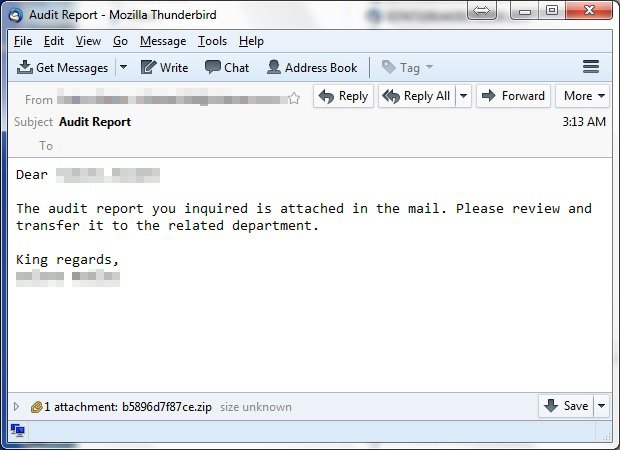
Armenian Hackers Leak Azerbaijani Banking and Military Data
ARMENIAN HACKERS LEAKED PERSONAL DETAILS OF GOVERNMENT OFFICIALS AND ALSO DEFACED EMBASSY SITES TO CELEBRATE 25 YEARS OF ARMENIAN INDEPENDENCE. Armenian hackers from Monte Melkonian Cyber Army (MMCA) have leaked a trove ofRead More →