Captain Hook: Pirating AVs to Bypass Exploit Mitigations
2016-07-21
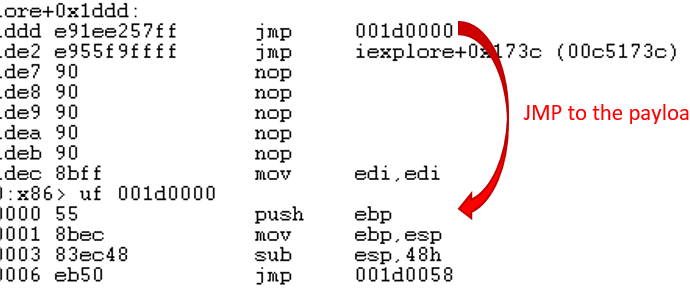
tl;dr: We found 6(!) different common security issues that stem from incorrect implementation of code hooking and injections techniques. These issues were found in more than 15 different products. TheRead More →