Months ago, Zimperium hacking course experts reported two kernel vulnerabilities present on all Android devices with Qualcomm chipsets. Exploiting these flaws, in conjunction with other previously discovered security issues, allowed hackers to use malicious apps to access root user permissions on the affected device.
Through this attack the threat actors were able to deploy various malicious activities such as:
- Read sensitive data stored on your device, including photos, videos, text messages (even in apps like WhatsApp and Telegram), emails, and almost any other resource stored on your device
- Access to all login credentials for any installed application
- Recording audio and video, activating the user’s camera and microphone without their consent
The vulnerabilities were identified as CVE-2019-14040 and CVE-2019-14041. Below are some technical details about these flaws and their potential consequences. To get started, the hacking course specialists specify what each flaw consists of:
- CVE-2019-14041: a race condition that can cause all kinds of memory damage
- CVE-2019-14040: A use-after-free kernel memory allocation flaw
The first of these flaws is derived from a function: __qseecom_update_cmd_buf (and also its 64-bit equivalent __qseecom_update_cmd_buf_64), whose function is to update the buffer to be sent to TrustZone.
To avoid code duplication, the function is designed to handle two different cases in which it is necessary to modify those buffers, so this function can be reached from two completely different ioctls. According to the hacking course specialists, in some parts, the feature has yet to behave differently depending on which ioctl was originally called. To do this, the function verifies data-> type:
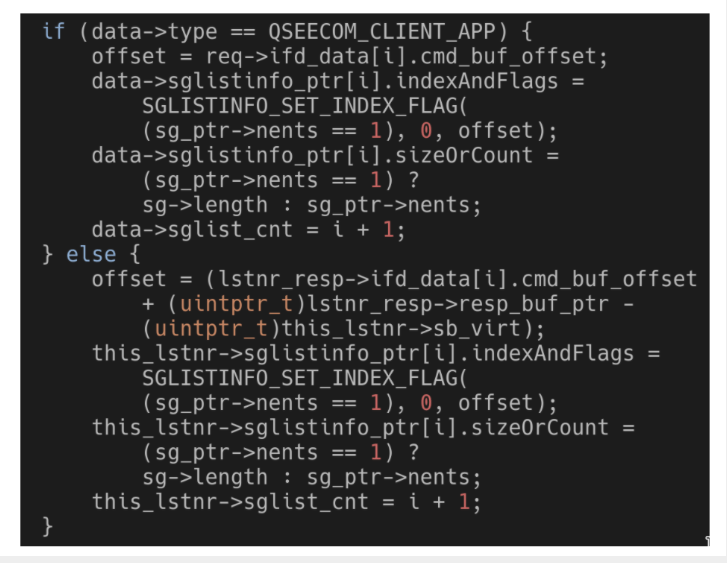
In a data->type case it would be QSEECOM_CLIENT_APP. In the other case, it would be QSEECOM_LISTENER_SERVICE. Verifications like this exist throughout the function.
The drawback is that the data is actually a pointer to a qseecom_dev_handle structure, which is attached to the open /dev/qseecom file in which the ioctl is performed. What if it is possible to modify data->type while __qseecom_update_cmd_buf is running?
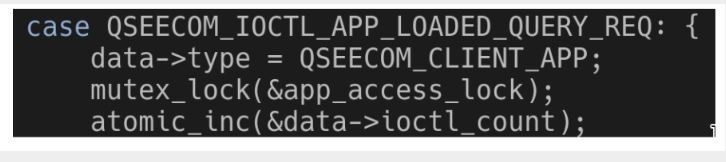
It turns out that running the ioctl QSEECOM_IOCTL_APP_LOADED_QUERY_REQ instantly modifies data-> type. Although there are some mechanisms to limit the simultaneous execution of ioctls, they only work after changing data->type.
Regarding the second vulnerability, this could allow an attacker to reach full privileges on the target kernel stealthily, as the victim could hardly notice malicious activity. Theoretically, an uneleged threat actor could complete a successful operating chain in a relatively simple way, so it’s worth staying on top of updates Qualcomm might release.
For further reports on vulnerabilities, exploits, malware variants and information security risks you can access the Website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











