Earlier we have shown many scanning tools where you can gather lot of information about your target, in internal network or few external network. There are many individual ethical hacking security researchers in International Institute of Cyber Security uses such tools or use manual analyze method to collect information of victim in iicybersecurity labs. There are many recent attacks which shows how these open source tools are used in gathering information.
Different scenario needs different tools. Most of scanning is done on ports like – Port 80, 443 or other common network services. Such attacks are done with using public resources. These attacks are most common now days. Large Tech companies who uses IDS/ IPS or strong firewall to secure their networks are often compromised using customized open source methods/ tools. We scanned our local network for gathering information of the hosts. Today we will show you Kali Inbuilt tools.
Arping is designed to send ARP or ICMP requests to specified host & displays replies. The host may determine by its hostname or its IP address. Each request is send per second. ARP & ICMP are part of internet protocol. According to ethical hacking researcher of international institute of cyber security ARP is used to map IPv4 address with MAC address & ICMP is used to send error info to connected IP addresses when packets are not delivered and other purposes. Now we will gather information with arping.
- For testing we are using Kali Linux 2019.1 amd64. Hence, arping comes pre-installed, open terminal type arping –help
root@kali:~/Downloads# arping --help
ARPing 2.19, by Thomas Habets thomas@habets.se
usage: arping [ -0aAbdDeFpPqrRuUv ] [ -w ] [ -W ] [ -S ]
[ -T ] [ -t ] [ -c ]
[ -C ] [ -i ] [ -m ] [ -g ]
[ -V ] [ -Q ]
- Above help menu used in arping.
Note : For security we have masked the gathered MAC addresses.
Ping Host Using ARP Packets :-
- Type arping 192.168.1.3
- 192.168.1.3 is the target IPv4.
root@kali:~/Downloads# arping 192.168.1.3
ARPING 192.168.1.3
42 bytes from 0#:##:17:##:##:#0 (192.168.1.3): index=0 time=118.068 msec
42 bytes from 0#:##:17:##:##:#0 (192.168.1.3): index=1 time=40.460 msec
42 bytes from 0#:##:17:##:##:#0 (192.168.1.3): index=2 time=61.031 msec
42 bytes from 0#:##:17:##:##:#0 (192.168.1.3): index=3 time=83.548 msec
- Above query has gathered around 42 bytes of data reply from 192.168.1.3 of around 40-120 msec.
- Above output shows MAC address of the target. Results shows that targets is vulnerable to arping which can be used other attacking methods.
Ping Host Using Specific Interface With Certain Request :-
- Type arping -i wlan0 -c8 192.168.1.3 -vv
- -i is used to enter network interface.
- -c is used to count send requests. Here 8 requests will be send.
- 192.168.1.3 is the target IP address.
- -vv is used for verbose mode.
root@kali:~/Downloads# arping -i wlan0 -c8 192.168.1.3 -vv
arping: clock_getres() = 0s 1ns
arping: libnet_init(wlan0)
arping: libnet_init(wlan0)
Timestamp types:
Name Description
arping: Successfully chrooted to /run/sshd
arping: Successfully dropped uid/gid to 65534/65534.
arping: pcap_get_selectable_fd(): 4
This box: Interface: wlan0 IP: 192.168.1.4 MAC address: b#:##:##:3#:##:##
ARPING 192.168.1.3
arping: sending packet at time 3003.792576155
42 bytes from 0#:##:##:00:##:b# (192.168.1.3): index=0 time=50.523 msec
arping: sending packet at time 3004.793923502
42 bytes from 0#:##:##:00:##:b# (192.168.1.3): index=1 time=73.002 msec
arping: sending packet at time 3007.797879408
42 bytes from 0#:##:##:00:##:b# (192.168.1.3): index=4 time=38.618 msec
arping: sending packet at time 3008.799252107
42 bytes from 0#:##:##:00:##:b# (192.168.1.3): index=5 time=61.192 msec
--- 192.168.1.3 statistics ---
8 packets transmitted, 8 packets received, 0% unanswered (0 extra)
rtt min/avg/max/std-dev = 38.618/78.477/118.228/25.969 ms
- In the above output, arping has send packets in milli seconds of 42 bytes to the target. The above request has gathered MAC addresses of the target with certain no. of requests.
Broadcast Target IP address ARP Cache :-
- Type arping -U 192.168.1.3
- -U is used to send unsolicited ARP.
- 192.168.1.3 is target IPv4.
root@kali:~/Downloads# arping -U 192.168.1.3
ARPING 192.168.1.3
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=0 time=80.594 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=1 time=103.256 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=2 time=25.452 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=3 time=46.234 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=4 time=3.548 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=5 time=91.538 msec
42 bytes from 0#:e#:##:00:##:#0 (192.168.1.3): index=6 time=115.317 msec
^C
--- 192.168.1.3 statistics ---
7 packets transmitted, 7 packets received, 0% unanswered (0 extra)
rtt min/avg/max/std-dev = 3.548/66.563/115.317/38.947 ms
- Above query has send the arp update neighbour ARP caches. With the response of 42 bytes. The above query shows that cache has been updated.
- For checking if cache has updated, you can do arp -a in command prompt. As we have found using IP address that on which OS target machine is running.
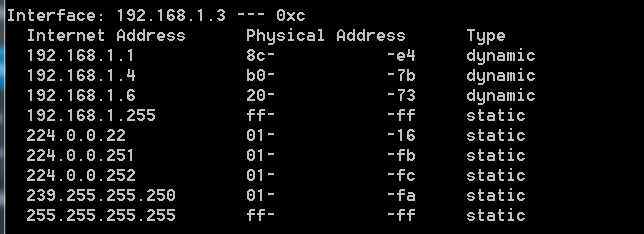
- In the above screen shot, Target (192.168.1.3) ARP cache has been updated. As attacker’s IP address was (192.168.1.4) which is found in the list of arp cache of target machine.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











