Like virtually every week, Cisco announced the release of a new set of security updates to address vulnerabilities in various products. Cloud security course experts ensure that most of the flaws corrected in this update are found in Cisco IP phones and Cisco UCS Director, as well as Cisco UCS Director Express for Big Data, unified solutions for data center operations.
Cybersecurity specialist Jacob Baines mentions that he reported two critical flaws present in the Cisco 8821 wireless IP phone. Subsequently, Cisco analyzed security on other IP phone models, discovering that they were also affected by the flaw.
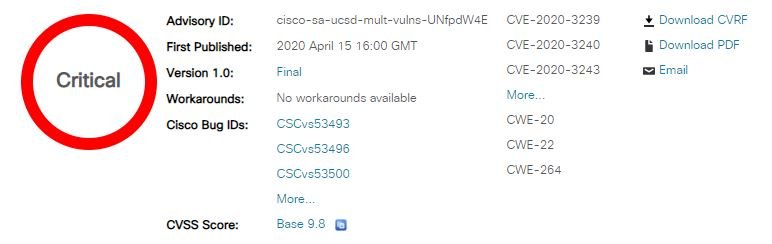
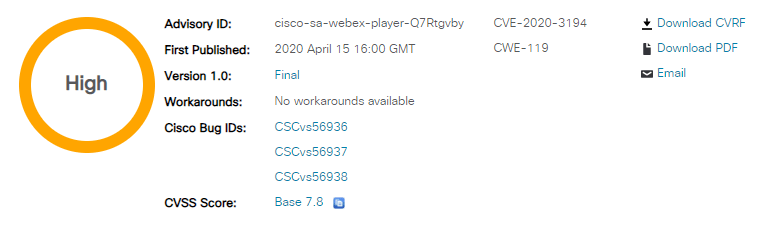
The two vulnerabilities discovered by the cloud security course expert, tracked as CVE-2020-3161 and CVE-2016-1421, affect the web server and web application of Cisco IP phones respectively. According to the report, both flaws allow unauthenticated remote threat actors to trigger a stack-based buffer overflow by sending a specially crafted HTTP request, which could lead to a denial of service (DDoS) attack, in addition to allowing the hacker to execute high-privileged code. The expert released a proof-of-concept of the DDoS attack for both flaws on the GitHub platform.
It was about four years ago that these vulnerabilities were detected. However, because an attack required authentication on the system, Cisco was not on the list of affected companies. When this new condition was detected, the list was updated and Cisco was notified about the security status of its IP phones.
Cloud security course specialists advise administrators to check if their IP phones have already received the corresponding firmware update. For now, the existence of workarounds is unknown, so it is necessary to install the Cisco update.
However, the International Institute of Cyber Security (IICS) recommends disabling web access to these devices; this feature is disabled by default, although many system administrators enable it manually.
In addition to these flaws, Cisco issued security patches to fix nine other authentication bypass vulnerabilities in the Cisco UCS Director REST API and Cisco UCS Director Express for technology companies. Of these flaws, only one is considered of severe gravity; its exploitation would allow a remote threat actor to bypass the authentication process or perform multiple attack variants against the affected system.
Administrators are encouraged to upgrade to UCS Director Release 6.7.4.0 and UCS Director Express Release 3.7.4.0 to address these issues.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











