Introduction
Pwndrop is self-deploying file hosting services. We use this tool for transferring file to other person very securely and be cautious of the fact that using same way any malicious file can send to the victims. This tool HTTP (Hyper Text Transport Protocol) and WebDAV (Web Distributed Authoring and Versioning) for transferring files. Ethical hackers can use this to deploy their files from remote locations using cloud services. This tool is easy to install and use.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel-Version: 5.2.3
Go Installation Steps
- We have to log-in to non-root and execute the below command
- Use this command to download the go file
- curl -O https://dl.google.com/go/go1.10.3.linux-amd64.tar.gz
- After verifying use this command to extract the downloaded go file.
- tar -xvzf go1.10.3.linux-amd64.tar.gz
- x = extract
- v= verbose
- F =file
- Now we just have to go to our home directory, change owner and group to root and move it to /usr/local
- sudo chown -R root:root go
- sudo mv go /usr/local
- Now, let’s check the file
iicybersecurity@kali:~$ cd /usr/local iicybersecurity@kali:~$ :/usr/local$ ls bin etc games go include lib man sbin share src work
Now Set the GO PATH
- Use this command to set Go’s root valve sudo nano ~/.profile
- At the end of the file, add this line
- export GOPATH=$HOME/work
- export PATH=$PATH:/usr/local/go/bin:$GOPATH/bin
- We can choose alternate Go’s installation location, add these lines at the end of the same file
$export GOROOT=$HOME/go- $export GOPATH=$HOME/work
- $export PATH=$PATH:$GOROOT/bin:$GOPATH/bin
iicybersecurity@kali:~$ export GOPATH=$HOME/work iicybersecurity@kali:~$exportPATH=$PATH:/usr/local/go/bin:$GOPATH/bin iicybersecurity@kali:~$ export GOROOT=$HOME/go iicybersecurity@kali:~$ export GOPATH=$HOME/work iicybersecurity@kali:~$ export PATH=$PATH:$GOROOT/bin:$GOPATH/bin iicybersecurity@kali:~$ mkdir $HOME/work iicybersecurity@kali:~$ ls examples.desktop go1.10.3.linux-amd64.tar.gz work
- After adding the above steps in the profile save and exit. Now run the source command.
- $source ~/.profile
Testing your Installation
- Now create a new directory for your Go to create files in it.
- $mkdir $HOME/work
- After creating the new directory, use this command to create your test file
- $mkdir -p work/src/github.com/user/hello
- Next, use this command to create a hello world file
- $nano ~/work/src/github.com/user/hello/hello.go
- After using the above command, past the below in your text editor code save and close the file.
package mainimport "fmt"func main() {fmt.Printf("hello, world\n")}
- Next use this command to compile it by invoking Go command
- $go install github.com/user/hello
- Next, simply type $hello it will execute the file
- iicybersecurity@kali:~$ hello
- Next use this command which hello it will show you the path
iicybersecurity@kali:~$ which hello /home/iicybersecurity/work/bin/hello
Now Pwndrop Installation
- Use this command to download the pwndrop zip file
- wget https://github.com/kgretzky/pwndrop/releases/download/1.0.0/pwndrop-linux-amd64.tar.gz
