A report by the security firm Kaspersky details the detection of a hacking group using an Internet Information Services (IIS) web server module identified as Owowa, with which they seek to intercept access credentials and execute remote code in Microsoft Exchange Outlook Web Access implementations.
According to the researchers, Owowa is a .NET v4.0 assembly developed in C# and designed to be loaded as a module within an IIS web server that also exposes Exchange’s Outlook Web Access (OWA): “This form of upload allows Owowa to steal access credentials entered by any user in an OWA login window, in addition to allowing a remote threat actor to execute commands on the underlying server.”
This module could have been specifically designed to inspect HTTP requests and responses by hooking the PreSendRequestContent event; if an inadvertent user successfully authenticates to OWA, the Owawa module will capture their credentials irretrievably.
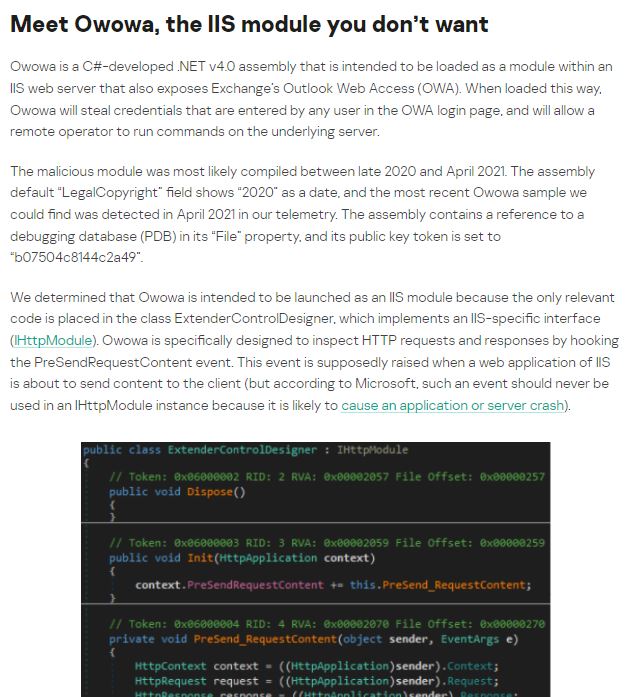
In addition, Owawa is able to verify successful authentication by checking whether OWA application sent an authentication token to the target user. The user’s user name, password, IP address, and current timestamp are stored in a file at C:\Windows\Temp\af397ef28e484961ba48646a5d38cf54.db.ses. Finally, the data is encrypted using the RSA algorithm, with an encoded public key stored as an XML blob:
<RSAKeyValue><Modulus>vTxV8wUJ0PoO2yu/Pm/aICbsT+nFwHXouNo623VIVMl6LY4R96a8cpMTHw92rs0foNcVJB8/SYQvL/6Ko9aOv1K3mm3Txa3Dfe6CmDjFb1wYoVJQ+wLksgd/MfMGXWK2rIuNTpUs1+UT1K+TNFSBAYTiiLAPczCmKkh6vcLO9iE=</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>
Exploiting Owawa begins by entering specially crafted commands within the fields for the username and password on the OWA authentication page of a compromised server; the module will then respond through the IIS server and display the results to the operator, rather than displaying them as OWA logon error messages.
By inserting the jFuLIXpzRdateYHoVwMlfc string into the OWA username, the module will return the base64-encoded encrypted credential record.
On the other hand, if the OWA username is Fb8v91c6tHiKsWzrulCeqO, the module will delete the contents of the encrypted credential record and return the OK string, while if the username is dEUM3jZXaDiob8BrqSy2PQO1, Owowa will execute the command that is typed in the OWA PowerShell password field on the compromised server. The result of this process is encrypted and returned to the operator.
So far this variant of attack has been detected only in some regions of Asia, including Malaysia, the Philippines and Mongolia; although experts do not rule out that it may spread to other regions.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











