One thing you might not know about hackers is that besides cracking some virtual systems many of them are fond of hacking real world stuff as well. One thing of particular interest for them is naturally locking systems. For instance, lockpicking contests and related talks are a common thing at hacker conferences such as DEF CON or Chaos Communication Congress.

At the recent 32C3 conference in Hamburg, Eric Wustrow, a professor at the University of Colorado, presented a report describing how 3D printers can be used to forge keys. To be precise, for the forgery of keys for pin tumbler locks, which is probably the most common lock system.
Before 3D printing was invented, in order to make a copy of a key one had to be skilled in metalcraft or at least in programming some CNC machine tools. Besides that, restrictions included unavailability of certain blank keys, necessity of physical access to key one wanted to forge and others physical world limitations. Obviously, 3D printing makes everything easier and cheaper, since it transfers some of the problems to digital plane.
But how exactly can a 3D-printed key be used to attack a pin tumbler lock? There are at least three attack models (or as they say in cyber-security world, ‘attack vectors’) this type of locks is vulnerable to.
First of all, it’s teleduplication of a key. Modern cameras’ sensors have huge resolutions, so even bad digital photo can contain more than enough information to make a 3D model of a key and print a replica. Moreover, modern telescopic lenses are so good (and relatively affordable), that this picture can be shot from a very impressive distance.

Second attack model is lock bumping, a technique that involves using a specially crafted bump key with deep cuts and some sleight of hand. It turns out, that plastic 3D printed bump keys can be even a better choice than the metal ones, since plastic transmits a knock better, bumping makes less noise, and risk of damaging the lock is reduced. And of course making a 3D model and printing a plastic key is way less complex than messing with metalcraft.
The third scenario is probably the most interesting one: it is aimed towards master key systems and thus called by Wurstow ‘Privilege escalation’ resembling computer hacking technique of the same name. The core idea of master key systems widely used by organizations is to make a lock ‘compatible’ with two different keys at once. To achieve that, locks manufacturers use two sets of pins inside a lock. Usually the so-called master key is in turn compatible with several locks, because one of the pin sets in them is made identical.
The problem is, that the sets of pins are not completely independent. If the attackers have a regular key which opens one of locks in question, they can modify one of its cuts and try to open the lock. If it doesn’t work, they need to modify the cut again, and keep modifying it until the alternative, ‘master key pin’ is in place and the lock is opened. All the other cuts are correct for this particular door, because they still conform to the ‘regular’ pins.
In such a way, one by one, attacker can modify all the cuts and get a master key that opens every door as a result. In this case 3D-printing could be especially helpful to the attacker since this scenario involves a lot of attempts and each of them requires a new modified key sample.

But are 3D-printed keys that good to work in real life? As a study shows, not all the substances used in 3D-printing are strong enough, some of them are too flexible, some of them are too fragile. But there certainly are some substances suitable for keys forgery. Moreover, for those who are not sure whether plastic will stand it or not, there are certain 3D-printing services which offer printing in metals such as brass, steel or even titanium.

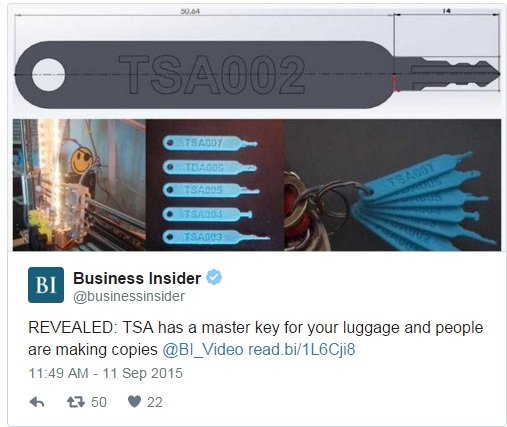
It is worth mentioning that 3D printed keys are not just a theoretical problem. The software for key forgery with 3D-printing technology is already in the wild, so are the 3D printers themselves. The most obvious case is TSA master keys leak. Several months ago someone has posted an image with TSA keys set on the web — 3D printable models followed immediately. And now anyone can download them and print their very own set of ‘Approved Luggage Locks’ keys
So, what can we do to defend? Probably, the good way of thinking about this cyber-physical issue is to implement the same strategy that people use to protect IT systems. You can think of your keys as of real-world passwords and treat them accordingly. Thus we come to several simple rules that won’t secure your lock for 100%, but at least will impede the attack enough to make the attacker rather go away:

1. Don’t use simple ‘passwords’. As you can see, common pin tumbler locks are rather weak and vulnerable, not exactly like ‘123456’ or ‘john1975’, but pretty close to it. If you need better protection, choose more complex lock systems.
2. Use ‘two-step authentication’. Two locks of different types could work much better than the only one lock.
3. Don’t expose your ‘passwords’. Keep your keys off from cameras and of course never post photos of your keys online. Even a bad photo could be enough to 3D-replicate your key.
4. Master-keys are pretty much like ‘backdoors’ at your organisation’s door locks. Avoid using such systems in critical rooms’ and areas’ doors.
5. It won’t hurt to use a security solution: alarm systems can protect you from burglary if attackers are persistent enough to overpass all above mentioned security means.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