root@kali:/home/iicybersecurity# wget https://github.com/kgretzky/pwndrop/releases/download/1.0.0/pwndrop-linux-amd64.tar.gz --2020-04-18 17:42:54-- https://github.com/kgretzky/pwndrop/releases/download/1.0.0/pwndrop-linux-amd64.tar.gz Resolving github.com (github.com)... 13.234.176.102 Connecting to github.com (github.com)|13.234.176.102|:443... connected. HTTP request sent, awaiting response... 302 Found Location: https://github-production-release-asset-2e65be.s3.amazonaws.com/224714134/a53b1e80-7fd8-11ea-974b-7d1700d6fae5?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20200418%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20200418T121300Z&X-Amz-Expires=300&X-Amz-Signature=9e04282aba4cc7899b3fe4c00c6aa25bbf4a48b5681c8bb81d9015c0a76a918e&X-Amz-SignedHeaders=host&actor_id=0&repo_id=224714134&response-content-disposition=attachment%3B%20filename%3Dpwndrop-linux-amd64.tar.gz&response-content-type=application%2Foctet-stream [following] --2020-04-18 17:42:55-- https://github-production-release-asset-2e65be.s3.amazonaws.com/224714134/a53b1e80-7fd8-11ea-974b-7d1700d6fae5?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20200418%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20200418T121300Z&X-Amz-Expires=300&X-Amz-Signature=9e04282aba4cc7899b3fe4c00c6aa25bbf4a48b5681c8bb81d9015c0a76a918e&X-Amz-SignedHeaders=host&actor_id=0&repo_id=224714134&response-content-disposition=attachment%3B%20filename%3Dpwndrop-linux-amd64.tar.gz&response-content-type=application%2Foctet-stream Resolving github-production-release-asset-2e65be.s3.amazonaws.com (github-production-release-asset-2e65be.s3.amazonaws.com)... 52.216.18.176 Connecting to github-production-release-asset-2e65be.s3.amazonaws.com (github-production-release-asset-2e65be.s3.amazonaws.com)|52.216.18.176|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 6088834 (5.8M) [application/octet-stream] Saving to: ‘pwndrop-linux-amd64.tar.gz.2’ pwndrop-linux-amd64.tar.gz.2 100%[====================================================================================================>] 5.81M 512KB/s in 9.6s 2020-04-18 17:43:06 (618 KB/s) - ‘pwndrop-linux-amd64.tar.gz.2’ saved [6088834/6088834]
- Now, use this command to extract the file tar zxvf pwndrop-linux-amd64.tar.gz
root@kali:/home/iicybersecurity# tar zxvf pwndrop-linux-amd64.tar.gz pwndrop/ pwndrop/admin/ pwndrop/admin/deps/ pwndrop/admin/deps/animate.min.css ==============================================================================================SNIP================================================================================================= pwndrop/admin/pages/main.js pwndrop/admin/pages/style.css pwndrop/admin/pages/vars.js pwndrop/pwndrop
- use this cd command to enter into pwndrop directory.
- cd pwndrop/
root@kali:/home/iicybersecurity# cd pwndrop/ root@kali:/home/iicybersecurity/pwndrop#
- Use this command to install the pwndrop,
- ./pwndrop install
root@kali:/home/iicybersecurity/pwndrop# ./pwndrop install [2020-04-18 18:00:06] [+++] copied pwndrop executable to: /usr/local/pwndrop/pwndrop [2020-04-18 18:00:06] [+++] copied admin panel to: /usr/local/pwndrop/admin [2020-04-18 18:00:06] [inf] service already installed [2020-04-18 18:00:06] [+++] successfully installed daemon
- Use this command to start the pwndrop services
- ./pwndrop start
root@kali:/home/iicybersecurity/pwndrop# ./pwndrop start [2020-04-18 18:01:11] [inf] daemon already running [2020-04-18 18:01:11] [+++] pwndrop is running
- Now, open the browser and enter your IP
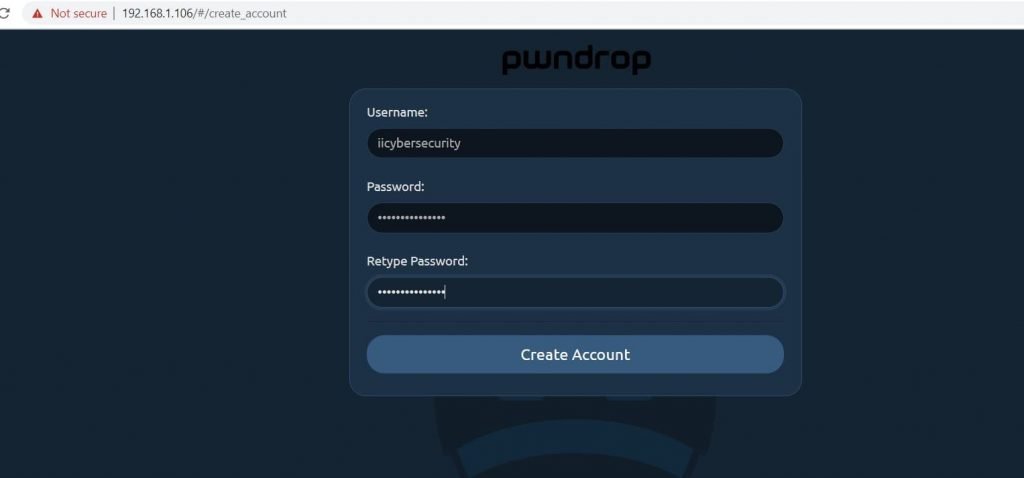
- Now, we have to create our account in the pwndrop
- Enter username & password and click on create an account.
