Facebook Password Recovery Software
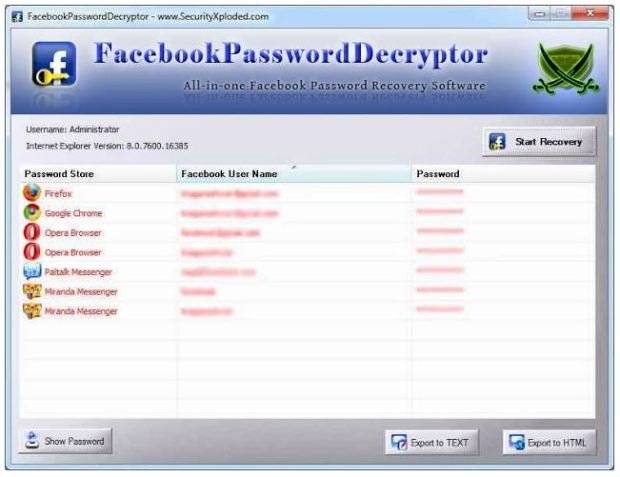
Facebook Password Decryptor is the free software to instantly recover Facebook account passwords stored by popular Web Browsers and Messengers, information security training expert said. Here is the complete list of supportedRead More →