineering experts, the tool supports x64 and x86 architectures, as well as having useful plugins for different occasions.
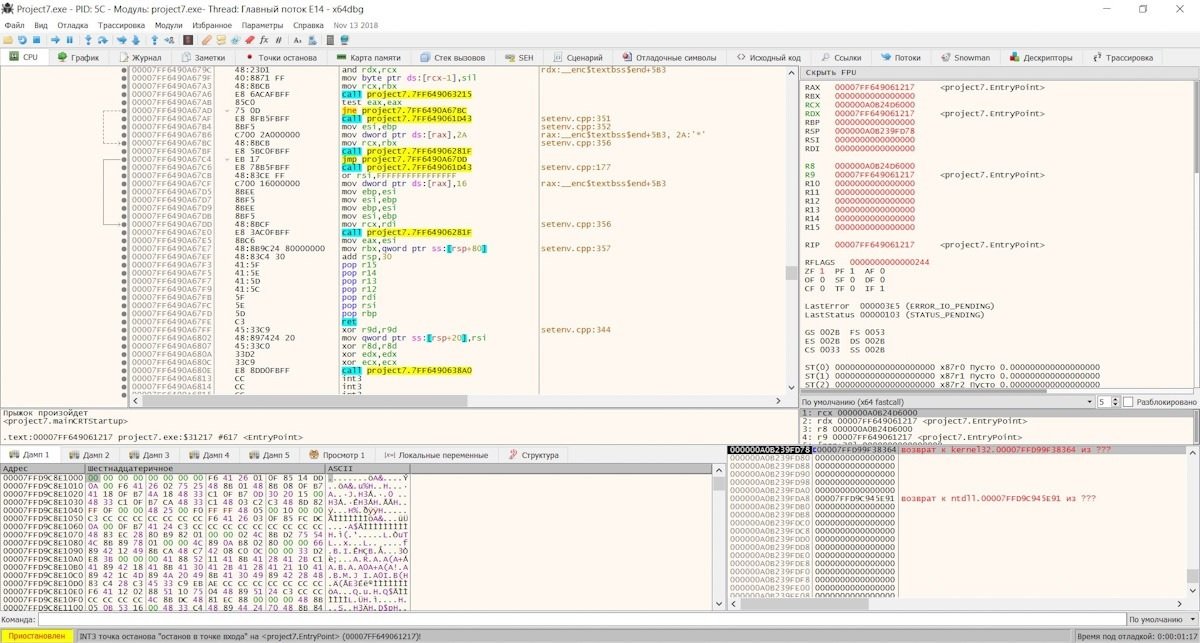
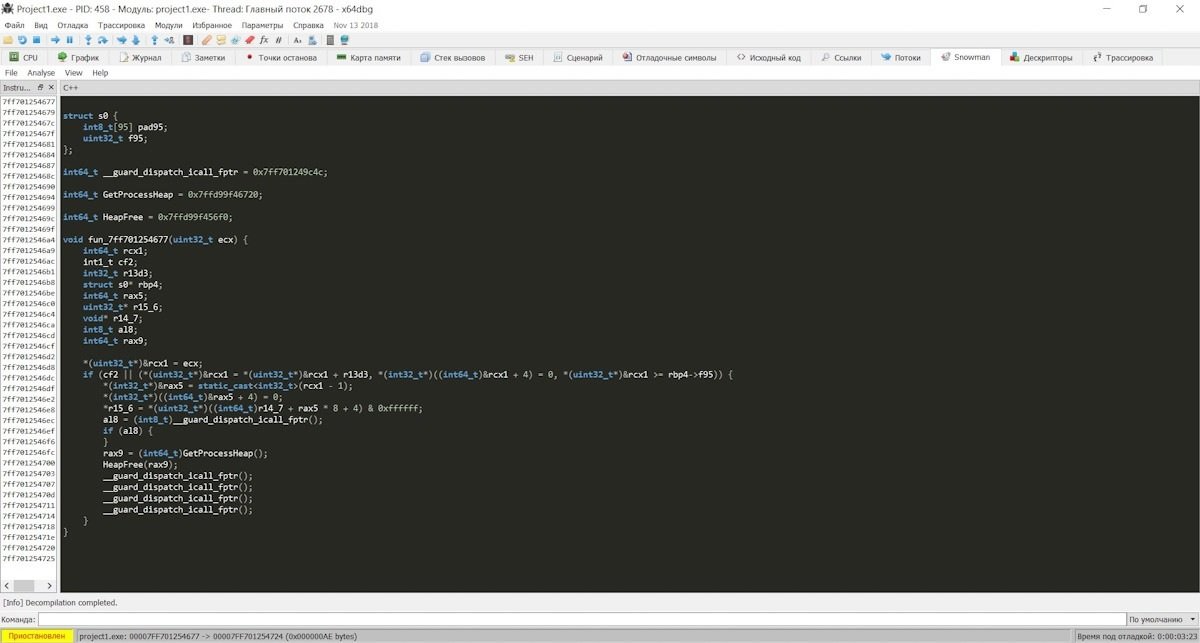
While the tool frequently fails, its maintainers remain active and send constant updates to optimize its operation. On the other hand, x64dbg has a built-in decompiler, supports displaying code as a graph, and can make breakpoints for reading, writing, running, and accessing, as well as having a built-in import rebuild utility for both x64 and x86.
