A few months ago a cybersecurity report revealed that at least 33 Canon cameras were exposed to the exploitation of some critical security vulnerabilities via WiFi or USB, which could lead to ransomware infections, compromising the files stored in the device’s memory.
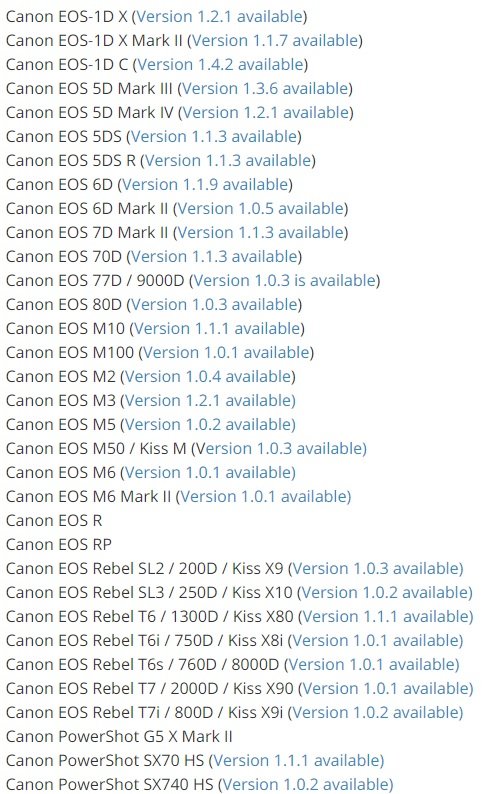
Shortly after the release of the report it was confirmed that the issue (a vulnerability in a standard communication protocol) could also affect other companies’ products. Nearly half a year later, Canon mentions that 30 of its vulnerable cameras have already been completely corrected, although the flaw still persists on three popular models: Canon EOS R, Canon EOS RP and Canon PowerShot G5 X Mark II.
SOURCE: Check Point
The report was presented by cybersecurity firm Check Point, including a proof-of-concept showing how to infect a camera (Canon EOS 80D) with encryption malware with relative ease by abusing some security holes in the Picture Transfer Protocol (PTP), a standard used in cameras and computers.
This is a standardized protocol and is present in the models of many other camera manufacturers, so the scope of the vulnerability has not yet been accurately determined. In the report, Eyal Itkin, Check Point’s cybersecurity researcher mentions: “We focus on Canon because of its predominant character in the market, however, it is necessary to mention that this protocol is present in virtually all cameras digital available.”
When the first report was published, Canon emphasized the fact that there were no known cases of exploitation of these failures in real-world scenarios. However, the International Institute of Cyber Security (IICS) points to the long time it took the company to release updates as a new risk factor for users. Firmware updates are now available (except for the three models mentioned above). Users should update as soon as possible to mitigate any risk. It should be remembered that this is a security issue inherent to most camera manufacturers, so users of other companies should consult with the manufacturer about safety risks and protective measures.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











