For virtual environments built on VMware vSphere, Nutanix AHV, and Microsoft Hyper-V hypervisors, Veeam Backup & Replication is a proprietary backup application. For systems like Exchange and SharePoint, it can safeguard and restore specific data and programs in addition to backing up and restoring virtual machines.
The team at CloudSEK has examined a number of serious and significant flaws impacting Veeam Backup & Replication. The fully customized tool enabling remote code execution to take advantage of the Veeam Backup & Replication flaws has been spotted being advertised by a number of threat actors.
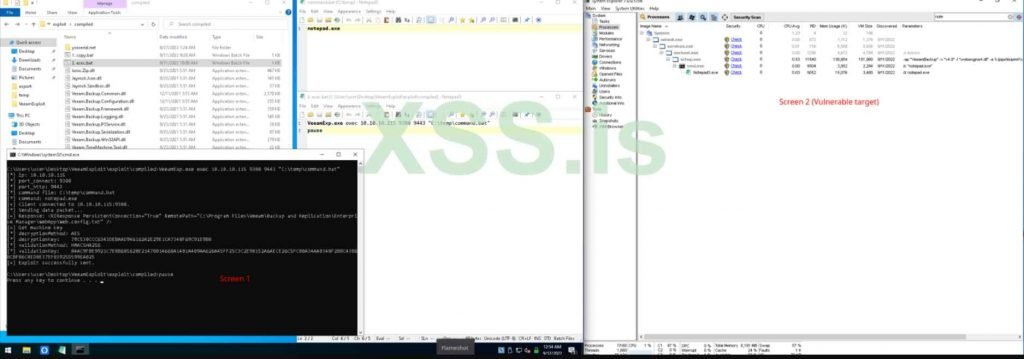
Copying files inside the locale or from a distant SMB network, RCE without authorization (‘Network Service’ rights), and RCE/LPE without authorization (‘Local System’ rights) are all possible as a result of the aforementioned CVEs being successfully exploited.
The Monti and Yanluowang ransomware gangs were discovered using “Veeamp” malware in the wild to steal usernames and passwords from a Veeam backup management software SQL database.
The malicious file is a 32-bit.NET program that, when launched, tries to establish a connection with the VeeamBackup SQL database and executes SQL command. Following successful decryptions, the “Veeamp.exe” credential dumper publishes the Username, Encrypted Password and the Decrypted Password.
CVE-2022-26500 and CVE-2022-26501- 9.8 CVSS V3 score
Veeam Distribution Service has a remote code execution flaw. Exploiting these hackers can access internal API operations by using the Veeam distribution service, which uses TCP 9380 with the default settings, even if they are not authorized.
Malicious actors can remotely run malware without being authenticated thanks to this component.
CVE-2022-26504- CVSS V3 score of 8.8
Veeam Backup PSManager contains a vulnerability for remote code execution. Threat actors who are not administrators are able to authenticate using domain credentials when utilizing Backup.PSManager.exe’s using TCP port 8732.
Through the use of vulnerable components, attackers are able to remotely execute malware, taking over the network.
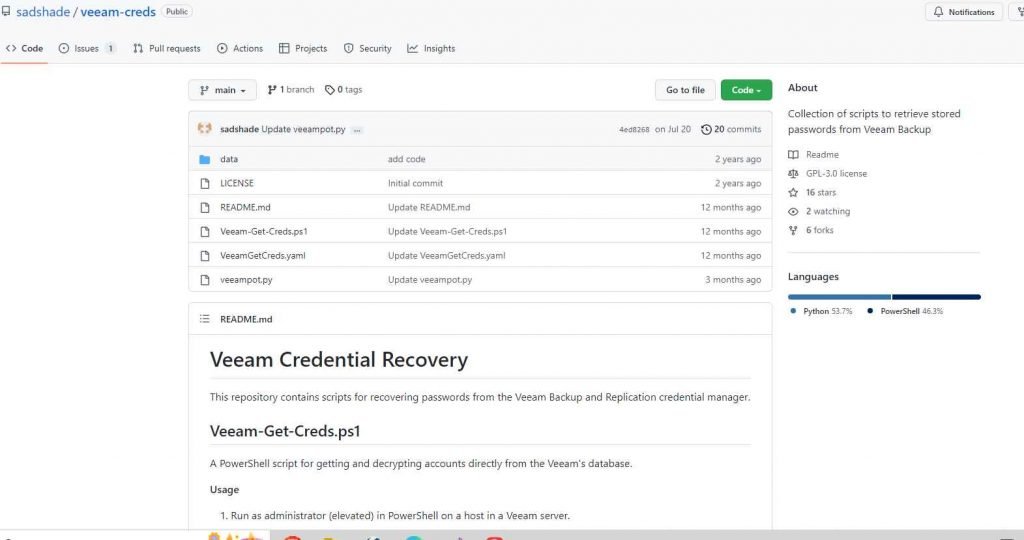
Additionally, there is “veeam-creds” GitHub repo enables password recovery from the Veeam Backup and Replication credential management.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











