Cyber crime is taking next level of steps for taking control on digital world. Research done by ethical hacking researcher of International Institute of Cyber Security (IICS) shows increase in cyber criminal activities. Different cyber criminals have different purpose to exploit any one privacy. There is no doubt that we can say that cyber security hasn’t increased. But there is always an way to create an backdoor for exploiting on any applications that are running on the servers. Developed nations Australia, Canada, New Zealand, United kingdom, United States has also been affected by these tools in recent cyber incidents.
There are many tools that are easily available. These tools can be used to exploit any user over the internet. Today we will talk about the 5 most widely tools that are used in cyber incidents recently. These tools are part of ethical hacking course offered by International Institute of Cyber Security (IICS), and these are capable of hijacking the different platforms like Windows, Mac, Linux.
Ethical hacking researcher of international institute of cyber security says, that these are commonly used by cyber criminals to steal private information of the users.
Whatever cyber criminal thinks, there initial targets is to find the common security weakness, unpatched softwares or the poorly configured systems. Most of the tools are spread by spam emails. The below tools are for educational purpose only using these tools without mutual consent can land you in legal trouble. The below tools comes in five categories :-
- Remote Access Trojans (RATs)
- Webshells
- Credential Stealers
- Lateral movement frameworks
- Command and control (C2C) obfuscators
Remote Access Trojans (RAT) – JBi Frost :-

Remote access trojans is a malware program used by cyber criminals to take full control of the computer for performing malicious activities. RATs are attached with commonly used programs and as well as in games. There are many RAT’s which are available but JBi Frost has been in the digital world because of its high demand by cyber criminals as said by cyber forensics experts of International Institute of Cyber Security (IICS). This tool is developed in 2015
Jbi Frost has been used continuously used from past 4-5 years by the cyber criminals. Jbi frost is a java based cross platform tool. This tool can be used to threat different operating systems windows, mac, linux. Jbi frost infection causes :-
- Block computer from restarting.
- Block Windows registry or Task manager
- Create files and directories with random names to inject the target.
- Record the keystrokes of the target.
- High CPU usage.
If your machine is injected using jbifrost. You can also use the decryptor to open the encrypted files in the jbifrost. For opening the files,you can use the decryptor available on github.
Webshell : The China Chopper
China chopper is publicly available tool. This well written tool can be used to target web server. In china chopper, webshells are uploaded after compromising the target and gains remote administrative capability. China chopper creates an virtual terminal on compromised devices. This tool has very small in size so it become easy for attacker to upload and exploit the target. China chopper was created in 2012
- The code is available on the github which can be modify according to the requirement.
- Caidoa.exe is only of 4 KB of size. For some network defenders it is difficult to find this payload.
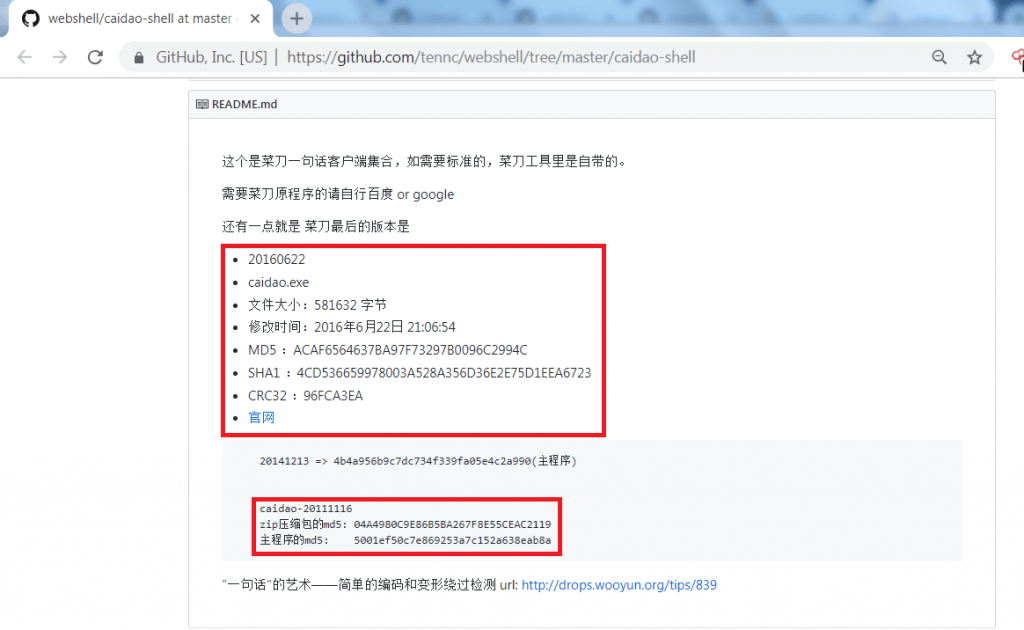
- The above screen shot shows the whole code of china chopper and the program is caidao.exe which shows their MD5 and SHA1 values.
