Cybersecurity specialists report the detection of a new critical vulnerability that resides in the JNDI of the H2 database console, exploitable in an attack similar to Log4Shell. Although a level of exploitation similar to that of the Log4j flaws is not foreseen, the cybersecurity community is already analyzing the potential risks derived from this flaw, which will be tracked as CVE-2021-42392.
JFrog researchers mention that JNDI is an API that provides directory functionalities and names for Java applications, while H2 is an open-source Java SQL database widely used, primarily by Internet of Things (IoT) device manufacturers.
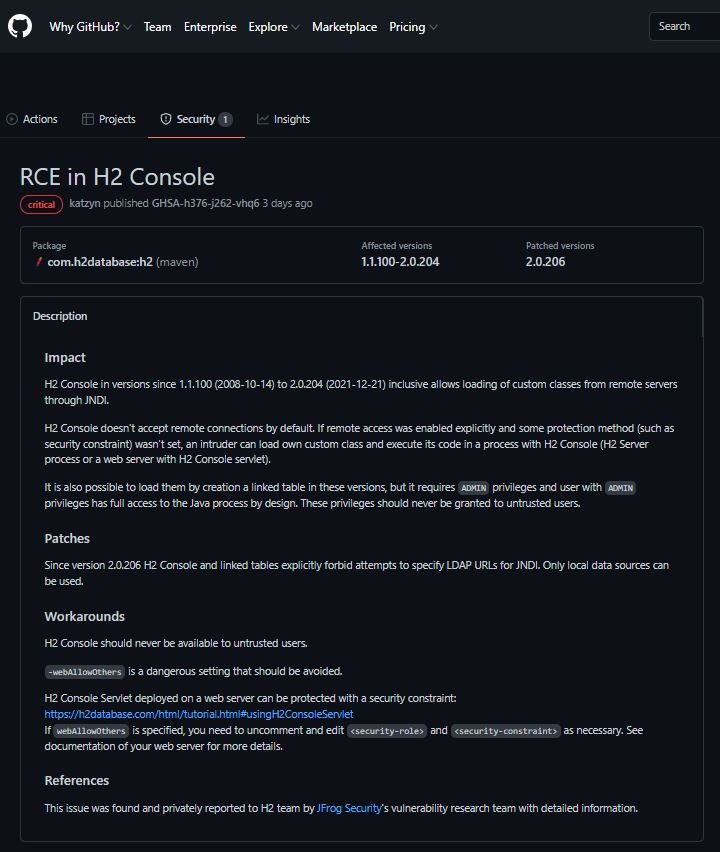
According to the report, this flaw was also detected in early December, discovering URLs controlled by threat actors to facilitate remote execution of unauthenticated code, allowing threat actors to take control over affected deployments.
Experts consider this to be the first critical flaw found since the finding of Log4Shell exploiting the same attack root but not being part of Log4j: “There are likely to be more packets affected by the same root cause as Log4Shell, accepting arbitrary JNDI search URLs. We have adjusted our automated vulnerability detection framework to account for the javax.naming.Context.lookup function as a dangerous function and released the framework in the Maven repository to find issues similar to Log4Shell2,” the researchers report.
The H2 database package was one of the first to be validated and reported to its developers, who immediately released a new version, available on GitHub. Experts add that several code paths in the H2 database framework pass unfiltered in attacker-controlled URLs to the javax.naming.Context.lookup function, which would allow remote loading of the code base.
In the report, H2 database users are asked to upgrade their deployments to the latest version available: “If you are running an H2 console that is exposed to your LAN, this issue is extremely critical and you should upgrade your H2 database to version 2.0.206 immediately,” JFrog adds.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