WinDbg
This debugger is maintained directly by Microsoft and is included in the Windows Driver Kit (WDK). It is currently considered the most updated and powerful kernel debugging tool and can operate in kernel mode, although it does not have a very accessible interface for its new users.
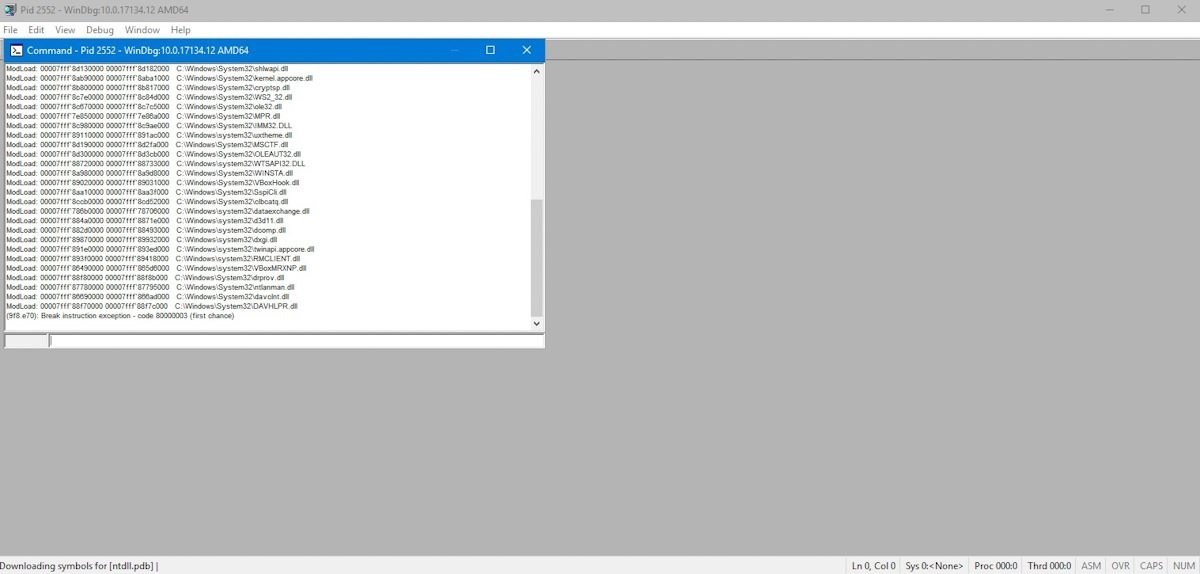
WinDbg supports remote debugging and can download debug symbols directly from Microsoft servers. To quickly configure it to debug the operating system kernel within virtual machines, there is a VirtualKD plugin.
IDA Disassembler
This tool has a free version and a paid version. The first version only supports x86 and has no support for plugins. On the other hand, the paid version can be used without architectural restrictions or plugins, which makes it a much better choice for researchers.