- The china chopper code is written in php and .net and some of the files are in jsp. These files and codes can be used in other hacking activities.
- China chopper consists of two main components, the china chopper client side and the server side. Both of the components are in control of attacker. After installing the webshell of china chopper can issue terminal commands. Its MD5 hash value is on github as shown below.
- The webshell server is uploaded in plain text and can be changed by attacker. The webshell server was also listed in CVE 2017-3066. As most of public web server were affected by the webshell china chopper.
- Ethical hacking researcher shows that Webshell connects over TCP using HTTP POST request. Network traffic is analysis chopper packets. Those chopper packets can reveal the files and the commands after creating a session. As chopper generates post request from each command. Manual analysis becomes very long and slow for the attacker. So attacker deploy the chopper on a web server behind SSL which makes all traffic encrypted.
- China chopper gives attacker an authorization of downloading and uploading the files.
- You can also decode webshell china chopper by using python scripts listed on github as shown below.
Credenials Stealer : Mimikatz
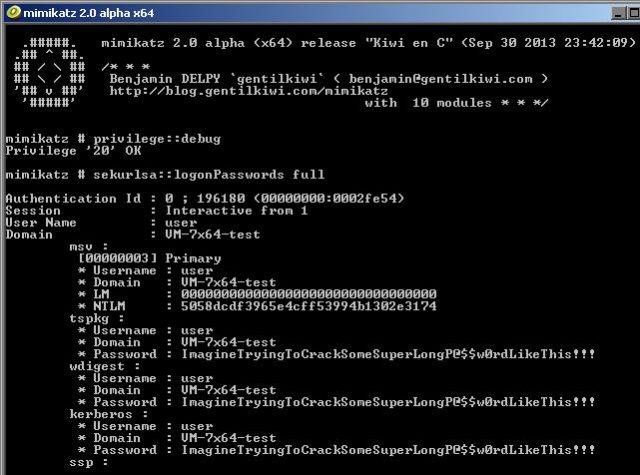
- The tool was develop to target the Windows users. Developed in 2007, an old but still shows an effective result for attacker. This tool was developed to steal credentials of other users. Mimikatz access in windows local security authority subsystem service (LSASS). This tool is also deployed in metasploit. Mimikatz has been used recently by cyber criminals to attack on the windows users and active directory networks.
- The authors Benjamin Delpy and Vincent LE TOUX has put all the code on github. But there they have listed Mimikatz as to play with windows security.
- The code is easily available can be accessed by any user.
- Mimikatz is capable of stealing the windows credentials in clear text form and even steals the hashes from the memory.
- Those hashes can be used to bypass the windows security of the other users if they are on the same network. These hashes can be used in other hacking activities.
- Mimikatz becomes automated with windows powershell scripts. This tool is vulnerable for Windows XP 2003, Windows 8.1, Windows SQL Server 2012 R2 and others.
Lateral Movement Framework : PowerShell Empire
- In recent years, this tool powershell empire has been used to exploit windows users. This tools is designed to allow an attacker to gain access to the network. This tools can also be used to make executables for accessing the social engineering networks.
- This tool is widely used by pentester to check the security of the windows machines in a network. Powershell empire is designed in 2015 for testing purposes.
- Powershell empire is difficult to detect on a network using traditional antivirus tools. Powershell empire used modules like credential harvesting, host enumeration, key logging.
- If target is on the attacker’s network, attacker can enters into target machine using listeners which scans the target Ip address on windows machine. Now attacker uses options which are provided by powershell empire to get the value of the target machine.
- You can check the code of powershell empire on githubas shown below.
C2 Obfuscation And Exfiltration : HUC Packet Transmitter

Most of the time when attacker don’t want to disguise their location so they use proxy server or any other tools to hide their location.
- HUC Packet Transmitter (Htran) is a proxy tool to intercept the TCP packets from a attacker to the target IP address. This tool was developed in 2009 and being used in recent attacks. Recent investigations has found that htran has been used to spread the malicious files over the internet, according to cyber forensics expert of International Institute of Cyber Security (IICS).
- Htran mostly target the vulnerable and outdated web applications. The use of Htran has been constantly seen in government and private industries.
- The code of this tool is easily available on github and can be used in other hacking activities.
- This proxy tool is used to evade detection and intrusion on a network.
- This tool is blend with common traffic to bypass security control systems.
- Htran creates an peer to peer network to transfer the files over the network.
- HTran runs in three modes in which each of the traffic forward across the network by creating bridge of two TCP sockets:
- Server which listens both TCP packets remotely.
- Client which listens both TCP packets locally
- Proxy which listens one TCP packet remotely. the other packet is initiated from locally after receiving the traffic from the first connection.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











