Cybersecurity specialists report the discovery of a dangerous vulnerability in Microsoft 3D Viewer, a 3D object visualization and augmented reality tool first launched in Windows 10 1703. According to the report, successful exploitation of this flaw would allow threat actors to execute arbitrary code in the affected implementations.
The vulnerability requires user interaction to be successfully exploited, tricking affected users into visiting malicious websites or downloading malware-infested files.
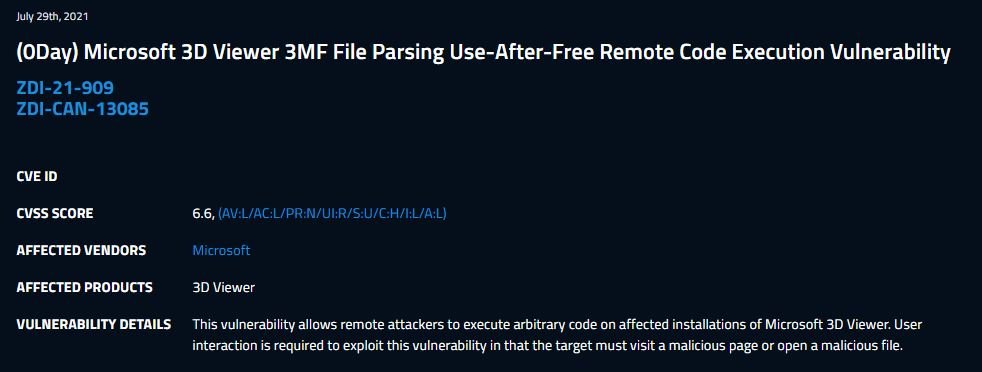
Apparently, the fault lies specifically in the analysis of 3MF files and is the result of the lack of verification for the existence of objects before performing operations. Threat actors can exploit the flaw for code execution in the context of the current process with low integrity. This bug was reported to Microsoft through The Zero Day Initiative (ZDI) by cybersecurity specialist Mat Powell.
The report was sent by ZDI to Microsoft along with a request to publish this flaw as a zero-day vulnerability. While the company received the report and indicated that it did not meet the characteristics set for analysis as a zero-day failure, it was agreed to conduct a detailed review.
So far there are no security patches available, so given the nature of the vulnerability, specialists say that the only way to mitigate the risk of exploitation is to restrict any interaction with the affected application, at least until the release of the security patches.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











