As the use of video conferencing platforms for home work increases, the battle between big tech companies continues to seek to seize a market that was badly exploited before the pandemic. This increase in the use of these resources has also revealed multiple security flaws, experts in a pentest training course.
One of the most recent security risks has to do with a malicious GIF that might have been stealing information from some Microsoft Teams accounts by exploiting a vulnerability to take full control of an organization’s networks. This problem was detected from the end of February, and is known to have remained active until a couple of weeks ago. The vulnerability was fixed on April 20, so no more similar attacks are expected.
According to the experts of the pentest training course, this vulnerability was present in all versions of Microsoft Teams for desktop and web browser. The problem lies in the way this software manages authentication tokens for image display.
Microsoft handles those tokens on its server located on teams.microsoft.com or any subdomain under that address. CyberArk researchers found that it was possible to hijack two of these subdomains (aadsync-test.teams.microsoft.com and data-dev.teams.microsoft.com) for malicious purposes.
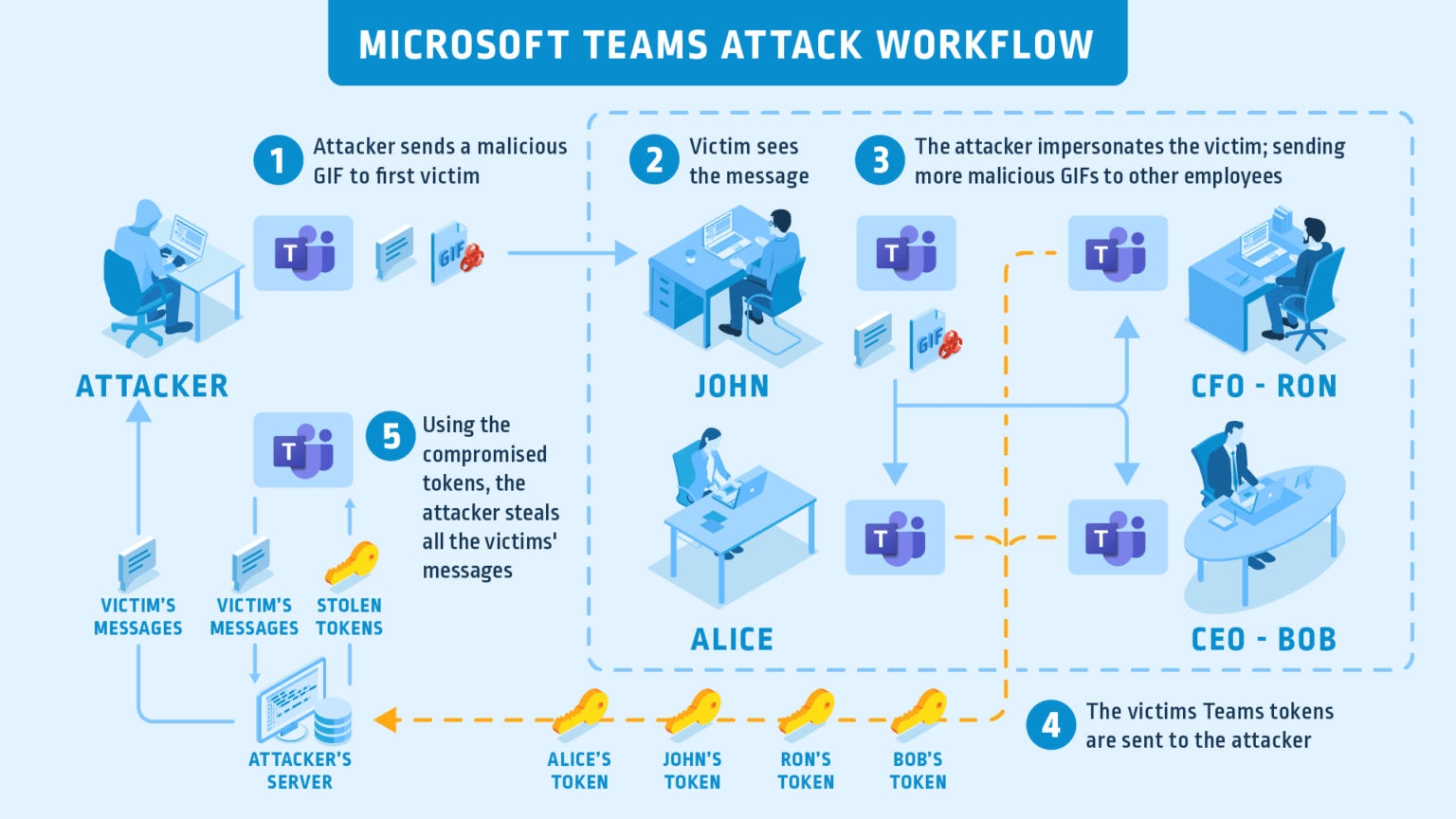
Apparently, if a threat actor managed to get a target user to visit one of the compromised subdomains, the authentication tokens could be moved to a hacker-controlled server. Subsequently, threat actors could create a “token skype” to access Microsoft Team deployments.
Up to this point, this looks like a conventional phishing campaign. However, experts identified the use of a malicious GIF (an image of Donald Duck); by viewing this file, the compromised computers would be forced to give up the authentication token, thus giving up their data. According to the experts of the pentest training course, this is because the source of the GIF was a compromised subdomain and the teams will automatically communicate with them to view the image.
This attack variant could have been exploited to create a worm to deploy subsequent attacks. In the report, the researchers mentioned that the fact that the attackers only required the target user to view a GIF made it a very dangerous variant, in addition to an access point to other areas of the network.
According to the International Institute of Cyber Security (IICS), Microsoft corrected the vulnerability immediately, and the company is monitoring Microsoft Team deployments for any malicious activity related to this platform.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











