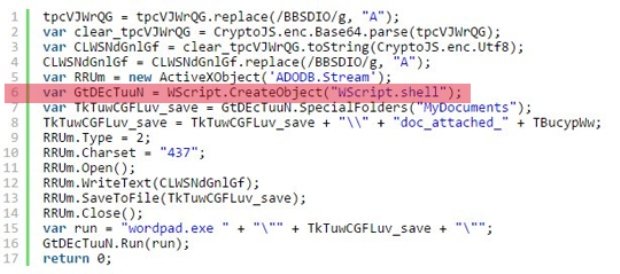
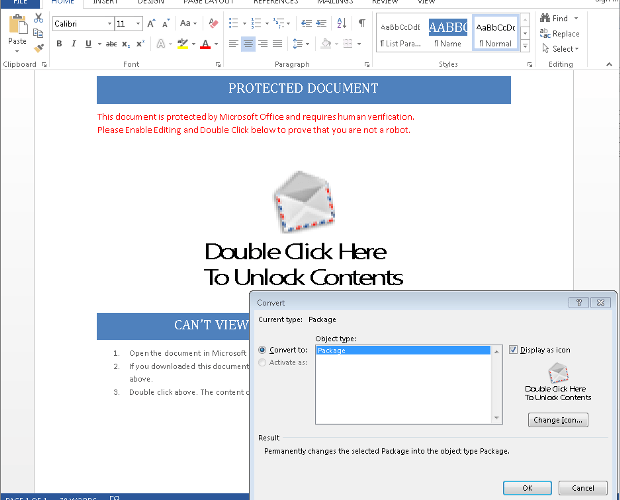
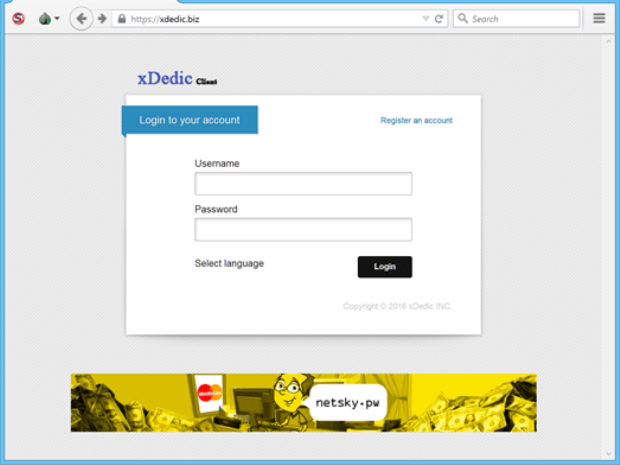
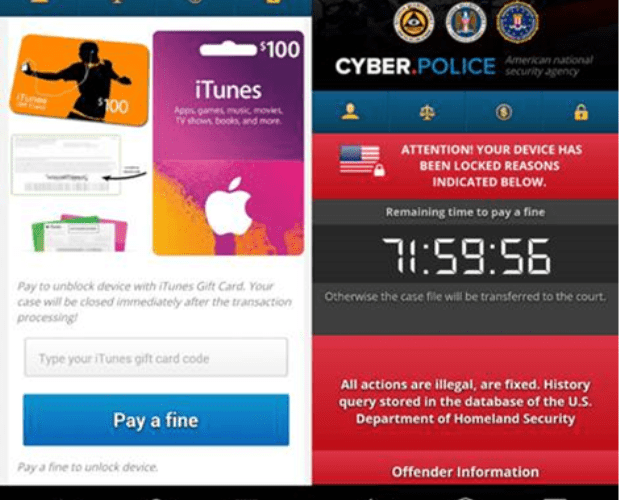
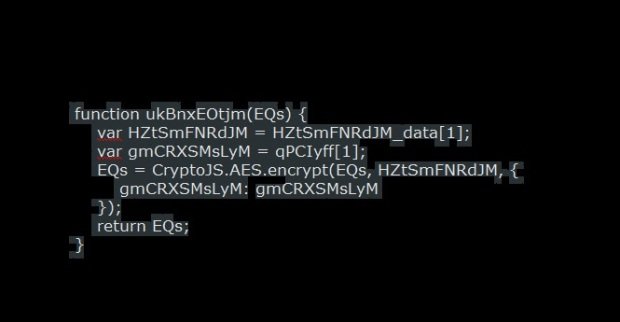
JScript-toting Ransomware Can Steal Your Passwords and Bitcoin Wallets, Too
In an effort to develop a target base and increase the conversion rate of victims, ransomware perpetrators will try to veer away from well-known families and create new family sportingRead More →