Cybersecurity specialists report the detection of a web attack structure implemented by an alleged group of Chinese state-sponsored hackers and designed to exploit security flaws in dozens of popular websites in order to gather information about dissidents and opponents of china’s government. Apparently, hackers are attacking at least 57 Chinese websites and the official platforms of the American newspaper New York Times.
The report mentions that this tool is also capable of abusing some legitimate browser functions to deploy a keylogging attack, in addition to collecting multiple data about the operating system, location details and even taking screenshots and images from webcams.
Identified as Tetris, this tool was first found on two Chinese websites that appeared to be non-profit news blogs, says one of the researchers who participated in Tetris’ analysis. The researcher works under the pseudonym “Imp0rtp3”.
The expert mentions that users who entered a compromised website were greeted by Jetriz, the first of two components of Tetris and that it was in charge of collecting information about the target user’s browser. If the browser was set to Chinese language, the user would be redirected to the second malicious component.
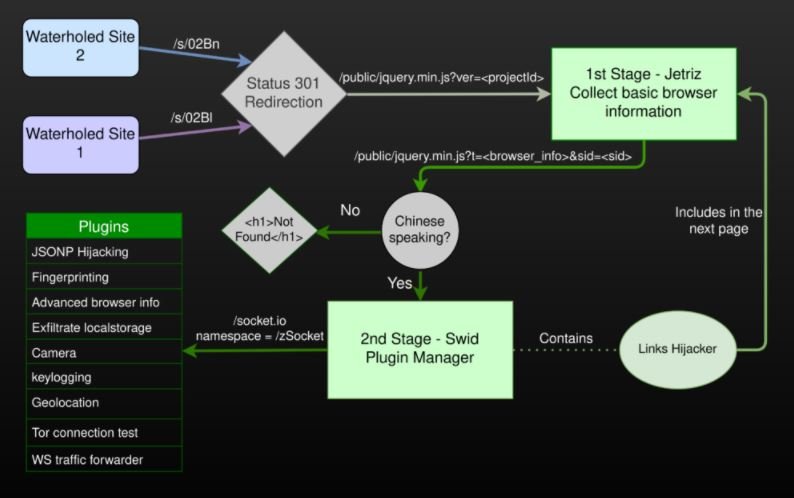
Swid, the second component, loads 15 additional plugins in JavaScript inside the victim’s browser. Eight of these plugins abuse a JSON hijacking technique to initiate connections to popular websites and retrieve public data about users. This technique does not allow the extracting of passwords or authentication cookies; although the report mentions that a threat actor could retrieve information such as user names, telephone numbers and even real names, allowing the elaboration of detailed user profiles.
Imp0rtp3 maintains that these tactics and procedures are linked to a hacking group that collaborates very closely with the Chinese government. The researcher bases his conclusions on the fact that Tetris operators have limited their campaign to a certain number of websites. As mentioned above, most of the affected websites are news blogs, political analysis, and anti-Chinese government opinion, which once again demonstrate its special interest in tracking and monitoring against potential threats to the regime’s stability.
Finally, the report mentions that while tools like Tetris are not very common these days, they are still a real threat to thousands of users, especially in highly targeted campaigns like the one described in this article.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











