Rackspace, a provider of cloud computing services, has admitted that it was the victim of a ransomware incident, which resulted in the business being forced to shut down its Hosted Exchange environment. Since Friday, December 2, the hosted Microsoft Exchange service provided by Rackspace has been experiencing a variety of issues. The affected environment was taken down by the business, and on Saturday the company admitted that a security breach had occurred.
The company made the announcement on Tuesday morning that the suspicious behavior that had caused the outage was the result of a cyberattack utilizing ransomware. We investigated the leak websites of some of the most prominent ransomware gangs, however they do not mention Rackspace anywhere on their sites. However, given the recent nature of the occurrence, the perpetrators of the cybercrime are most likely still attempting to bargain with the business in question before adding it to their website and making the threat to disclose stolen data.
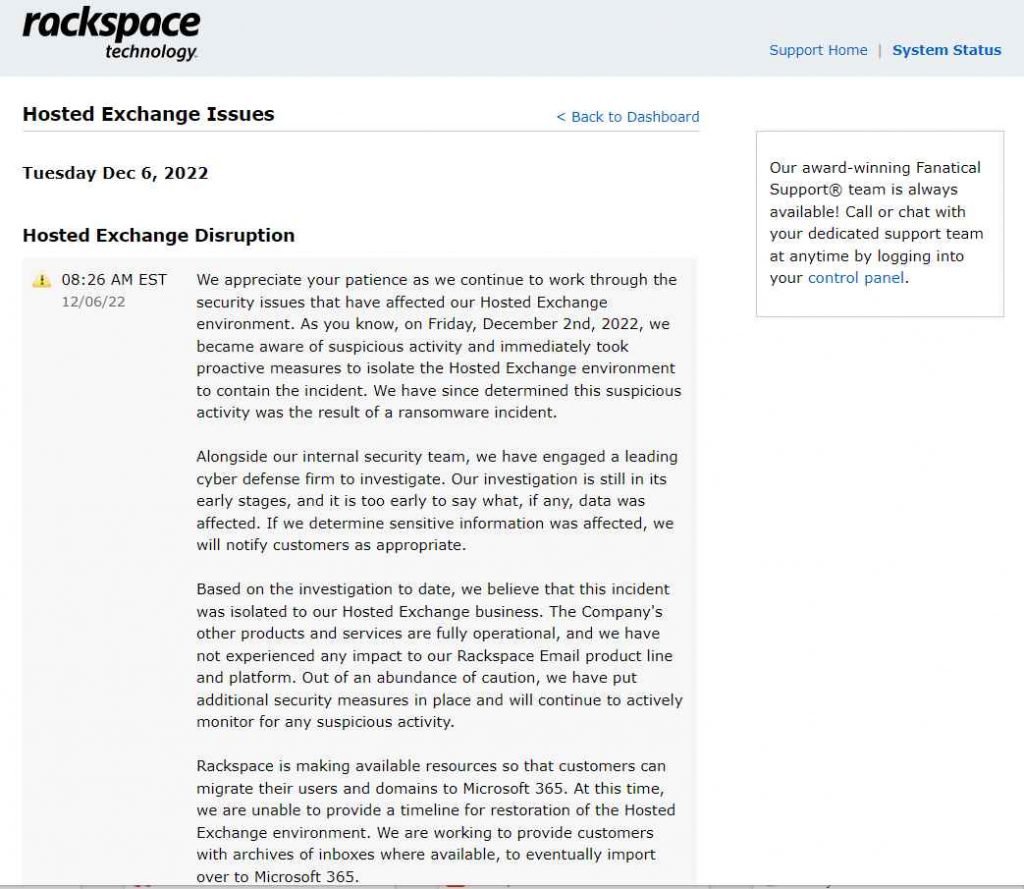
Rackspace has said that it is too soon to determine if any customer data has been accessed inappropriately. It is likely dependent on how long the hackers were able to remain hidden inside the company’s systems until the intrusion was discovered. Rackspace has said that they would tell its customers in the right manner “if we establish that sensitive information was impacted.”
“On the basis of the investigation that has been conducted to this point, we think that this problem was restricted to our Hosted Exchange business. The statement went on to say that the company’s other offerings and services are fully functioning, and that the Rackspace Email product line and platform have not been affected by the outage in any way.
Customers who were impacted by this Rackspace outage have been given the instruction to migrate their email services to Microsoft 365. According to the company’s statement, it was successful in restoring email services for thousands of clients using Microsoft 365.
Cyber security researchers, speculates that the event may have included the exploitation of vulnerabilities in Microsoft Exchange listed as CVE-2022-41040 and CVE-2022-41082, together referred to as ProxyNotShell.
Late in the month of September, a Vietnamese cybersecurity organization discovered ProxyNotShell while seeing the vulnerability being abused in the field. Microsoft has acknowledged the vulnerability and established a connection between it and a state-sponsored hacking organisation.
The IT giant moved quickly to disseminate mitigations, but specialists demonstrated that it was simple to get around them. November was the sole month in which Microsoft issued fixes.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











