Cybersecurity specialists report the discovery of a dangerous redirect vulnerability in the Google-for-Android app that would allow threat actors to arbitrarily extract data and access all records on Google of the affected user.
According to the developers of the Oversecured app scanner, malicious hackers could abuse this flaw to intercept all kinds of information, including SMS messages, contact lists, camera and microphone logs, call history and other sensitive data.
To make matters worse, the attacking application only needs to be launched once to make a successful attack. After that, malicious functionality can still be present in the Google app independently even if it is removed, plus the attack doesn’t require the user to approve of improper access.
The analysis reports that a content provider with the flag Content-lengthandroid:grantUriPermissions=”true” contains a handler that could grant another app permission to read and write files: “The app also uses the Google Play Core library, so if an attacker writes an arbitrary module, the attacker’s module classes would automatically be added to the affected app’s ClassLoader.”
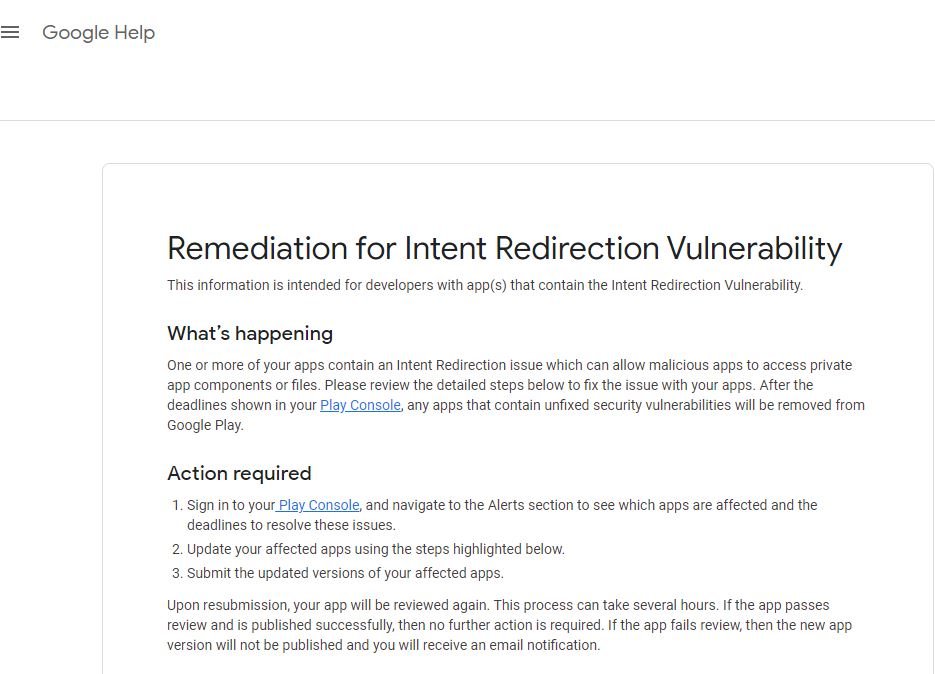
Google notified developers that apps that are affected by these kinds of flaws will be removed from the Google Play Store, although a grace period was granted for developer companies to update any affected software.
The company recommends developers check their Play Console for security alerts on their apps, and also asks for reports of updated apps to be sent. Google concluded by mentioning that there are different ways to make the application component in which the fault resides private; developers can ensure that the extracted Intent comes from a trusted source, or ensure that the intent being redirected is not harmful.
Oversecured developers warn of dangers in the way mobile apps currently work: “Almost all Android apps dynamically load code from native libraries .iso or .dex files. Developers should understand that this practice is unsafe, as it would even allow arbitrary files to be overwritten during the execution of critical code in a vulnerable app.” While Google has already corrected the reported flaw, Oversecured has found evidence of exploitation of similar flaws in other apps, including TikTok.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











