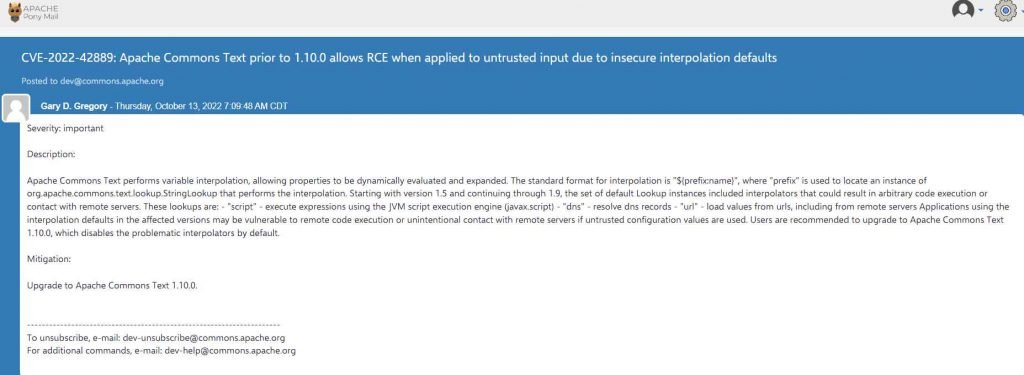
An update to the Apache Commons Text library addresses a major vulnerability that may have allowed remote code execution, according to the Apache Software Foundation (ASF).
Alvaro Munoz’s issue, CVE-2022-42889, originally reported on the Apache dev list on October 13, 2022.
The vulnerability is being related to the Log4Shell vulnerability, which affects Apache Log4j 2, a well-liked Java library used to log application error messages. But based on study by several security researchers (as of this writing), it doesn’t appear to have the same impact as the Log4Shell issue.
Versions 1.5 through 1.9 of Apache Commons Text are impacted by CVE-2022-42889. As of Commons Text version 1.10, the vulnerability has been addressed by the Apache team.
The variable interpolation mechanism of Commons Text has an insecure implementation, which leads to CVE-2022-42889.
Because it uses the same sort of attack code as Log4Shell, this vulnerability is frequently referred to as Text4Shell or Text2Shell. Compared to Log4J, Apache Commons Text is a significantly less popular library. However, in this instance, Apache Commons Text does not by default validate the data to be processed, which implies that if no filter has been added to the susceptible application code, malicious code can be run.
The Apache Commons Text vulnerability, CVE-2022-42889 (Text4Shell / Text2Shell), may be exploited by introducing a malicious payload into the insecure program, which will request information from a third-party source, using DNS, or by executing a script.
The following JDK version was used by the rapid7 team to test their proof-of-concept:
JDK 1.8.0_341 – PoC works
JDK 9.0.4 – PoC works
JDK 10.0.2 – PoC works
JDK 11.0.16.1 – warning but works
JDK 12.0.2 – warning but works
JDK 13.0.2 – warning but works
JDK 14.0.2 – warning but works
JDK 15.0.2 – fails
JDK 16.0.2 – fails
JDK 17.0.4.1 – fails
JDK 18.0.2.1 – fails
JDK 19 – fails
Although the Nashorn engine was disabled, the JFrog Security team emphasized that Java 15+ users are protected from code execution since $script interpolation won’t function. However, other vectors (DNS, URL) will continue to operate.
Since the vulnerability is not expected to have as great of an impact as Log4Shell, we also highly advise updating Apache Commons Text to the corrected version 1.10.0.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