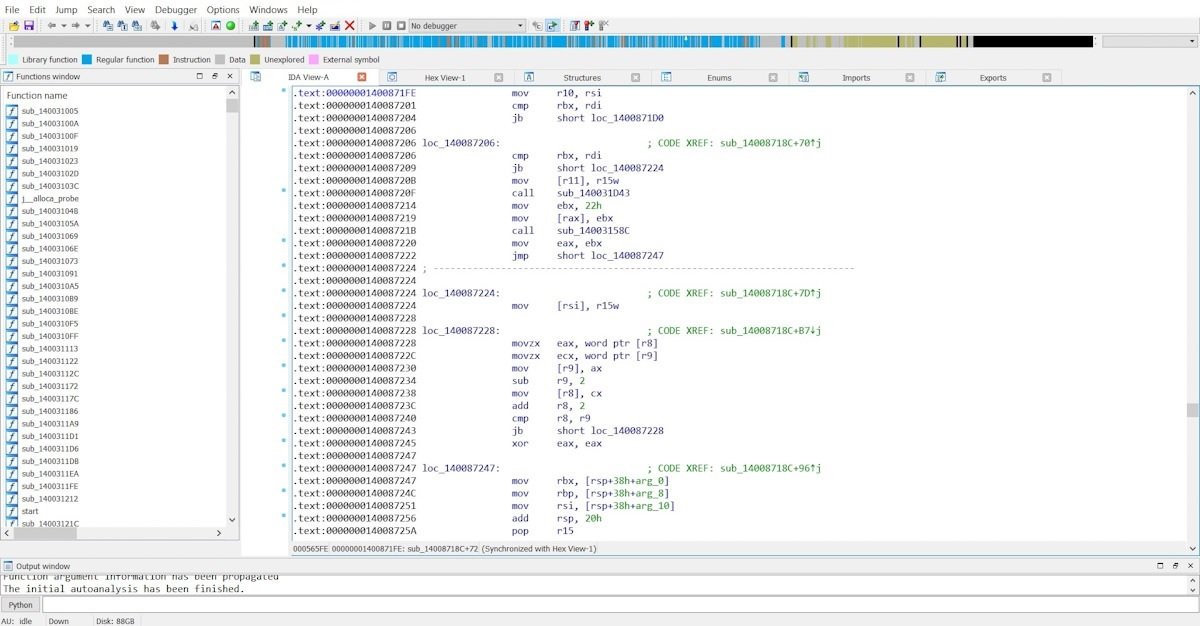
IDA has a built-in debugger, very simple in terms of a set of functions but with a somewhat complicated user interface. This tool can also be adapted with the Hex-Rays plugin, a powerful C-written decompiler that greatly enhances the default features of IDA Disassembler.
Radare2
According to malware reverse engineering experts, this tool was originally intended as a hexadecimal editor, although it was eventually turned into a complete framework for debugging and disassembled all kinds of code, including malware.
Radare2 is a collection of console utilities that includes a debugger, disassembler, decompiler, hexadecimal editor, native compiler and binary comparison utility, among many other tools, as well as having all kinds of processors and platforms, thanks to which you can compete even with products such as the paid version of IDA Disassembler.
Detect it Easy (DiE)
This is an excellent program to identify packers, in addition to having additional functionalities such as the calculation of the entropy of the file sections.
The tool also includes a resource viewer capable of overturning to disk, allowing you to easily view the import table, support for extensions and scripts. The biggest disadvantage of DiE is that its maintainers do not usually release updates, so the reported bugs are fixed until the release of completely new versions.
ExeInfoPE
This is a very functional packer and protector detector although with a rather peculiar interface that can become difficult to understand. Even so, the program is constantly updated and is full of interesting features for malware reverse engineering experts.
Experts consider this to be the ideal tool for beginners as it also contains default features for a friendlier operation, not to mention support for popular plugins.
HxD
HxD is a prominent member of the hexadecimal editor family, as it is one of the main options for accessing a hard drive, memory or application in binary mode. The tool is free and constantly updated, as well as allowing you to safely delete files and support a portable version.
HIEW
This tool has a free version and a paid version that receives constant maintenance from the developers. Malware reverse engineering experts mention that this is a tool similar to Norton Commander, although the user interface is a little more complex.
Pestudio
Pestudio is an advanced malware analysis tool that automatically scans any sample, even taking databases from platforms like VirusTotal.
