
A specialist recently published the findings of his research
According to experts in network security and ethical hacking from the International Institute of Cyber Security, the firmware of the WiFi chips used in various devices presents multiple security drawbacks. According to reports, some of these flaws could be exploited for remote execution of arbitrary code, all without the need for user’s interaction.
Security failures were discovered in ThreadX, a real-time operating system (RTOS); according to the website of the developers, ThreadX has more than 6 billion of implementations, being one of the most popular programs running with WiFi chips.
The firmware also operates on Marvell’s SoC Avastar 88W8897 (Wi-Fi + Bluetooth + NFC), present on Sony PlayStation 4, on the Microsoft Surface tablet, Xbox One, Samsung Chromebook and some smartphones, report network security experts.
Process initialization of WiFi chips
Regularly, a WiFi chip is initialized by a manufacturer’s controller charged with loading the firmware image during the startup process. With Marvell’s wireless chip system (SoC), there are certain drivers that work with the Linux kernel you use: ‘mwifiex’, ‘mLAN’, and ‘mlinux’.
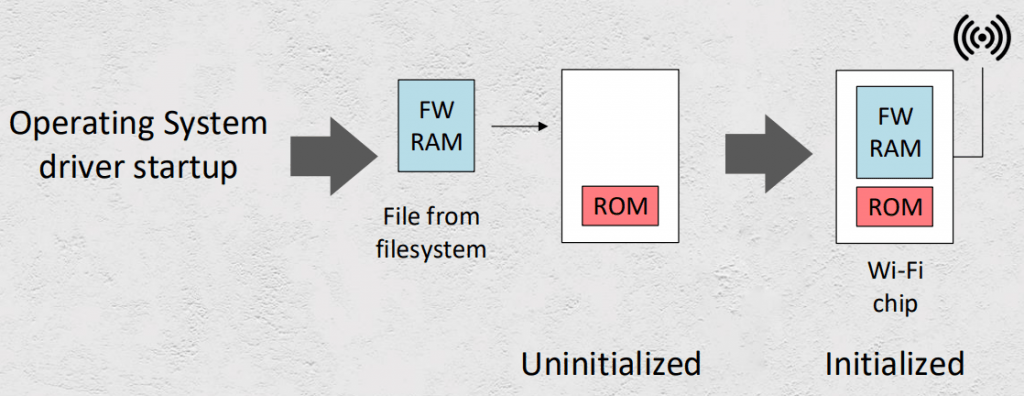
Both functions have debugging capabilities, allowing you to read and write to and from the WiFi module memory.
Controlling memory block allocation
One of the vulnerabilities discovered in the firmware is a block overflow that could be activated when the chip is looking for available networks, a process that starts every five minutes, even if the device is already connected to a WiFi network.
“An attacker could perform a remote code execution on a Samsung Chromebook, for example, even without the user having any interaction,” says Denis Selianin, a network security and WiFi device specialist.
In a report, Selianin describes two methods of exploitation, one that works with any ThreadX-based firmware if certain conditions are met, and another for the implementation of Marvell’s firmware in its modules; “The combination of these two methods leads to a successful exploitation of vulnerabilities,” says the expert.
In the generic case, an attacker can overwrite the pointer to the next free memory block and control the location to assign the following block: “When you control the location of the next block assignment, an attacker can place this block in place where some critical execution-time structures or pointers are found, thus achieving the execution of an attacker’s code”.
The exploitation of Marvell’s Avastar SoC vulnerability requires reverse-engineering activities for memory management routines. This works if the next block is busy.
The functions use a metadata header with special pointers that are called before releasing a block at the beginning of each ThreadX block. This information is enough to allow code execution in a wireless SoC.
Selianin said in his presentation that as soon as a solution is available, he will publish a review with the exploit and the tools used in the process.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











