A newly discovered hacking group is deploying an ambitious malicious campaign against politicians in Africa and the Middle East. The operation, identified as “BackdoorDiplomacy”, has also been detected in Europe and Asia.
ESET experts believe this campaign has been active since at least 2017, targeting Windows and Linux systems in order to exploit vulnerabilities in Internet-connected devices. When threat actors encounter vulnerable web servers or management interfaces, they will exploit the F5 flaw identified as CVE-2020-5902 to install a Linux backdoor; as for Windows systems, hackers exploit bugs in Microsoft Exchange to install the China Chopper webshell.
As users may recall, the term backdoor refers to an access point hidden within the code of a legitimate software variant. Threat actors use a backdoor to access affected systems without being detected.
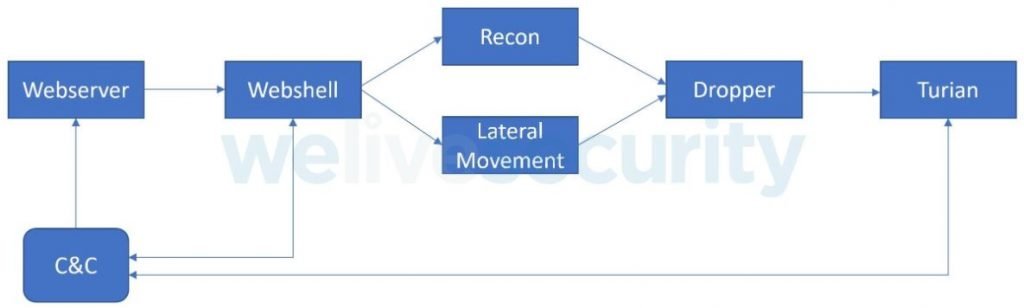
After initial access, threat actors scan the device to perform lateral movements, install the backdoor, and deploy multiple tools to perform monitoring and data theft activities. This backdoor, identified as Turian, could be based on Quarian, a backdoor detected in 2013. The main implant is capable of collecting and filtering information from the target system, in addition to taking screenshots and arbitrarily modifying the compromised files.
The set of tools employed by the Hackers of BackdoorDiplomacy includes EarthWorm, Mimikatz and NetCat, in addition to using VMProtect for the obfuscation of malicious activities.
Politicians and diplomats around the world are frequent targets of all kinds of cyberattacks, as by the nature of their work they often deal with sensitive information through physical storage units and cloud deployments.
In an example approach, hackers search for flash drives and try to copy the password-protected files to send the copies to a C&C server. While this is a fully identified hacking group, experts believe that BackdoorDiplomacy could be linked to at least three other major hacking groups.
Separately, Check Point Research researchers discovered a similar backdoor identified as VictoryDll_x86, used in multiple attacks on the infrastructure of an Asian country that was not named. It is believed that both hacking campaigns could be strongly linked.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











