In a report released on Tuesday, Akamai says it spotted DDoS attacks leveraging the CLDAP protocol for the first time, and attacks using this protocol have the potential to incur serious damage, based on the opinion of its experts.
The CLDAP protocol, defined by RFC 1798 and replaced by RFC 3352, is an alternative to the LDAP protocol from Microsoft, used to connect, search, and modify share Internet directories.
While both protocols work on port 389, LDAP works via TCP, while CLDAP, as its name implies — Connection-less Lightweight Directory Access Protocol — works via UDP.
First DDoS attacks using CLDAP detected last year
According to Akamai, during October 2016, the company started detecting DDoS attacks carried out via an unfamiliar protocol, which was CLDAP. This was happening at the same time when DDoS mitigation firm Corero announced it also discovered DDoS attacks leveraging LDAP.
According to the Akamai report released this week, both protocols appear to have been used in similar manners, which was for amplified DDoS reflection attacks.
These types of attacks happen when an attacker sends an LDAP or CLDAP request to a LDAP server with a spoofed sender IP address (the victim’s IP).
Based on the attacker’s LDAP/CLDAP query, the server responds with its own data, which it inserts into the response packet. Because the attacker used IP spoofing, this unsolicitated & bulked-up response is sent to the target’s IP, causing the DDoS attack, as the victim’s machine can’t process massive amounts of LDAP/CLDAP data at the same time.
CLDAP and LDAP DDoS attacks have massive amplification factors
This is the reflection part of the attack. The amplification part, or the amplification factor is the number of times a packet is enlarged while processed by the LDAP server.
For both the LDAP and CLDAP protocols, this amplification factor is quite substantial. Normally, other protocols susceptible to amplified reflection DDoS attacks have an amplification factor of around 10, meaning a packet of 1 byte is bounced off the vulnerable server and amplified to 10 bytes.
According to Corero, for LDAP, the amplification factor is 46, on average, and up to 55 at peak conditions.
CLDAP attacks are slightly more powerful, with an amplification factor of 56, on average, and 70 at peak conditions.
50 DDoS attacks using CLDAP detected
Akamai says that since October 14, 2016, when the first CLDAP-based DDoS attack was seen, there have been 50 attacks in total, coming from 7,629 unique CLDAP reflectors (LDAP servers with port 389 exposed to the Internet).
The biggest of this was of 24 Gbps, more than enough to bring down a website, which usually falls around 1 Gbps.
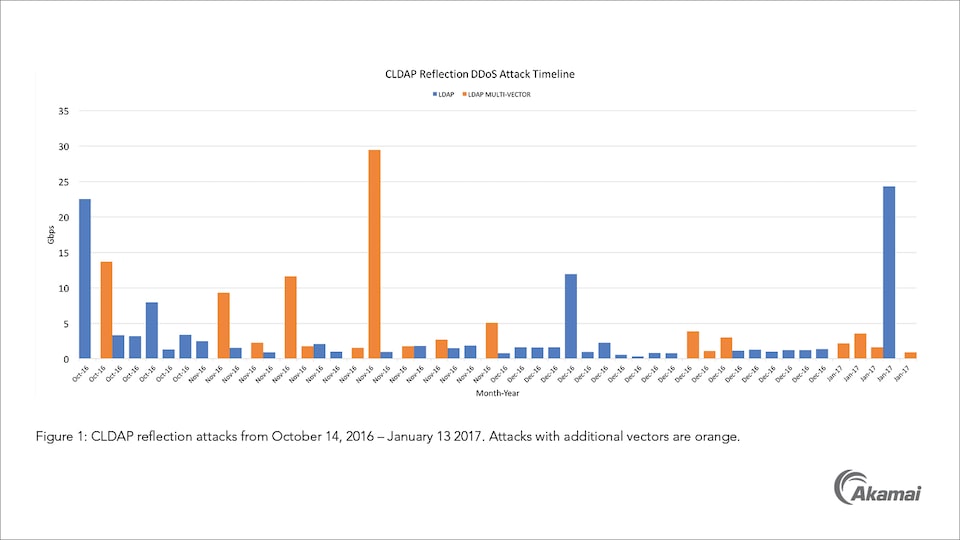
The vast majority of these attacks, 33, were single vector attacks, meaning 100% pure CLDAP requests, with no other protocols involved. This is uncommon, as most DDoS attacks use multiple protocols in order to avoid DDoS protection systems.
Someone testing a new DDoS cannon?
The low number of CLDAP attacks detected during the last six months, and the high percentage of pure CLDAP DDoS attacks lends us to believe that a threat actor was testing CLDAP’s feasibility for DDoS attacks.
With amplification factors going as high as 55 and 70, LDAP and CLDAP stand to become very popular with DDoS-for-hire services. Currently, there are 250,000 devices with port 389 exposed to the Internet, according to Shodan.
In the past two years, security researchers have discovered other protocols susceptible to amplified DDoS reflection attacks, such as NetBIOS, RPC, Sentinel, DNSSEC, and TFTP. Generally, UDP-based protocols are susceptible to these types of attacks.
source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











