Search engines are one of the most widely used computer tools worldwide, since any user can access the Internet regardless of their level of computer knowledge. Although tools such as Chrome, Edge or Firefox are the best known, other web browsers offer other kinds of functions and protections.
This time, cybersecurity awareness experts from the International Institute of Cyber Security (IICS) will show you the 10 search engines most used by cybersecurity professionals and even by some hacking groups.
As usual, we remind you that this article was written for informational purposes only and should not be taken as a call to action, so IICS is not responsible for the misuse of the information contained herein. With this in mind, let’s start looking at web browsers.
Shodan
Cybersecurity awareness experts consider Shodan to be one of the best search engines today. This tool allows getting information about any device connected to the Internet, including webcams, alarms, servers, routers, traffic lights and many other devices.
Shodan may collect information such as IP addresses, HTTP server headers, location, and device type, which can be used to find security flaws and fix them, or even exploit them.
Censys
Censys is a tool similar to Shodan in general terms as it also allows you to monitor devices connected to the Internet, collect their information and provide detailed reports to users.
According to cybersecurity awareness specialists, Censys can also be used to view real-time information about the various attacks to which computer systems are exposed, being able to detect services vulnerable to known failures.
Greynoise
Greynoise is somewhat different from the tools listed above, as it allows you to identify servers and users who scan networks for vulnerabilities using tools such as Shodan. Using this tool, it is possible to get information about malicious websites, types of attacks, and security breaches by simply entering an IP address or related words.
Wigle
This is a search engine for finding wireless networks and used to map wireless networks. Using this tool shows a map where we can enter a certain latitude and longitude in order to find all the networks of access points, WiFi devices and telecommunications antennas available in that area.
Zoomeye

Zoomeye is a navigation map to find vulnerabilities and active threats in networks and systems. It was developed mainly for the Chinese market and records numerous amounts of data collected from multiple sources, always ready for user consultation.
The tool can present statistics for all devices that can be accessed over the Internet from different countries, web browsers or servers.
Hunter
This is an internet search engine widely used by hacking groups to find unsecured email addresses. Hunter Search Engine can be used to search and retrieve all email addresses associated with a specific domain or organization.
During use, Hunter displays a list of email addresses that belong to the target domain, including their activity, as well as the public resources that were used for those addresses. The developers also created an API to test email ID deliverability and learn more about the organization.
PIPL
This is a useful Search Engine on the Internet to find information about a certain person, using as a reference general data associated with the person, such as phone numbers and email addresses, mention experts in cybersecurity awareness.
PublicWWW
This is a search engine designed to analyze any website for source code in HTML, CSS, JavaScript and other formats. Using PublicWWW, cybersecurity awareness experts can search websites based on their source code by simply providing a small piece of code; in response, the search engine will return a list of all websites that use similar code, which can prove very useful in subsequent analysis.
Have I Been Pwned
This tool is useful for both ethical hacking specialists and the general public, as it allows users to verify if an email address has been compromised in a cybersecurity incident.
The platform collects and identifies various database dumps and identifies exposed accounts, alerting the user to their compromised information or confirming that the email address or phone number is safe.
OSINT Framework
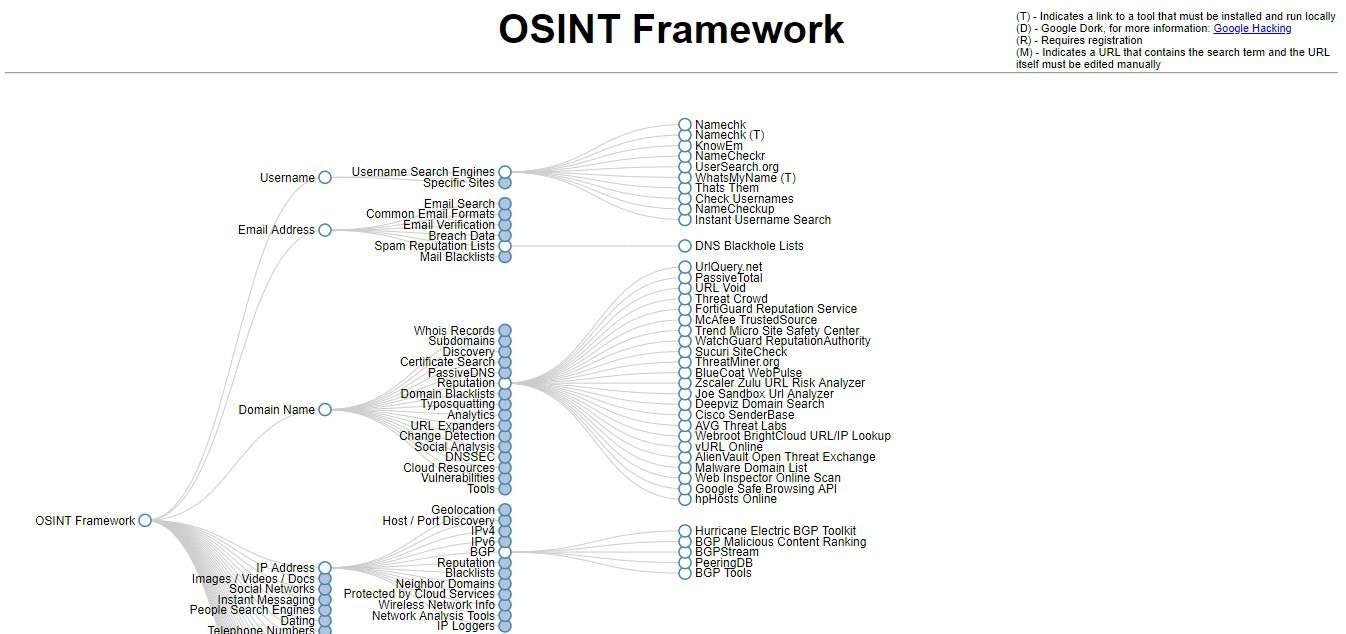
Open Source Intelligence Framework is capable of collecting information available from public sources, which is very useful for analysis and pentesting processes. This tool has a large number of menus and submenus, which allow you to obtain the desired results according to the goals of the research.
This cybersecurity framework is mainly employed by law enforcement and intelligence agencies in multiple countries, so it is constantly maintained and updated.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











