The way users move fingers across a phone’s touchscreen alters the WiFi signals transmitted by a mobile phone, causing interruptions that an attacker can intercept, analyze, and reverse engineer to accurately guess what the user has typed on his phone or in password input fields.
This type of attack, nicknamed WindTalker, is only possible when the attacker controls a rogue WiFi access point to collect WiFi signal disturbances.
Control over the WiFi access point is also imperial since the attacker must also know when to collect WiFi signals from the victim, in order to capture the exact moment when the target enters a PIN or password.
The attacker can achieve this by using the access over the WiFi access point to sniff the user’s traffic and detect when he’s accessing pages with authentication forms.
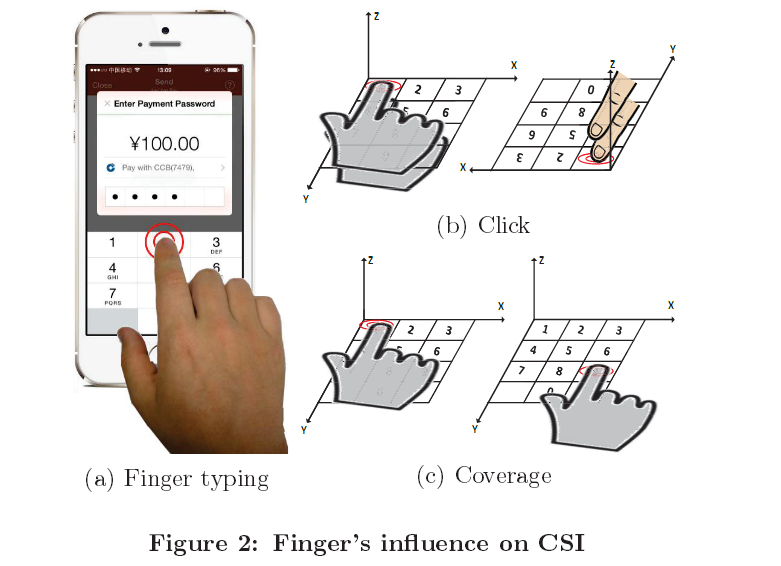
The attack sounds futuristic, but it’s actually leveraging radio signals called CSI (Channel State Information). CSI is part of the WiFi protocol, and it provides general information about the status of the WiFi signal.
Because the user’s finger moves across the smartphone when he types text, his hand alters CSI properties for the phone’s outgoing WiFi signals, which the attacker can collect and log on the rogue access point.
WindTalker attack has a 68%+ accuracy
By performing basic signal analysis and signal processing, an attacker can separate desired portions of the CSI signal and guess with an average accuracy of 68.3% the characters a user has typed.
WindTalker’s accuracy is different based on smartphone models, but it can be improved the more the user types and the more data the attacker collects.
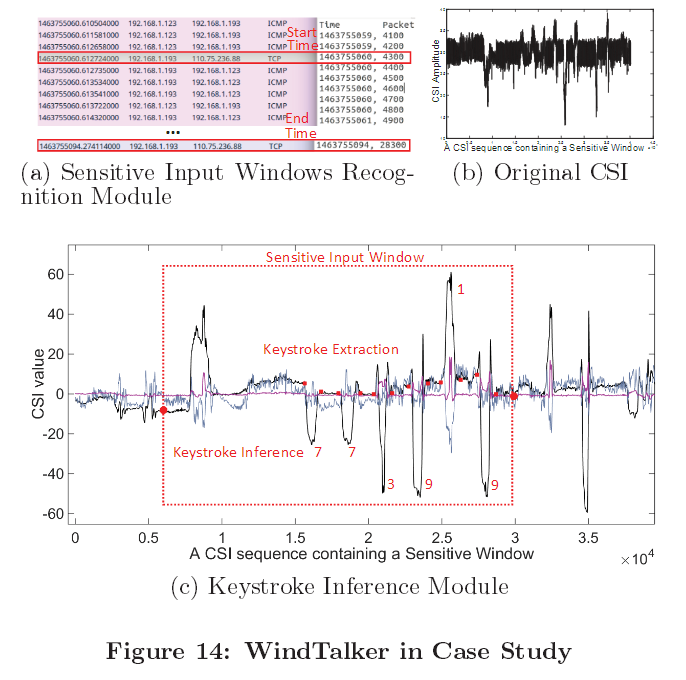
Researchers tested WindTalker in a real-world scenario by recovering the transaction PIN users need to enter to authorize AliPay mobile transactions, which are in most cases sent to a fixed range of IPs that the attacker can detect and use to initiate the PIN WiFi signal collection procedure.
Details about the real-world attack and WindTalker, in general, are available in a research paper titled “When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi Signals.”
The WindTalker attack was also presented at the 23rd ACM Conference on Computer and Communications Security, held in Vienna, Austria, at the end of October. The ACM CCS presentation is also available on YouTube, embedded below.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











