New Python ransomware called HolyCrypt Discovered
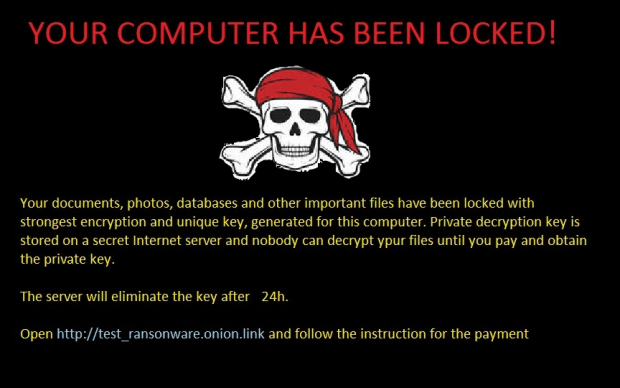
A new ransomware has been discovered by AVG malware analyst @JakubKroustek called HolyCrypt. This ransomware is written in Python and compiled into a Windows executable using PyInstaller. This allows the developer to distributeRead More →