- After creating the account, we see this page
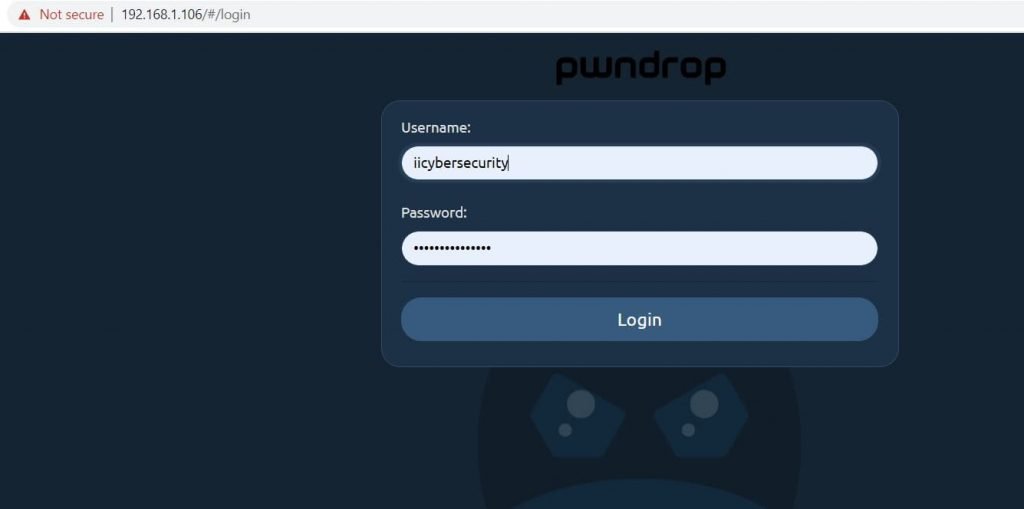
- Here, enter the username and password to login to pwndrop.
- Now, we are going to upload a file and to transfer to another person.
- Click on upload and select a file which you want to upload
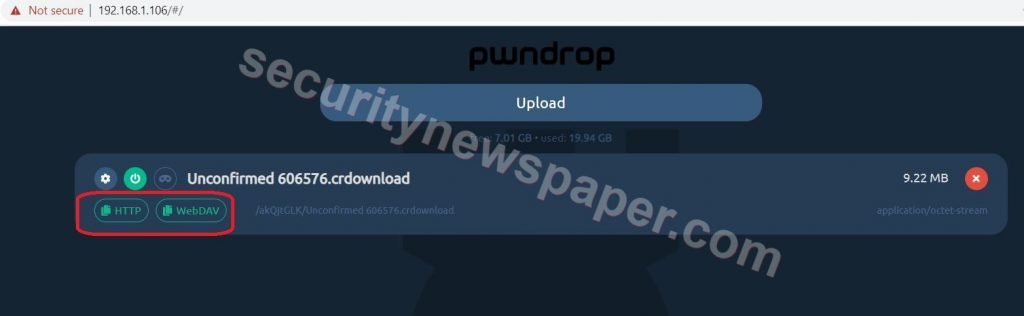
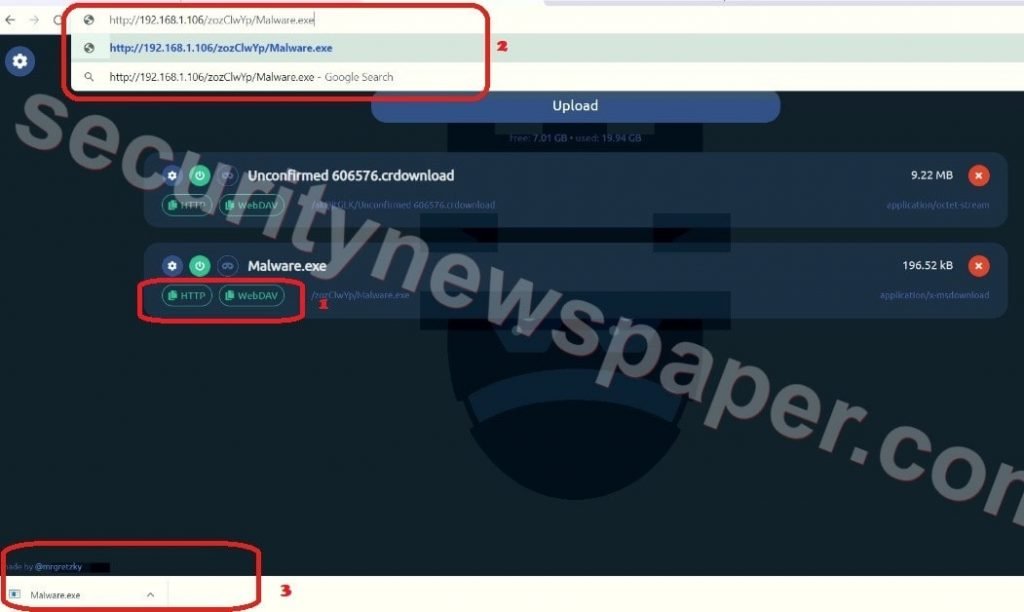
- In the above picture we see two options HTTP and WebDAV.
