The vulnerability testing team from security firm Eclypsium recently released a document detailing the finding of unsigned firmware in multiple drivers (WiFi adapters, USB ports, and cameras, among others) installed on the computers of manufacturers such as Lenovo, Dell and HP. In this report, researchers demonstrated that it is possible to abuse the absence of signatures to infect the target system with malware, putting millions of users of Windows and Linux systems at risk.
While the dangers of firmware hacking have been known for at least five years, manufacturers have shown little interest in addressing this attack vector, so it is now still common to find unsigned firmware in aforementioned components. To make matters worse, it is fully demonstrated that these firmware vulnerabilities are, in most cases, virtually impossible to fix by software updates, so affected devices will remain exposed to ransomware infections, extraction of sensitive data, among other malicious activities.
The lack of adequate protections and safety practices in peripheral devices is an industry problem; in this specific report, the researchers refer to the lack of firmware verification before these devices run the code. In other words, peripherals don’t have a way of knowing if the loaded firmware is legitimate, so an attacker might insert a malicious or vulnerable firmware image and the components wouldn’t notice anomalous behavior. Vulnerability testing specialists identified three stages of the main risk scenario:
- A threat actor gains access to a device, either by delivering malware via email, redirecting the victim to a malicious website or any other known method. Once inside the target system, the malware may write malicious firmware to the vulnerable component
- If this attacked component does not require strict firmware verification, the attacker’s code is loaded and executed
- The threat actor uses the capabilities and privileges of the attacked component to deploy additional attacks
Malicious tasks performed by threat actors vary depending on the compromised component.
Vulnerable Components
Touchpad and trackpoint firmware on Lenovo laptops
For this test, the researchers analyzed a Lenovo ThinkPad X1 Carbon 6th Gen laptop, although it should be noted that these kinds of drawbacks are not limited to some computer models, but affect the industry in general.
During the investigation, vulnerability testing specialists discovered that these components employ an unsecure firmware update mechanism, identifying that device-level cryptographic verification was not necessary for implement updates, allowing firmware image modifications for the execution of malicious code on these touchpads and trackpoints. Through a statement, Lenovo acknowledged that this generation of laptops does not have a way to correct these flaws.

Wide Vision FHD Camera firmware on HP Laptops
Researchers tested on an HP Spectre x360 Convertible 13-ap0xxx laptop. Like the previous case, updating the firmware of Wide Vision FHD cameras on HP laptops is not an encrypted process, so it is possible to make firmware modifications to alter USB descriptors using the update tool delivered by HP.
These computers use a Windows-based firmware update tool, which accepts modified files to adjust the contents of the USB descriptor; this feature can be abused by threat actors to disable the device or have it identified as a different type of USB to analyze additional details of the compromised system processor architecture.

WiFi adapter on Dell XPS 15 9560 laptops
By analyzing Dell devices, specifically the WiFi adapter on the Dell XPS 15 9560 laptop, vulnerability testing experts demonstrated that they were able to modify the firmware of the affected component. The Windows 10 system will check to confirm that the drivers are properly signed, and a small certificate icon is displayed next to the driver when viewed in Device Manager, as shown below:
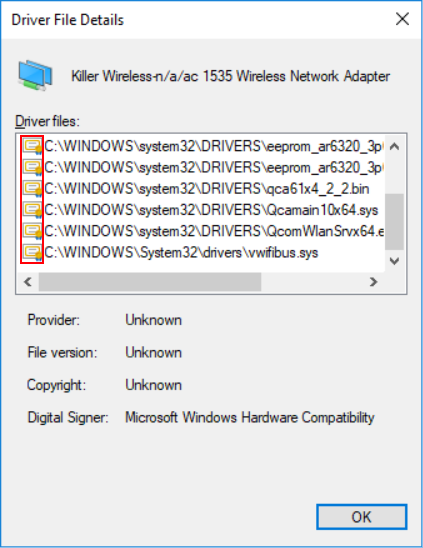
When we modify the firmware image for the WiFi adapter, we can see that the icon disappears:
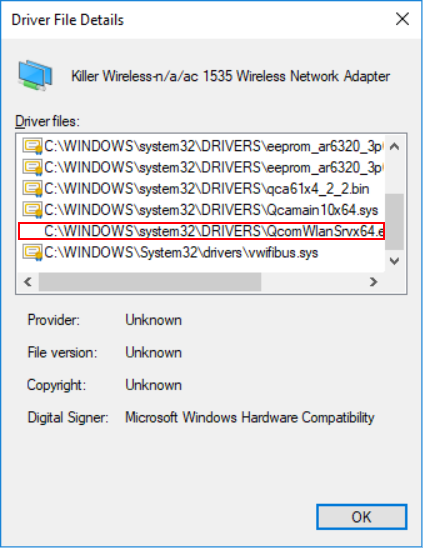
As shown in the screenshot above, the certificate icon is no longer displayed. Although the icon is missing, it is possible to modify the firmware in a malicious way, yet the driver loads it successfully on the device.
As mentioned throughout this research, the unsigned firmware issue affects the entire industry and its respective vendors. Although a few years ago manufacturers began to implement some changes so that their components only accept valid firmware, the International Institute of Cyber Security (IICS) believes that the adoption of best practices has lagged behind due to ignorance of attacks in the wild, a situation that has changed recently, so companies must work at forced marches to create a fully protected environment.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











