A recent report points to the detection of Bvp47, a backdoor for Linux systems developed by Equation Group, a group of threat actors allegedly linked to the U.S. National Security Agency (NSA). Although it was included in the VirusTotal database in 2013, this backdoor is still active and has remained hidden in countless deployments.
The first reports indicated that only an antivirus engine was able to detect a sample of Bvp47, although with the passage of the hours more indicators of compromise have been known, which will considerably improve the detection of this security threat.
The backdoor was first identified by Chinese security firm Pangu Lab, describing it as an advanced development for Linux with remote access capabilities protected through an RSA asymmetric cryptography algorithm, which requires a private key for enablement. This malware would have impacted almost 300 organizations in 45 countries, going unnoticed for almost 10 years.
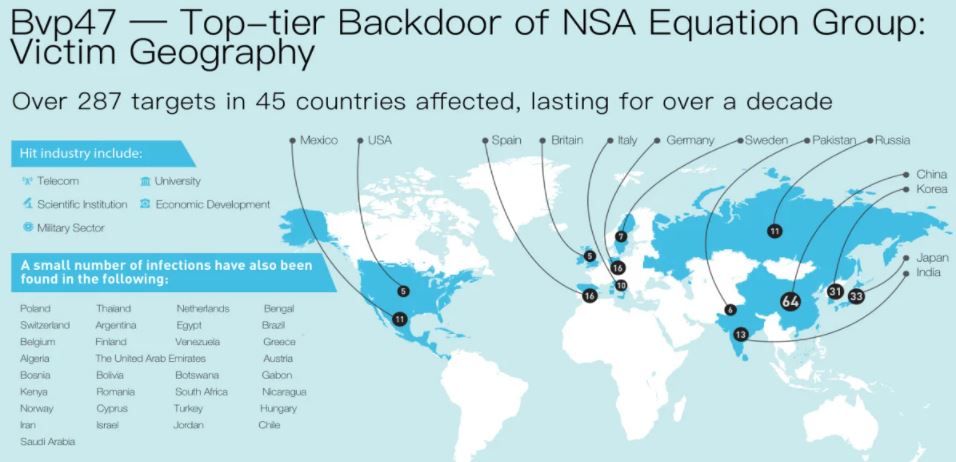
This private key was found in leaks published by Shadow Brokers hackers, in addition to other hacking tools and zero-day exploits used by Equation Group. The backdoor could also operate on major Linux distributions, including JunOS, FreeBSD, and Solaris.
A subsequent automated analysis seems to confirm the authorship of Bvp47, as it shares multiple features with another backdoor developed by Equation Group. According to Kaspersky experts, this backdoor shares 30% of the code strings with other malware identified in 2018 and available in virusTotal databases.
On the Bvp47 attack, the researchers point out that the threat actors control 3 servers, one responsible for the external attacks and two other internal machines in charge of an email server and a business server.
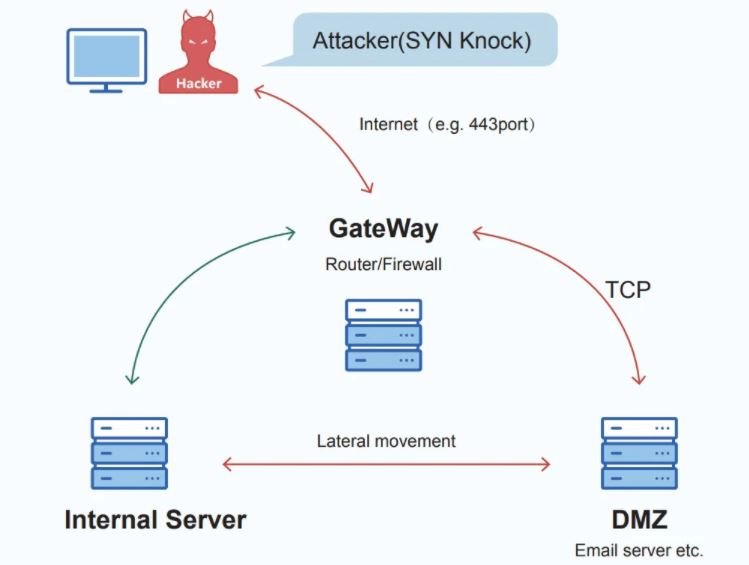
Attackers establish a connection between the external server and the email server via a TCP SYN packet with a payload of 264 bytes. The email server then connects to the commercial server’s SMB service to perform some sensitive operations, including running PowerShell scripts.
The trading server then connected to the email server for the download of additional files, including the Powershell script and the encrypted data from the second stage. The connection between the internal machines allows the transmission of encrypted data through a specialized protocol.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