- Click on any option to copy the link and send this link to other people
- By this other person can download the file very easily
Testing Uploading Malware Sample
- Now, lets upload any Malware.exe application in pwndrop
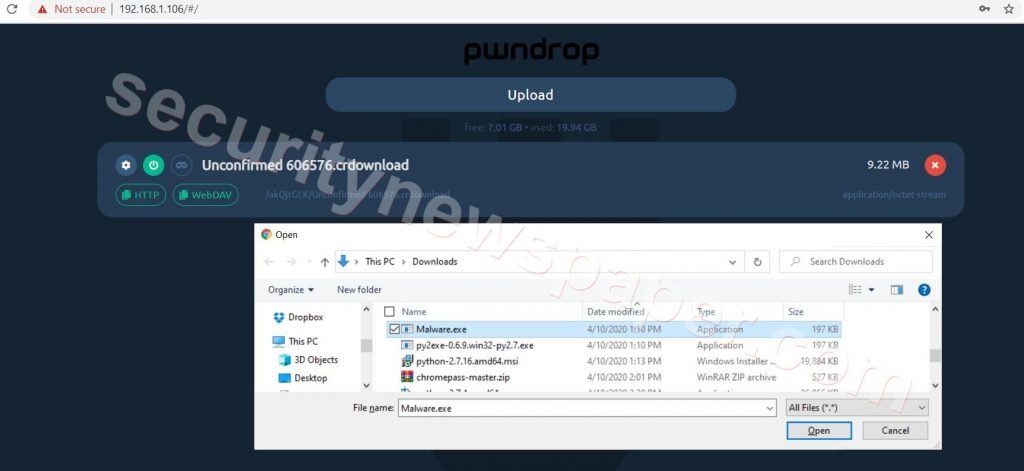
- Select any Malware application and click on open to upload the file.
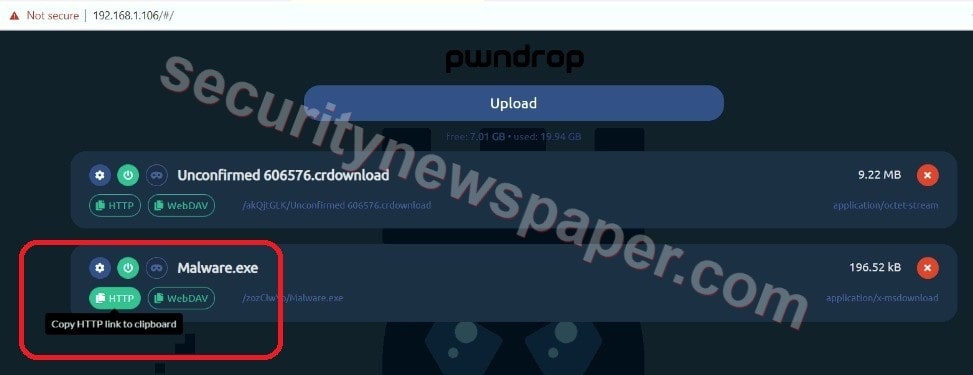
- Here we have successfully uploaded the malware application into pwndrop.