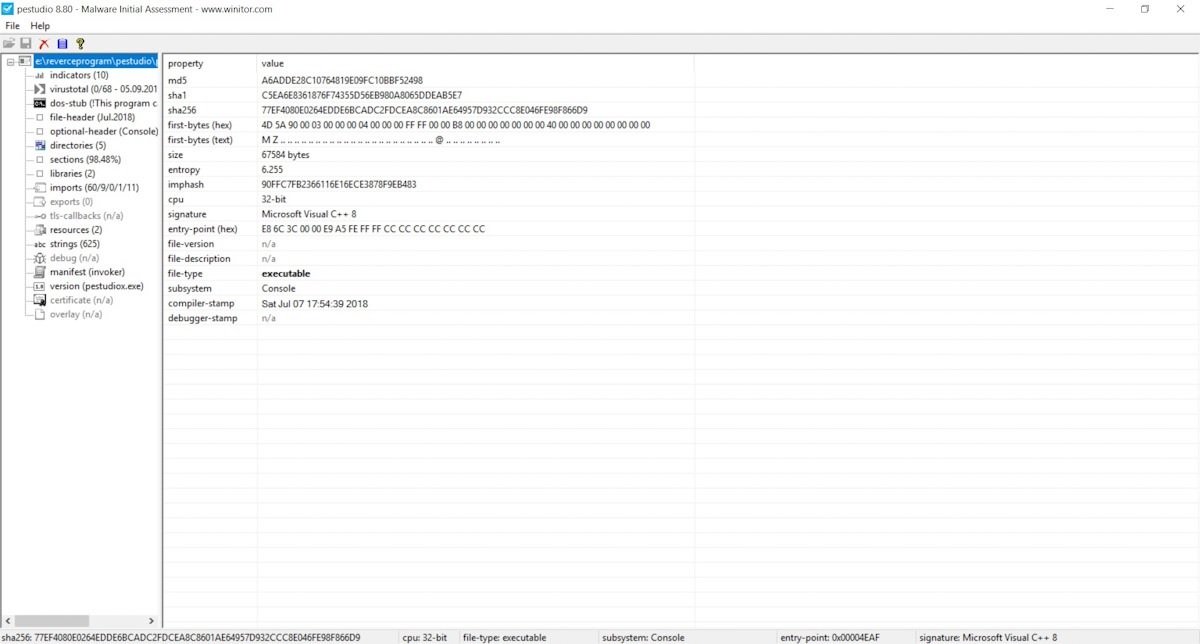
The tool practically displays the import table functions used in the test application, displays the application’s virus signatures, the libraries used, and the PE file header information. In other words, it is a multifunctional antivirus collector for initial sample analysis.
PE-bear
This is a convenient viewer and editor for PE and PE+ files that contains a parser of packers and protectors, displays information about file headers, resources, and sections. If users choose, they can access to see the hexadecimal representation of these sections and disassemble them into ordinary assembler mnemonics.
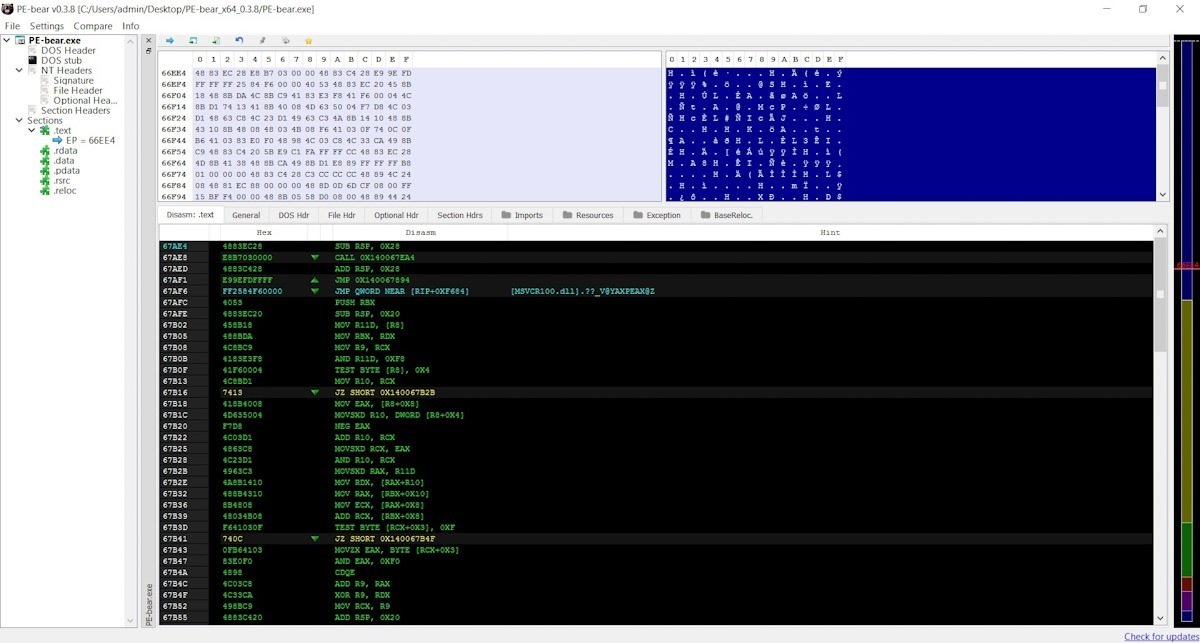
PE-bear has a friendly interface and a plugin pre-installed to compare files, although as a disadvantage the program does not receive updates constantly, although we should not forget that it is an open source tool.
