LibreOffice is a free use and open source office software package that has a relatively large number of users. Recently, web application security specialists reported a flaw that could compromise the integrity of a system by simply opening a malicious file.
According to reports, this condition exists due to a code execution vulnerability that, if exploited, could allow a hacker to inject malware into the compromised system after the user interacts with the specially crafted file. This software package is one of the most popular alternatives to the use of Microsoft Office suite and is suitable with Windows, Linux and macOS systems.
Just a few weeks ago, LibreOffice developers released the latest version of their software, adding fixes for two severe vulnerabilities (tracked as CVE-2019-9848 and CVE-2019-9849). However, hackers managed to develop a method to bypass newly implemented fixes, mentioned web application security specialists. Although the details of this “counter-attack” are still unknown, the impact of the vulnerabilities is known to remain highly considerable.
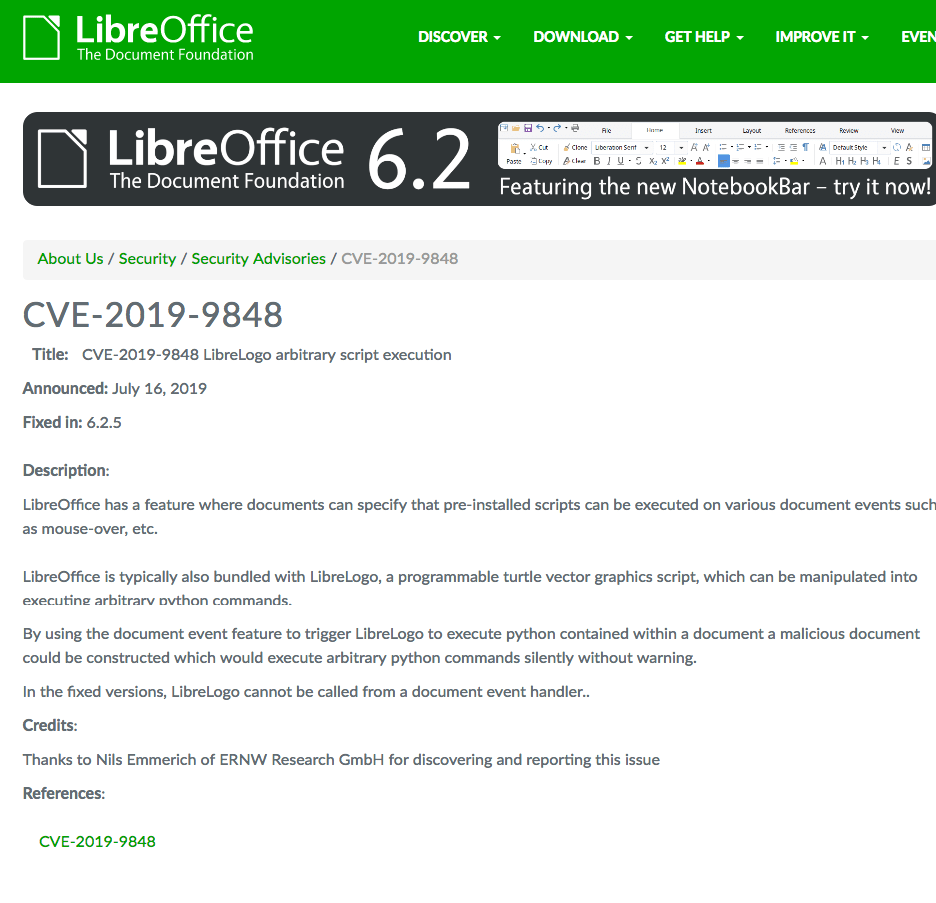
The first vulnerability (CVE-2019-9848), still existing in the latest version, resides in LibreLogo, a vector graphics script that is delivered by default with the LibreOffice package. This feature allows users to specify pre-installed scripts in a document that will run under certain circumstances, such as mouse interactions.
As for the vulnerability, it could allow a hacker to create a malicious document to execute arbitrary python commands without the victim being able to detect this unauthorized activity. Nils Emmerich, the researcher who discovered the vulnerability, even released a proof-of-concept for exploiting this particular flaw.
Exploitation of the second vulnerability (CVE-2019-9849) would allow the injection of remote arbitrary code into a document; the flaw persists even if LibreOffice’s “Stealth Mode” is enabled. This feature is not enabled by default, but users can turn it on to tell a LibreOffice document to retrieve remote resources only from trusted locations.
International Institute of Cyber Security (IICS) web application security specialists recommend potentially affected users update or reinstall their LibreOffice versions to remove the LibreLogo component at least until the company releases the full update patches.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











