EvilExtractor is an attack tool that is meant to target Windows operating systems to extract data and files from endpoint devices. EvilExtractor is also occasionally written Evil Extractor. It comes with a number of modules, all of which operate over an FTP service. It was created by a firm known as Kodex, and according to the company, it may be used as a teaching tool. However, research carried out by FortiGuard Labs demonstrates that fraudsters are actively using it as a means of information theft.
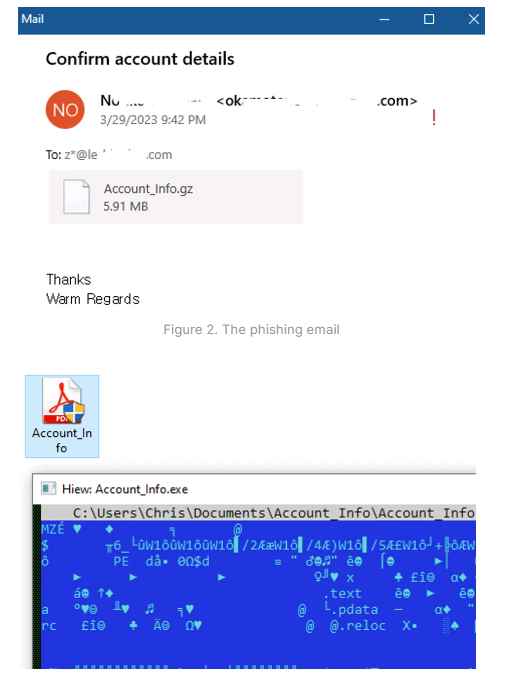
According to the data collected on the sources of traffic going to the site, evilextractor[. ]com in March 2023, malicious activity saw a considerable uptick. On March 30th, experts discovered malware in a phishing email campaign, and they were able to link back to the samples of this. Typically, it will appear to be a valid file, such as an Adobe PDF or a file from Dropbox, but as soon as it is loaded, it will start using PowerShell to do malicious operations. In addition to that, it has features for monitoring the environment and preventing virtual machines. Its major function seems to be to collect browser data and information from endpoints that have been hacked, which it subsequently sends to an FTP server controlled by the attacker.
The researchers saw an increase in the number of attacks that disseminated the virus in the month of March 2023. The majority of infections were recorded in the United States and Europe.
An individual who uses the alias Kodex online is the one who advertises and sells the tool on cybercrime message boards. The program’s creator first made it available in October 2022 and is continually expanding its capabilities by adding new modules that come equipped with advanced capabilities.
The malicious software has the ability to steal sensitive data from the infected endpoint, such as the browser history, passwords, cookies, and more. Additionally, the malicious software is able to record keystrokes, activate the camera, and take screenshots. The specialists have discovered that the malware also has a ransomware function that is known as “Kodex Ransomware.”
The security analysts discovered a phishing effort that included a malicious attachment in the form of a PDF file that was disguised as a request to confirm an existing account. The perpetrator of the attack gets the victim to open the attachment by tricking them into clicking on the PDF icon.
It has been discovered that EvilExtractor is being used as a complete information stealer with numerous harmful characteristics, including ransomware. It is possible for a PowerShell script to avoid detection when run using a.NET loader or PyArmor. Within a relatively short period of time, its creator has improved the system’s reliability and updated a number of its functionalities. This blog post demonstrates how threat actors initiate an attack using phishing mail and identifies the files that are used to extract the EvilExtracrtor PowerShell script. In addition to this, they went through the functionalities that are available, the kind of information that may be gathered by EvilExtractor, and how the Kodex Ransomware operates. Users need to be aware of this new information stealer and should continue to exercise extreme caution when it comes to e-mails that seem to be suspicious.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