Fakenet-NG
This is a specialized program for networking that allows you to examine any malware sample, monitor DNS and HTTP requests, track web traffic and analyze IP addresses. Fakenet-NG operates on an offline virtual machine, so it is a completely secure tool.
The tool receives updates constantly, so it can be compatible with even the most modern operating systems.
ProcessExplorer
The interface of this tool shows all running processes of the system organized hierarchically, allowing malware reverse engineering experts to identify the order in which processes are generated.
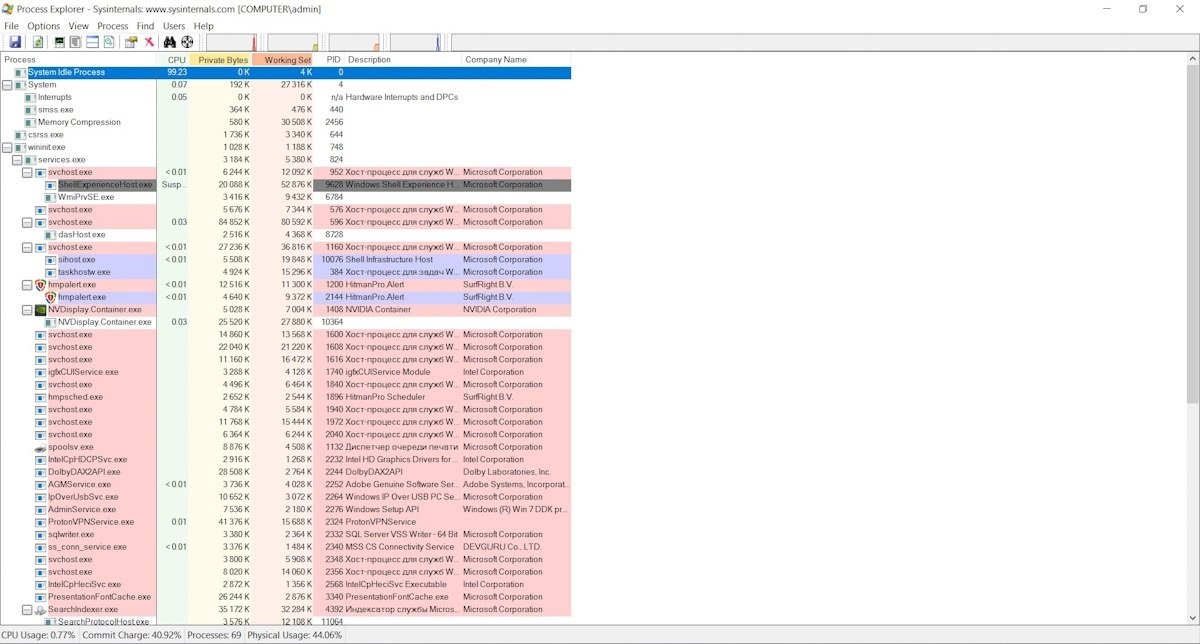
The tool allows you to find out which dynamic libraries are loaded into processes, priorities, digital signatures and processor usage.
RegShot
RegShot is an ideal program to monitor any changes in the registry, take screenshots before and after the analysis and allow identifying the changes that were made.
