A hacking group exposed around 500,000 Fortinet VPN service usernames and passwords allegedly obtained from vulnerable devices via exploiting a dangerous vulnerability. Although the hackers mention that the flaw has already been addressed, they assure that many of the compromised credentials are still active.
Cybersecurity specialists point out that this incident could have severe consequences, since access to these platforms would allow threat actors to steal confidential data, install malware and perform other attack variants.
According to the report, these credentials were published at no cost on RAMP, a newly created hacking platform. The hacker responsible for the leak, known as “Orange”, worked with the Babuk ransomware group, although after a series of internal disputes he decided to resign from this group and start his own dark web leak platform.
This week, the threat actor posted the information on RAMP, including a file that Orange said contains thousands of Fortinet VPN accounts.
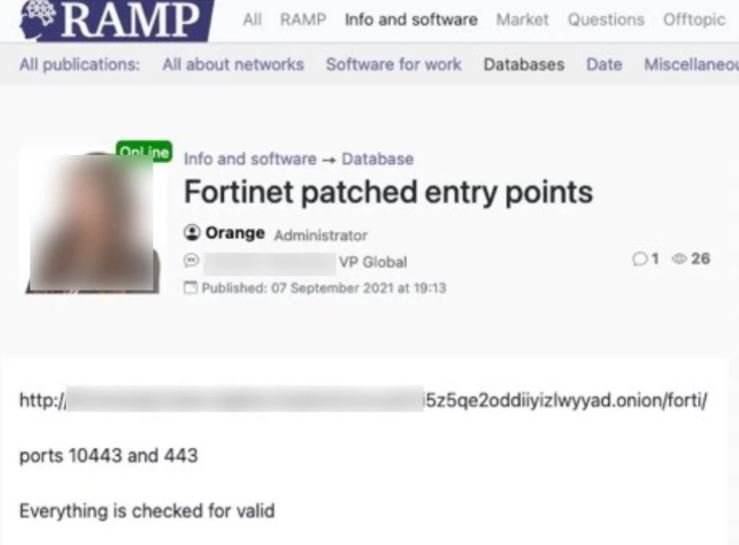
Something striking about this incident is that almost at the same time those responsible for Groove, another leak website, also published the compromised information of Fortinet VPN.
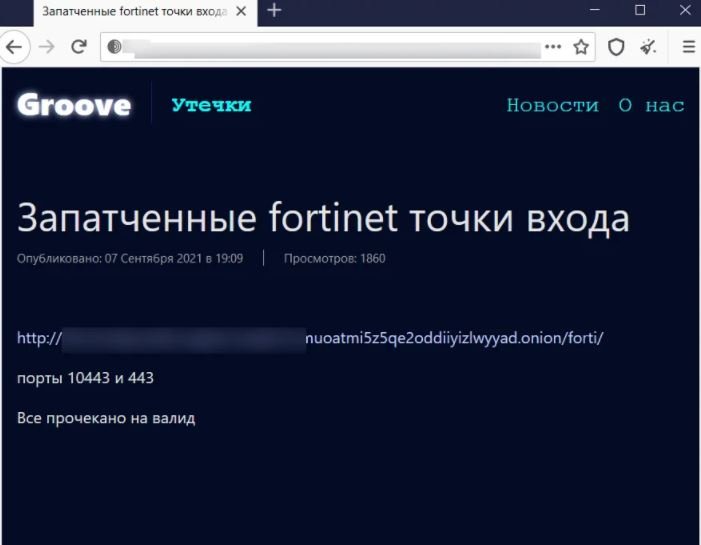
The two publications include a file hosted on Tor, employed by Groove to store compromised data and extort money from victims of its attacks. An analysis of the exposed information determined that the file contains credentials for 489,000 accounts on more than 12,000 devices.
Further more detailed analysis shows that IP addresses are for devices worldwide, with nearly 3,000 devices located in the U.S.
On the vulnerability employed by hackers, the researchers believe that this hacking group would have exploited the CVE-2018-13379 flaw for the theft of confidential information. The researchers were able to verify that at least one set of these credentials were valid at the time of the attack.
It’s not yet clear why the hackers decided to leak the credentials instead of using them for attacks or selling them to other hacking groups. One possible explanation is that the attackers wanted to promote the RAMP hacking forum and the Groove ransomware-as-a-service (RaaS) operation.
While the investigation continues, experts recommend Fortinet VPN users reset passwords on all their devices. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











