One of the most well-known security standards in telecommunications and mobile networks is mutual authentication, which allows a smartphone and mobile network to verify their identities. In the Long Term Evolution (LTE) standard, mutual authentication is set at the control plane, with secure authentication and a key agreement protocol. Recently, network security specialists at universities in Germany and the United Arab Emirates demonstrated that it is possible to abuse the lack of user-level integrity protection to deploy some attack variants.
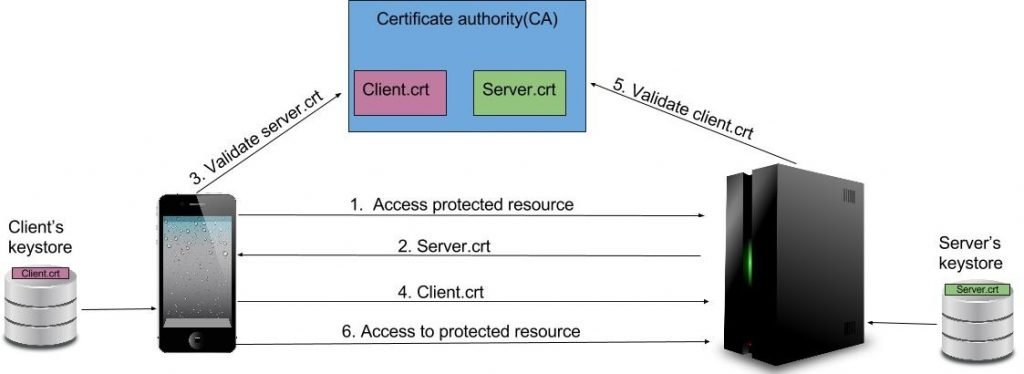
These attack variants known as IMPAGT, focus on exploiting an IP stack operating system reflection mechanism and the lack of user data integrity protection to subsequently complete the attack against third layer, allowing threat actors to impersonate a legitimate user on a network by injecting arbitrary packets.
Impersonation can be done on the uplink or in the downlink direction:
- In the uplink attack, a hacker can impersonate a victim to the network and can use arbitrary IP services (websites) with the identity of the victim. All traffic generated by the attacker is associated with the victim’s IP address
- Downlink spoofing allows hackers to establish a TCP/IP connection to the phone that bypasses any firewall mechanism on the LTE network. Attacker cannot break any security mechanism above IP layer
Network security specialists deployed multiple scenarios to verify the behavior of devices with iOS or Android operating systems in the event of such an attack.
Successful exploitation of this attack would allow threat actors to impersonate the victim or network at the IP layer, so they could send and receive IP packets with the impersonated identity. It is important to note that attackers would not be able to access the victim’s email accounts or messaging services, make phone calls, or break a website’s TLS encryption.
For mobile operators, they rely on mutual authentication to bill or provide access to some service websites that can only be accessed with a network layer identifier. According to network security specialists, IMP4GT attacks allow threat actors to use the identity of victims to access those services when they do not request additional authorization.
While the potential consequences of an attack are disastrous, users are at risk of mild to moderate, as exploiting an IMP4GT attack requires a threat actor with advanced skills, and needs to be in a location close to potential victims. As if that weren’t enough, some highly specialized hardware tools and a custom implementation of the LTE protocol stack are required, not to mention that this analysis was performed in a controlled test environment.
As already mentioned, the attack exploits the absence of missing integrity protection and the operating system’s reflection mechanism. Because only the first attack vector is inherent in mobile networks, this variable is defined by the operating system of the affected device. Considering the above, and because user data integrity protection is compatible with 5G networks, although not used in cases of dual connectivity, early 5G implementations are vulnerable to these attacks.
To conclude their report (available here) network security researchers highlighted the fact that these attacks are based on a specification failure, so all network providers are vulnerable.
The International Institute of Cyber Security (IICS) has broadly monitored reports of network attacks exploiting 4G technology; while it is considered that the transition to the use of 5G networks would obstruct the deployment of a wide variety of attacks, completing this process is truly complex, as even in the more developed countries the transition has been carried out in a leisurely manner and only in regions determined, so it could take years to achieve the widespread use of 5G technology.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











