A new variant of mobile ransomware that encrypts the content of Android smartphones is putting a new spin on both how it communicates with its masters and how it spurs its victims into action. The updated version of Simplocker masquerades on app stores and download pages as a legitimate application, and uses an open instant messaging protocol to connect to command and control servers.
The malware requests administrative permissions to sink its hooks deep into Android. Once it’s installed, it announces itself to some victims by telling them it was planted by the NSA—and to get their files back, they’ll have to pay a “fine.”
Ofer Caspi of Check Point’s malware research team wrote in a report posted this week that the team has “evidence that users have already paid hundreds of thousands of dollars to get their files “unencrypted” by this new variant. He estimates that the number of infected devices so far is in the tens of thousands, but may be much higher. Because the software can’t easily be removed once it is installed, and because the files it encrypts can’t be recovered without it, victims have no choice but to either pay $500 to get their files decrypted or to wipe the device and start from scratch.
While posing as a legal or governmental authority to intimidate the victim into paying up is not new, the use of Extensible Messaging and Presence Protocol (XMPP), the instant messaging protocol used by Jabber and previously by GTalk, is a shift in tactics to evade detection by anti-malware tools. XMPP communication makes it more difficult for security and anti-malware tools to catch the ransomware before it can communicate with its command and control network because it conceals the communication in a form that looks like normal instant message communications.
Most previous ransomware packages have communicated with a website over HTTPS to obtain encryption keys; those websites can generally be identified by their URLs, IP addresses, or the signature of their Web requests and then blocked. An application making a secure HTTP request to a suspicious destination would be a good sign that something bad was afoot. But the XMPP communications channel used by the new Simplocker variant uses an external Android library to communicate with the command and control network through a legitimate messaging relay server. And these messages can be encrypted using Transport Layer Security (TLS). The messages were pulled from the command and control network by the operators of the scheme via Tor.
By reverse-engineering a sample of the malware, Check Point researchers were able to tap into its XMPP communications channel.
“During our investigation, we successfully obtained hundreds of thousands of XMPP messages sent between the C&C servers and the infected mobile devices,” Caspi wrote. “After breaking the obfuscation scheme implemented in these messages, we were able to read most of the message contents. This led us to obtain evidence that suggests that there are tens of thousands of devices infected with this malware. We also observed that ~10% of the users paid between $200 and $500 in ransom to decrypt their files. This means that for every 10k infections, the malware authors raked in $200k-$500k. While these numbers are stunning, this might just be the tip of the iceberg, as our dataset is incomplete and the actual infection rate is probably much higher.”
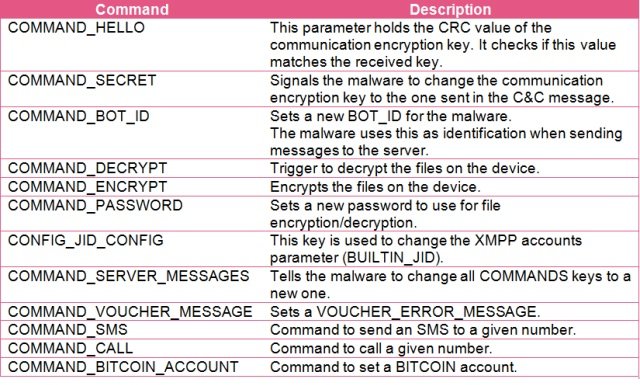
The XMPP channel allows a number of other commands to be launched remotely by the malware operators, including sending SMS messages and placing phone calls, as well as re-setting the configuration of the malware’s communications (and the Bitcoin account to be used to submit victims’ payments). The malware also had localized versions of its ransom demands for Saudi Arabia, the United Arab Emirates, and Iran, each using appropriately themed faked warnings from those countries’ governments to victims.
Check Point has informed the operators of the XMPP relay servers being used by the ransomware, providing details that will allow those service providers to block traffic that provides the malware with the encryption keys needed to launch an attack. However, new versions of the malware “are still appearing almost every day,” Caspi warned.
Source:https://arstechnica.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











