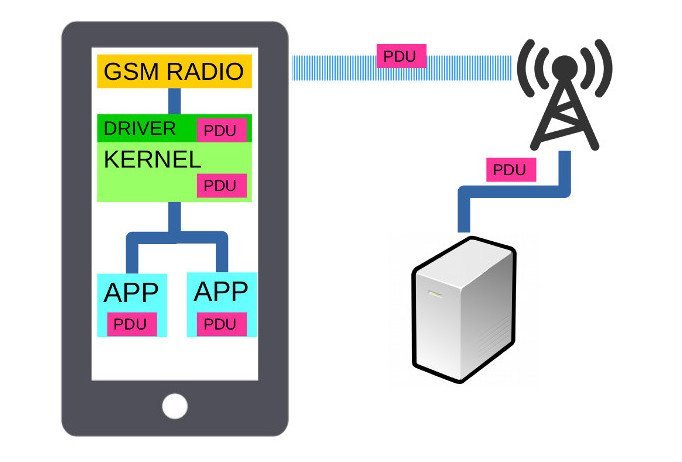
Binary SMS – The old backdoor to your new thing
Despite being older than many of its users, Short Messaging Service (SMS) remains a very popular communications medium and is increasingly found on remote sensors, critical infrastructure and vehicles dueRead More →