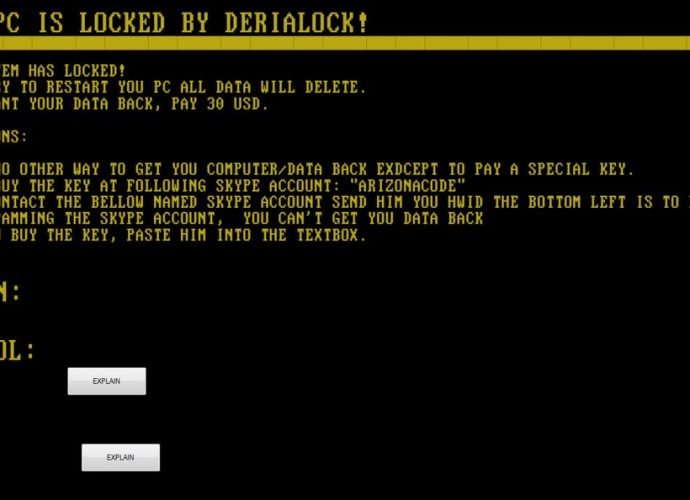
New DeriaLock Ransomware Active on Christmas, Includes An ‘Unlock All’ Command
Today, on Christmas Eve, G Data malware analyst Karsten Hahn has come across a new ransomware family named DeriaLock, which locks your screen and requests a payment of $30. RansomwareRead More →