Windows Zero-Day Affecting All OS Versions on Sale for $90,000
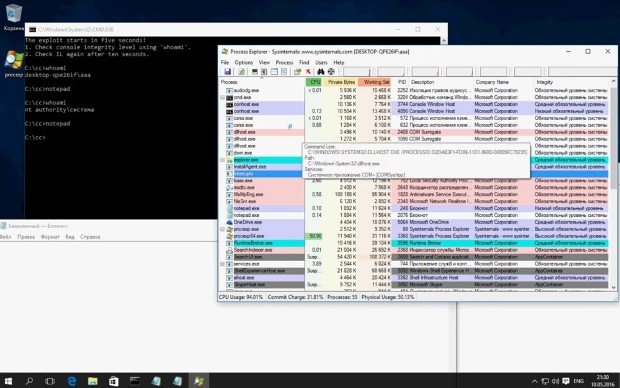
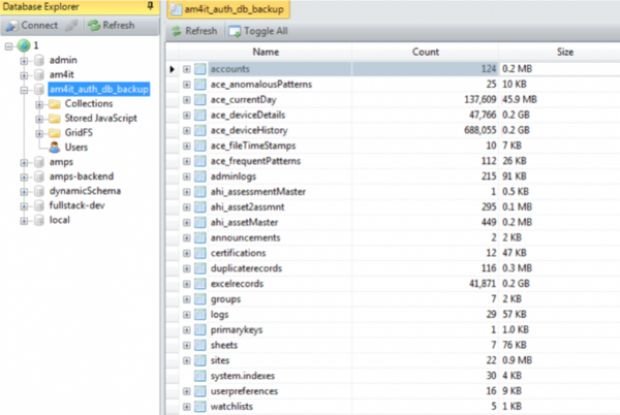
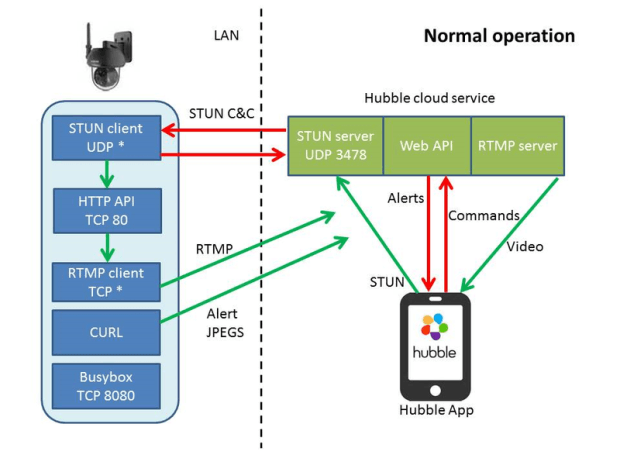
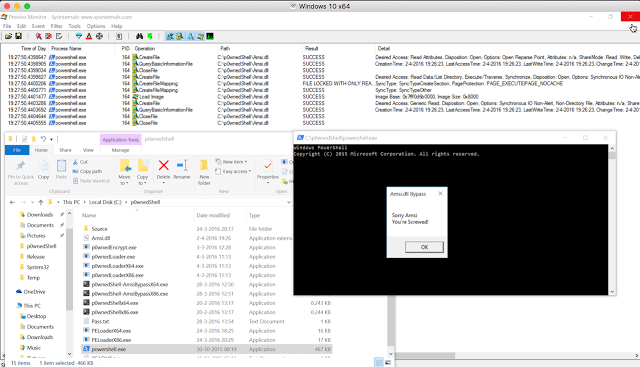
Over 1.5 billion users in danger thanks to new exploit. A hacker going by the handle BuggiCorp is selling a zero-day vulnerability affecting all Windows OS versions that can allow anRead More →