- Now, copy the URL and send this to the victim. If the victim opens the URL in the browser the malware.exe file will be download in the victim’s system.
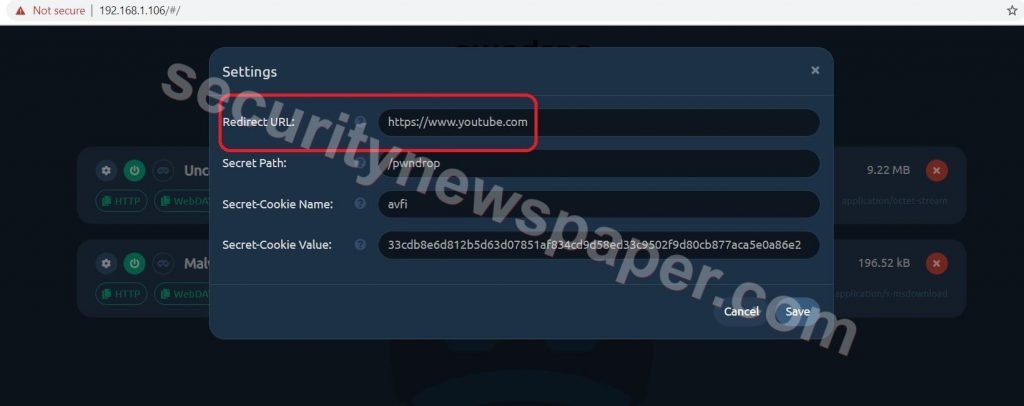
- In this tool, we have a settings option to Redirect URL.
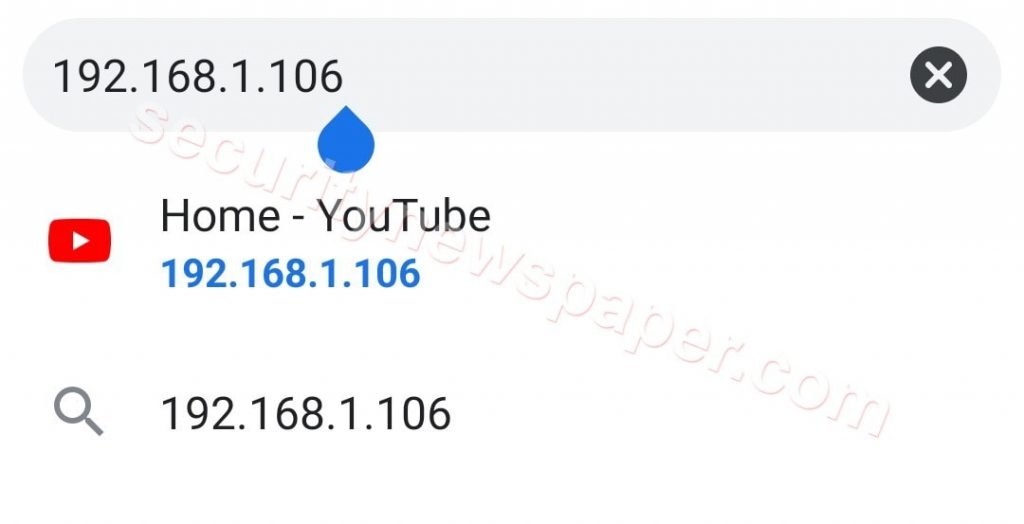
- If any person in our LAN tries to enter this IP in the browser, it will redirect to YouTube and we can also change the URL.
- When we tried to open the same IP from other device
- Previously we worked on a tool on HOW TO HACK VICTIM BY SENDING MALICIOUS EXCEL AND WORD DOCUMENTS
In this, we send the malicious file to the victim through Pendrive but now we can also use this tool to upload the malicious word file and send link to the victim. .
Conclusion
Pwndrop tool can be used in public cloud environment for easy file deployment across internet.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