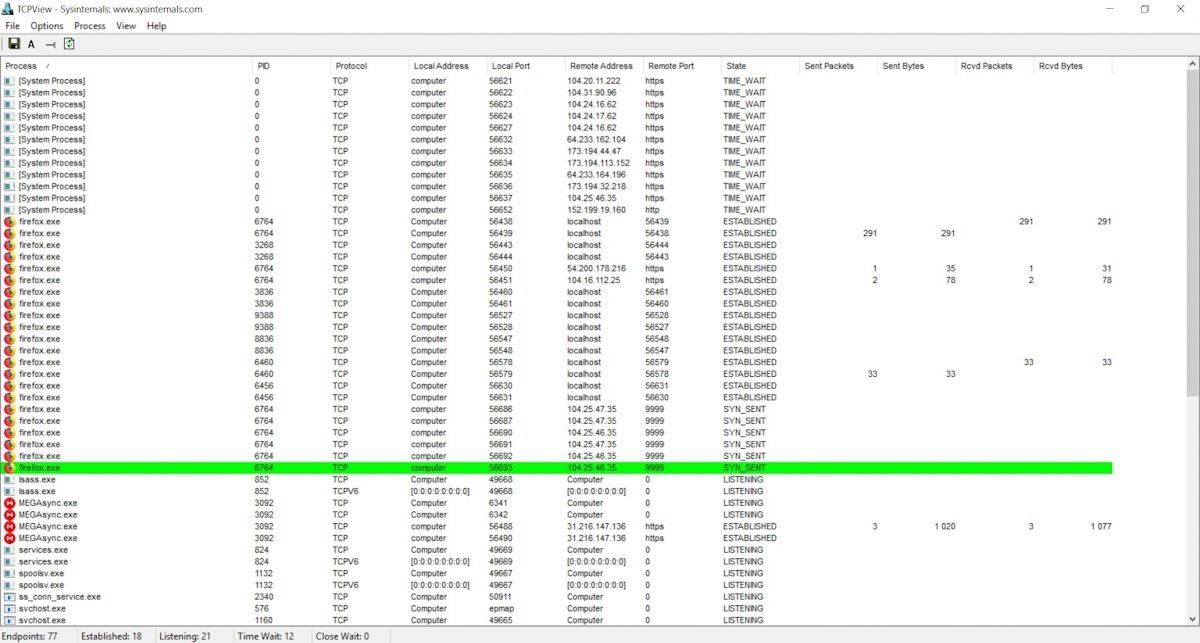
TCPview
This program monitors network and application activity on the scanned system. Users can see which ports are opening the application locally and remotely, as well as identify protocols, process IDs, and forward packet counters.
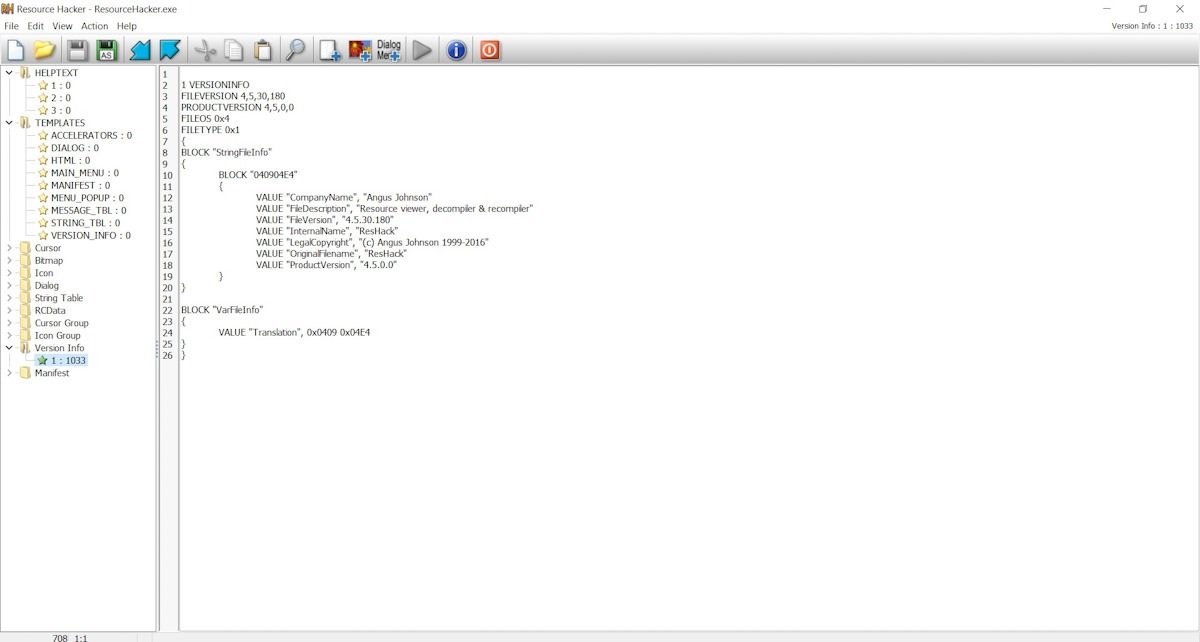
Resource Hacker
This is a popular tool for editing resources. According to malware reverse engineering specialists, users can edit icons, text dialog strings, cursor information and other records. You don’t need to edit your application’s resources frequently, but you need to have the right tool.
These applications should be more than enough for researchers and those not started in this topic. Mastering these tools will allow enthusiasts to approach other more sophisticated tools and even get into the development of new software for malware reverse engineering projects.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











