The Shadow Brokers have published a new message today, gloating about the damage caused by the NotPetya ransomware, and threatening to expose the real-life identity of an alleged NSA employee, who they say has been mocking the group on Twitter.
In their message, the group also boasted about have “many many subscribers” to their monthly data dump service, which they started earlier this month.
Based on this premise, the group announced that starting next month, with July, anyone who wants to subscribe to their service and receive zero-day exploits via email must now pay double, a sum of 200 Zcash, or around $33,000.
The group’s announcement also included details about an upcoming “VIP Service,” which the group has set up after several individuals approached the group with requests and questions about certain exploits or data dumps.
“For one time payment of 400 ZEC you getting theshadowbrokers VIP attention,” the group wrote today in their usual and intentional broken English. The group says that no data is guaranteed, so basically, VIP members would be paying only for the honor to ask the group a few questions.
Shadow Brokers threaten to dox alleged NSA hacker
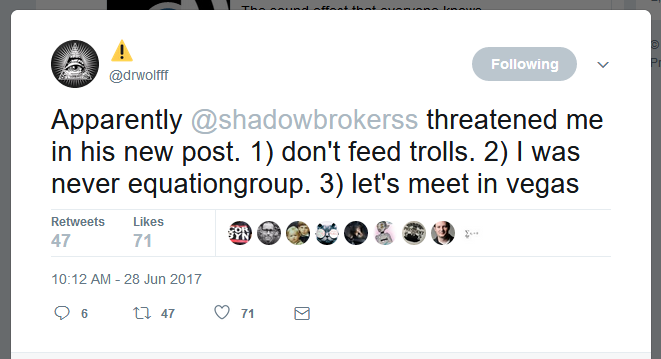
While these are interesting wrinkles in the Shadow Brokers’ ongoing operation, the most intriguing part of their announcement was a large section where they spent their time threatening a Twitter user, who they claim is a former Equation Group (codename given to NSA) member.
“‘Doctor’ person is writing ugly tweets to theshadowbrokers […] Then “doctor” person is deleting ugly tweets,” the group wrote. “TheShadowBrokers is thinking ‘doctor’ person is former EquationGroup developer who built many tools and hacked organization in China. TheShadowBrokers is thinking “doctor” person is co-founder of new security company and is having much venture capital.”
The Shadow Brokers continued by threatening to reveal “Doctor”‘s real identity if he doesn’t sign-up for July’s Shadow Brokers dump using an email address of “doctor@company-name.com,” effectively blackmailing the Twitter user to pay up or getting doxed.
Alleged NSA employee denies everything
The Twitter user, @drwolfff, reached out to this reporter today, admitting he was the one the Shadow Brokers had mentioned in their posts.
Both on Twitter, and in a private conversation with Bleeping Computer, the Drwolfff denied he was an NSA employee, and that he created any cyber tools for the NSA. He also later denied of owning a cyber-security startup.
When asked if the Shadow Brokers might be mad at him for exposing cyber-espionage operations that the Shadow Brokers might have orchestrated in the past, Drwolfff said “it’s possible, but I wouldn’t know because I am 100% defense.”
The researcher believes the Shadow Brokers are mad at him for “making fun of their fake accent and bad grammar.”
Many security and intelligence analysts have claimed the Shadow Brokers is a man/group that’s intentionally distorting his grammar in order to disguise linguistic clues.
While many have pointed the finger at a Russian operative, there are other experts that claim a former NSA contractor is behind the group’s operations. “I think he is former NSA,” Drwolfff said echoing some of these theories.
Twitter user says he’ll dox himself
Furthermore, the Drwolfff believes the Shadow Brokers are wrong and might have misidentified him. “I believe it is a case of mistaken identity and innocent people could be in danger,” he says.
Jake Williams, founder of US cyber security firm RenditionSec, believes the same. “Several people have told me that [The Shadow Brokers] misidentified the owner of the @drwolfff account and will dox an innocent person,” Williams wrote on Twitter.
People in the infosec community seem to know who Drwolfff is in real life, and all are surprised about The Shadow Brokers’ claims.
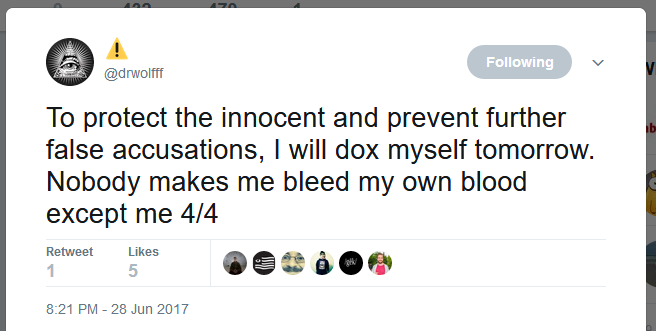
Because of this identity mix-up, Drwolfff has decided to that tomorrow, June 29, he’ll be doxing himself “to protect the innocent and prevent further false accusations.”
A dangerous game has started
Further, Williams doesn’t like the fact that the Shadow Brokers have resulted to threatening to expose NSA employees, even if they seem to be wrong.
“While ShadowBrokers has named TAO operators before, they’ve never threatened to tie specific operations to specific people,” Williams wrote on Twitter, referring to allegations of hacking Chinese targets. “Releasing that data will threaten the safety (and freedom) of former TAO operators traveling overseas.” The danger is clear and visible.
Williams sees this as a clear escalation in cyber-warfare, where individuals following orders as part of nation-state cyber operations can’t hide anymore behind generic codenames such as The Equation Group, Fancy Bear, Turla, or others.
But if we have to be fair, the Shadow Brokers aren’t the ones that started this cyber-ops doxing trend. Earlier in the year, the US DOJ named two Russian FSB officials in an indictment relating to the Yahoo 2014 data breach.
The US also went after Iranian hackers who have operated in revenge hacks after the US and Israel’s Stuxnet attacks, and also went after Chinese military members, who it branded as hackers.
Some would say NSA employees are about to reap the rewards planted by an aggressive US policy towards catching foreign nation-state hackers. Let’s hope the Shadow Brokers aren’t that incompetent to blame the wrong person.
Source:https://www.bleepingcomputer.com/news/security/shadow-brokers-threaten-to-expose-identity-of-former-nsa-hacker/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











